Farm Communication in SharePoint
The information provided in this article is available at Plan security hardening for SharePoint 2013 (TechNet) and SharePoint 2013 Ports, Proxies and Protocols - An Overview of Farm Communications
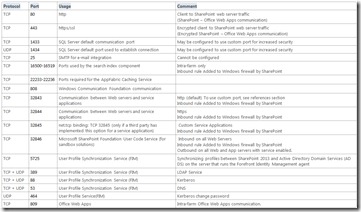
See this table for commonly used ports and protocols in farm communication.
Service Application Communication
By default, communication between Web servers and service applications within a farm takes place by using HTTP with a binding to TCP 32843. When you publish a service application, you can select either HTTP or HTTPS with the following bindings:
HTTP binding: TCP 32843
HTTPS binding: TCP 32844
Additionally, third parties that develop service applications can implement a third choice:
net.tcp binding: TCP 32845
You can change the protocol and port binding for each service application. On the Service Applications page in Central Administration, select the service application, and then click Publish.
The HTTP/HTTPS/net.tcp bindings can also be viewed and changed using the Get-SPServiceHostConfig and Set-SPServiceHostConfig PowerShell cmdlets. Communication between service applications and SQL Server takes place over the standard SQL Server ports or the ports that you configure for SQL Server communication. See Service Application Communication for more information.
Output of Get-SPServiceHostConfig
HttpPort : 32843
HttpsPort : 32844
NetTcpPort : 32845
SslCertificateStoreName : SharePoint
SslCertificateFindType : FindBySubjectDistinguishedName
SslCertificateFindValue : CN=SharePoint Services, OU=SharePoint, O=Contoso, C=IC
User Profile Service Hardening Requirements
The User Profile service application uses the Forefront Identity Management agent to synchronize profiles between SharePoint 2013 and Active Directory or a Lightweight Directory Access Protocol (LDAP) directory service. The Forefront Identity Management agent is installed on all servers in a SharePoint farm, but is only required on the server that is set up to synchronize with the directory store.
The Forefront Identity Management agent includes the following two services that must remain enabled on the server that is set up to crawl Active Directory or another directory store:
- Forefront Identity Manager service
- Forefront Identity Manager Synchronization service
Additionally, TCP 5725 must be open on the server that runs the Forefront Identity Management agent and is set up to crawl a directory store. In Active Directory environments, the following ports must remain open for communication between the SharePoint 2013 server that synchronizes with the directory store and the server that is running Active Directory:
- TCP & UDP 389 (LDAP service)
- TCP & UDP 88 (Kerberos)
- TCP & UDP 53 (DNS)
- UDP 464 (Kerberos Change Password)
For more information about hardening requirements for the Forefront Identity Management agent, including port requirements for other directory types, see Management Agent Communication Ports, Rights, and Permissions (https://go.microsoft.com/fwlink/p/?LinkId=186832).
References
Plan security hardening for SharePoint 2013 https://technet.microsoft.com/en-us/library/cc262849.aspx
Learn about security hardening for SharePoint web server, application server, and database server roles (blocking the standard SQL Server ports), including specific hardening requirements for ports, protocols, and services.
- Security planning for SharePoint 2013 farms https://technet.microsoft.com/en-us/library/hh377941.aspx
The articles and resources on this page provide information about how to plan SharePoint 2013 security for server farms.
- Configure SQL Server security for SharePoint 2013 environments https://technet.microsoft.com/en-us/library/ff607733.aspx
When you install SQL Server, the default settings help to provide a safe database. In addition, you can use SQL Server tools and Windows Firewall to add additional security to SQL Server for SharePoint 2013 environments. Learn how to improve the security of SQL Server for SharePoint 2013 environments.
- TCP/IP Communications (Windows Server AppFabric Caching) https://msdn.microsoft.com/en-us/library/ee790914(v=azure.10).aspx