Verifying Spectre / Meltdown protections remotely
In this post we will take a look at the SpeculationControl PowerShell module that was recently released by the Microsoft Security Response Center to help with verifying Spectre / Meltdown protections.
SpeculationControl can be found on the PowerShell Gallery at the following link: https://www.powershellgallery.com/packages/SpeculationControl
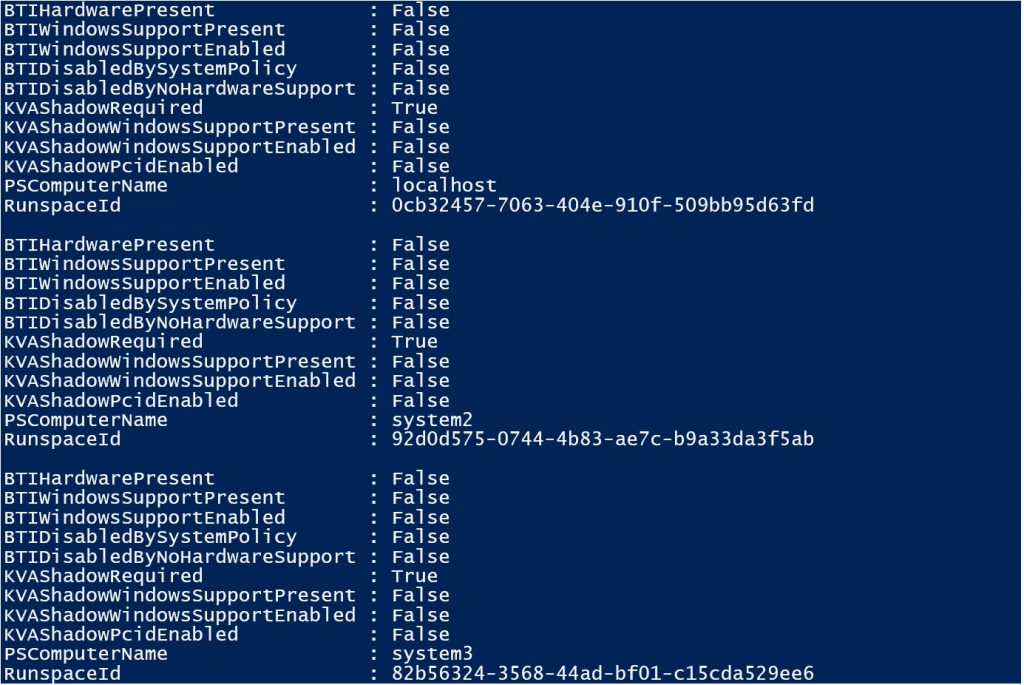
Installing this module onto a system adds a new function called Get-SpeculationControlSettings and this function can be run on a system to provide details on whether Spectre / Meltdown protections have been enabled.
What if you wanted to run this remotely against multiple systems?
To run the Get-SpeculationControlSettings function against multiple systems, see the example code below:
(Credit goes to Keith Hitchcock for his help on this)
This example only requires that you have the SpeculationControl PowerShell module installed on the system that you execute this code from. Because of the way the Get-SpeculationControlSettings function is structured, we can simply load the function remotely as part of the call to Invoke-Command.
In order to run this sample code in an environment, the only update required is the list of machines that follow -ComputerName. If you prefer to pass in a list of systems in a text file, the sample code can easily be modified to take in an input text file by utilizing the Get-Content cmdlet.
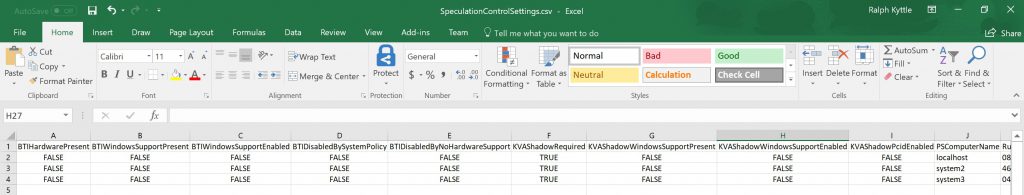
While this is nice, we can take things a step further by outputting the results to CSV which will make things easier to consume, especially as we start adding more systems to the list.
Example code below:
This is now easier to digest, and we can sort and apply filters as needed.
At this point, we have taken the SpeculationControl PowerShell module and run it through a few examples that take it beyond local execution and help us review remote systems in an environment.
Next, we will take a look at using the SpeculationControl PowerShell module along with another PowerShell module called DSCEA. DSCEA provides configuration testing and reporting capabilities for Windows based systems, and we will take a look at how we can use it to gain some intelligence from the data that we are able to gather remotely.
For example, let’s say your management team is looking for numbers, specifically how many machines exist in your environment that have not yet been patched for the CVE-2017-5754 rogue data cache load (Meltdown) vulnerability.
While we could ask someone to look through the CSV file and compare systems across multiple columns, I’d rather have a computer provide me with this information.
There are a few points to make though before we go down the DSCEA path. DSCEA requires a minimum PowerShell version of 5.0, with 5.1 being recommended. Also, DSCEA would require that the SpeculationControl PowerShell module be installed on all endpoints that are being scanned. While there are some easy ways to handle this which include pushing out a DSC configuration that utilizes the DSC File resource, or just a file copy script, for this example I am including the entire Get-SpeculationControlSettings function as a part of my custom DSC configuration. This just makes this a whole lot easier to demonstrate, but it does require code updates if there are updates to the SpeculationControl PowerShell module in the future.
This section will assume you have downloaded DSCEA and have some knowledge of its usage. If you don’t, click here to learn more.
I have copied the DSC configuration at the end of this post that will be used to verify if systems have been patched for Meltdown. You will use this configuration to build a MOF file that you will use with DSCEA to scan systems to see if they have the proper updates and configurations enabled.
The configuration comes with the following logic defined to determine if a system has been properly configured in regards to Meltdown:
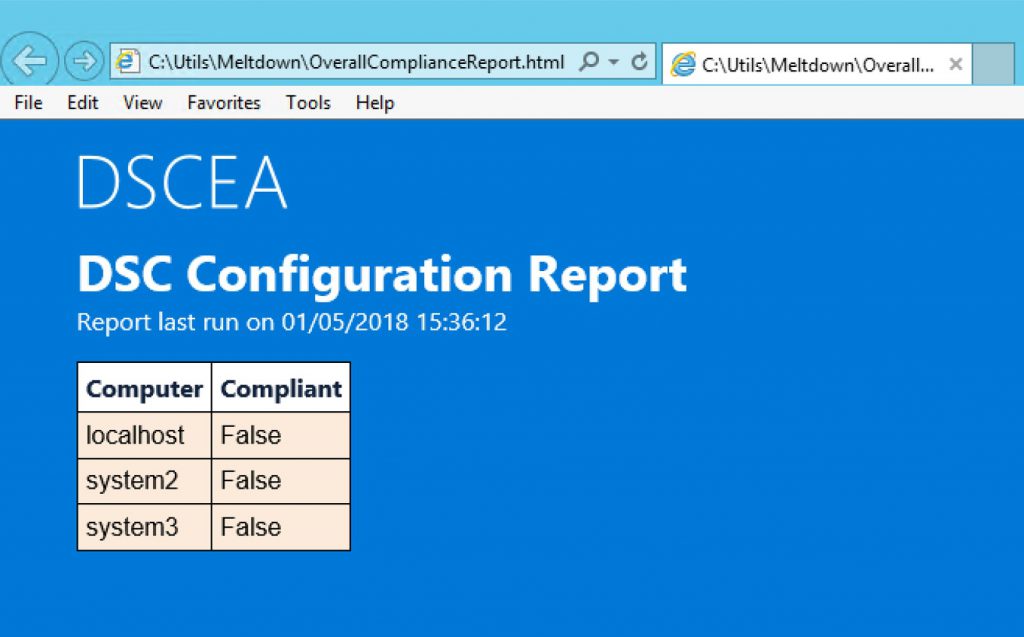
DSCEA HTML Report Example
In this case, all 3 systems are non-compliant, meaning they need to be reviewed to get the proper updates and settings applied.
DSC Configuration