Securing My Infrastructure: Risk Management
This is a follow-up of my last post about how I secure my environment. If you want to read the start of the series, see at the end of this post but please do not expect me to keep this rhythm J.
Let me start with an introduction first: After my first post, I got quite some reactions – which was very good and promising. You raised quite some questions mainly about monitoring and authentication. I will answer then and would like you to keep asking – that is the only way you get an answer, actually. However, I will start with a few different themes and then come to those. Mainly, I would like to start with Risk Management and how I secure my perimeter. From there on, we can talk about monitoring and how I do the authentication piece in my environment.
So, before you actually start to talk about how to secure something, we need two things:
- What are your assets?
- What are the risks for these assets?
If I look at my environment: My assets? Well, there are a few things I would like to protect: all the photos and videos of my family, my mailbox and a few others. But really critical information is not here. However, I would not like to read somewhere that somebody broke into my network…
What is the easiest way to get a good overview of your risks? The challenge there is always to compare the business risks (including the acceptable level of risks) with the actual risks you are taking in you infrastructure. A good tool that can help you here is the Microsoft Security Assessment Tool (MSAT). We just recently released a new version of it (you can have it in multiple languages). It is a really excellent tool from my point of view to give you and overview of you needs: Where you should invest more AND where you are doing too much! It does that in two steps:
- You assess your own profile and create what we call a BRP (Business Risk Profile)
- You assess your infrastructure. There are – again – two assessments available
- Security Assessment
- An assessment against the Core Infrastructure part of our Infrastructure Optimization model
So, I did both and afterwards it is generating some reports for me how I am doing against my Business Risk Profile. You could even compare with Businesses in similar segments (is there any family out there running a similar infrastructure??).
Security Assessment
Looking at my security assessment, this is the high-level overview:
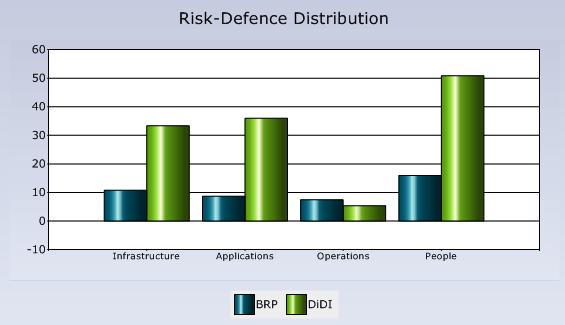
BRP: Business Risk Profile, DiDI: Defense in Depth Index
The result is not really surprising: I am doing extremely well on Infrastructure and Applications. What about Operations? Well, I do not have any standardized build for my servers and clients nor is there any formal process to test them. Overall, I am not doing well on processes at home (why should I? I am the processJ). With regards to the people: As there are not too many people on my network, they are drilled what they are allowed to do and how to behave if something bad happens. Therefore I am doing much better than I actually would have to compared to my business risk profile.
Core Infrastructure
This is a similar picture as with the Security Assessment above: I am actually very good automated (some people call that level of automation "sick") for my profile, but I am not doing too well on processes:
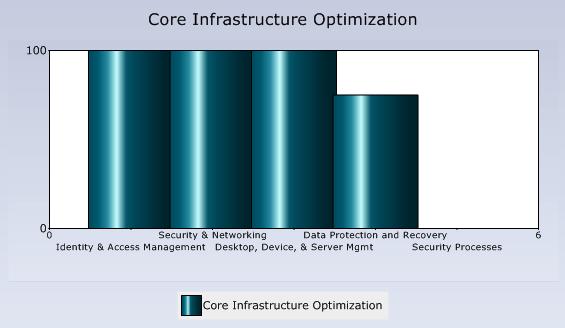
So, now I know where I am and what I have to do. The next step is looking a little bit more into my network perimeter and how I defend my network from the outside.
As always: If you have anything you would like me to answer, drop me a mail or a comment.
Roger
Other posts in this series:
Additional Information
- Risk Management Guide
- Microsoft Security Assessment Tool (MSAT):
- Security Tools