Introduction to Code Signing and Sideloading for Windows 8 Applications with System Center Configuration Manager
This is a guest post from Martin Booth, a Senior Technical Product Manager in the System Center Product Team. I asked Martin to write about Windows Code Signing and Sideloading, a topic that many folks have questions about and would like to better understand. This post will complement my series on Mobile Application Delivery with System Center Configuration Manager 2012 R2 and Windows Intune Series.
-----------------------------------------------------------------------------------------------------------------
Hi, I’m Martin Booth, a Technical Product Manager in the Server & Tools Marketing Group at Microsoft. I look after the enterprise client management products, namely System Center Configuration Manager and Windows Intune.
In this blog article, I’ll be running through the concepts behind sideloading and code signing of Windows Store line of business applications, and the impact this has on managing Windows 8.1 devices using OMA-DM with System Center Configuration Manager 2012 R2 and Windows Intune.
What is sideloading?
Windows Store apps are the new type of (“modern”) application that runs on Windows 8.1 and Windows 8 devices. These apps are based on the Windows Runtime API and differ from traditional desktop apps in their design and in the way users can interact with them on Windows 8.1 devices and Windows 8 devices. To learn more about Windows Store apps, see What is a Windows Store App? .
Typically, Windows Store apps are available only through the Windows Store. You can submit LOB Windows Store apps to the Windows Store and make them available outside of your enterprise. However, you can also develop Windows Store apps for use only within your enterprise and add them to Windows devices you manage through a process we call sideloading. Sideloaded apps do not have to be certified by or installed through the Windows Store.
Apps that aren't signed by Windows Store can only be installed on sideloading-enabled devices. Within the enterprise, sideloading is enabled on Windows 8.1 Enterprise, Windows 8 Enterprise, Windows Server 2012 R2 or Windows Server 2012 by joining the computer to a domain. To enable sideloading on a Windows 8.1 Enterprise and Windows 8 Enterprise computer that is not domain-joined or on any Windows 8.1 Pro or Windows 8 Pro computer or on a Windows RT device, you must use a sideloading product activation key. For more information about acquiring sideloading product activation keys, see Microsoft Volume Licensing.
LOB Windows Store apps can be sideloaded onto a PC in the enterprise through scripts at runtime on a per-user basis. They can also be provisioned in an image by the enterprise so that the app is registered to each new user profile that's created on the PC. However, for “Bring Your Own Device” scenarios, where the device is not domain joined or running an enterprise image, you can use System Center Configuration Manager 2012 R2 with Windows Intune to enable sideloading and provide a catalog of corporate applications to the user.
There are several good blogs and articles that go in more details on what sideloading is and how to use it in environments without Configuration Manager:
· Sideloading Windows 8 and Windows RT apps: Requirements
Configuring sideloading keys in Configuration Manager 2012 R2
There are two places you can add the sideloading keys in to Configuration Manager 2012 R2; either during the initial wizard set up of the Windows Intune Subscription or directly in the “Windows Sideloading Keys” node in the administration console.
When first configuring the Windows Intune Subscription in Configuration Manager 2012 R2, you get the option to enable each of the platforms you wish to support. When enabling Windows as a managed platform, there is the option to add the sideloading keys then.
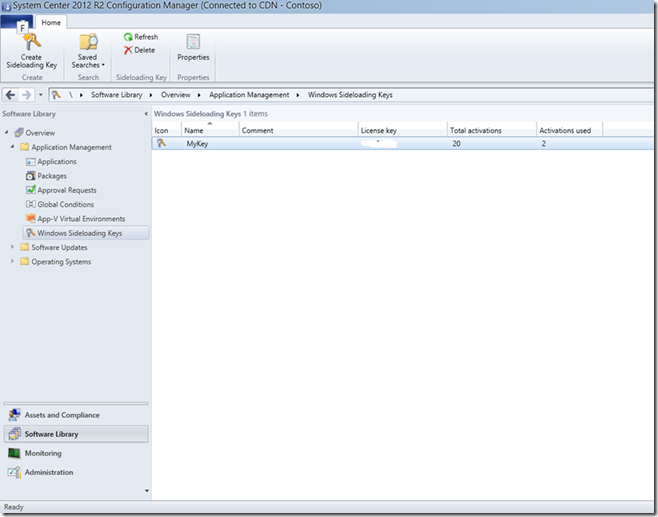
Alternatively, you can add the sideloading keys before or after setting up the Windows Intune Subscription. The keys can be entered in the console under “Software Library” -> “Application Management” -> “Windows Sideloading Keys”.
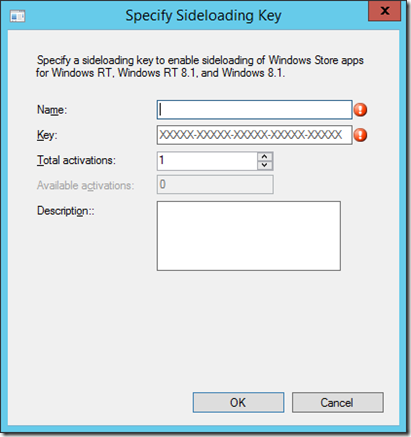
To enter a new key, you just need to specify a friendly name, the key, the number of activations purchased, and (optionally) a comment or description.
Once the keys are loaded, they will be allocated to devices as the devices enroll. When a key has reached its total number of available activations Configuration Manager will move on to allocating from the next key in the list.
Monitoring sideloading keys
It is important to key an eye on the sideloading keys. If all the available activations are used up, then devices will still enroll but newly enrolled devices will not be able to sideload applications. Thankfully Configuration Manager 2012 R2 provides a number of tools to help here. First, you will have seen in the screenshot above that the number of available activations is shown clearly in the console.
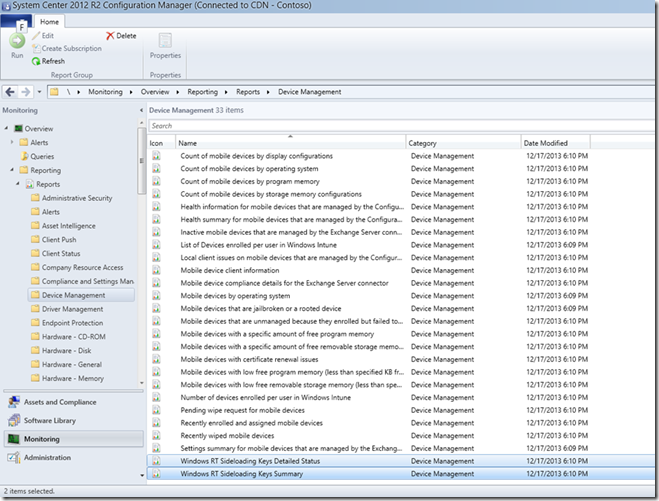
In additional there are a couple of reports available through the built-in SQL Server Reporting Services capability that provide a summary or detailed view of the usage of sideloading keys. Of course, these reports can be set up with a schedule to be regularly generated and the output can be a file, sent by email, or embedded in a SharePoint site.
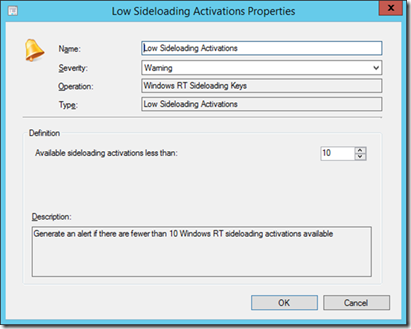
There is also a built-in alert that is preconfigured to alert the administrator if the number of available sideloading keys goes below 10. You can of course tweak this to suit your needs.
Background on app signing for Windows 8
The security model of Windows 8 requires that applications are code signed by an authority that is trusted by the device. For applications acquired through the Windows Store, the required trusted certificates are already present in Windows 8. For enterprise applications, this means that you will need to either sign your applications with a certificate from an authority already trusted by Windows, or you can sign using your own PKI and distribute the code-signing certificate via Configuration Manager.
I would recommend using your own code signing certificate, as this enables you to control which devices can run your application. Only those devices with your certificate authority will be able to install and run the application. If you are controlling deployment of that certificate, you will be restricting the devices capable of running your application to just your managed devices.
So, how do I sign my apps? Well, best bet would be first to review the blog article that The Deployment Guys posted (Link). There is plenty of information in that article on the requirements for setting up your own PKI for code signing, plus how to package and sign the application within Visual Studio.
There is also some deeper information in on these pages:
Setting up the code signing certificate in Configuration Manager 2012 R2
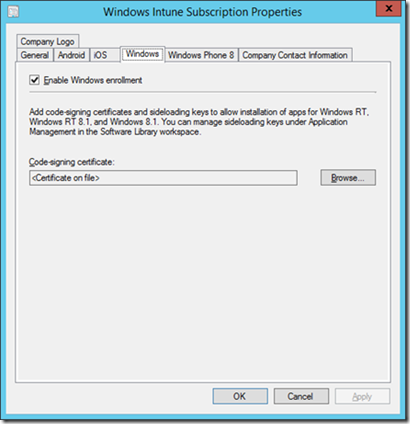
If you have signed your applications using your own PKI infrastructure, you will need to set up Configuration Manager 2012 R2 to deploy the code-signing certificate for that authority to Windows devices as they enroll for management. The simplest way of doing this is to supply that certificate on the Windows tab of the Windows Intune Subscription properties:
For more information on configuring the Windows Intune subscription properties, check out this TechNet Library article: https://technet.microsoft.com/en-us/library/jj884158.aspx
A good follow up question is “What happens when my certificate or my app signing expires?” As detailed on this page, https://technet.microsoft.com/en-us/library/dn469410.aspx, the app will no longer be downloadable. If the certificate authority is still valid, but the signing of the app expired you can resign the app and published it to supersede the existing app. If the code signing cert itself has expired, you can resign and publish the apps and simply update the Windows Intune Subscription properties with the new code-signing certificate.
Summary
Hopefully this article has brought some insight in to how Windows uses sideloading keys and application signing to improve security and manageability, and how Configuration Manager 2012 R2 with Windows Intune can enable application deployment within this model. For more information on the mobile application deployment process itself, check out Jeff Buller’s blog series on Mobile Application Delivery with System Center Configuration Manager 2012 R2 and Windows Intune.
Playing with keys and code signing can seem daunting at first, but with the details covered above you should be able to understand more about the process and how to use it to help protect corporate applications and data.
Martin Booth