Microsoft SIR 11 Finds Social Engineering is Leading Cause of Malware
This week Microsoft’s Trustworthy Computing released the 11th edition of the Microsoft Security Intelligence Report volume 11 (SIRv11). Among the most interesting findings is that social-engineering
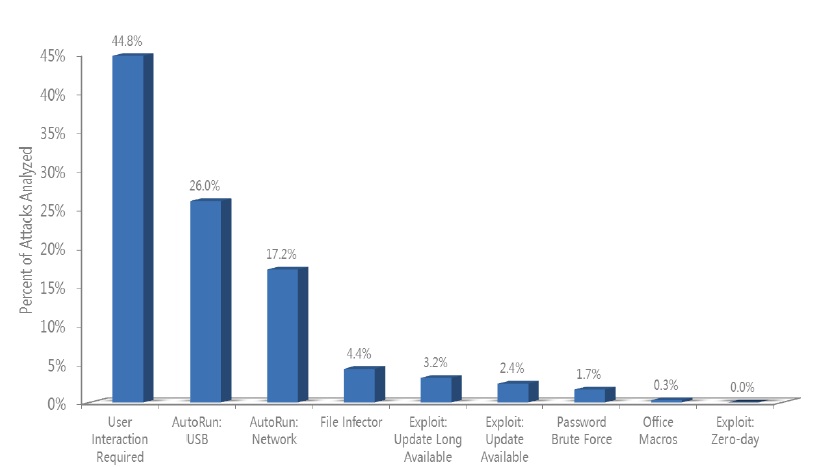
techniques cause nearly half (45 percent) of all malware propagation in the first half of 2011:
For the analysis, threats detected by the Malicious Software Removal Tool (MSRT) during the first half of 2011 (1H11) were classified by the means of propagation that each threat family has been documented to use to infect victims. If the threat was reported as using multiple vectors to infect users, then the number of infections reported by the MSRT for that family were divided and attributed equally to each vector. The figure on the next page shows the results of that analysis.
The different malware threat propagation methods referenced in the figure are described as follows:
User Interaction Required. When a user has to perform an action for the computer to be compromised. In this usage, “action” means an intentional action that is in some way distinguished from typical use of the computer.
AutoRun: USB. The threat takes advantage of the AutoRun feature in Windows to infect USB storage devices and other removable volumes.
AutoRun: Network. The threat takes advantage of the AutoRun feature to infect network volumes mapped to drive letters.
File Infector. The threat spreads by modifying files, often with .exe or .scr extensions, by rewriting or overwriting some code segments.
Exploit: Update Long Available. The vendor released a security update to address the vulnerability more than a year before the attack.
Exploit: Update Available. The vendor released a security update to address the vulnerability less than a year before the attack.
Exploit: Zero-day. The vendor had not released a security update to address the vulnerability at the time of the attack.
Password Brute Force. The threat spreads by attempting brute force password attacks on available volumes, as with the net use command.
Office Macros. The threat spreads by infecting Microsoft Office documents with malicious Visual Basic® for Applications (VBA) macros.