Configuring Claims and Forms based Authentication for use with an ASP.NET Membership Provider in SharePoint 2010
The steps included in this post are:
- Configure SQL for membership store
- Create a new Web Application with 'Claims-based authentication'
- Modify the Web.config files
a. Configure the web.config of the web application to use ASP.Net membership provider
b. Configure Central Admin to use the ASP.Net membership provider
c. Configure the Security Token Service (STS) application) - Add A User Policy
- Login
- For the purpose of this article, I have used the following configuration:
Web Application Name - SharePoint – SQLMemberWeb80
Web app URL - https://SQLMemberWeb
Membership Provider - SQL-Membership
Role Manager - SQL-RoleManager
SQL Instance Name - Skylark
Connection String name - SQLConnString
ASP Net DB - SQL-Auth
Create a database for ASP.Net Membership and Role Provider
- Microsoft ships providers that work with a SQL Server database. There is a tool called “aspnet_regsql” that can be used to configure a database to use ASP.NET application services. This is located at ‘C:\Windows\Microsoft.NET\Framework\v2.0.50727’.
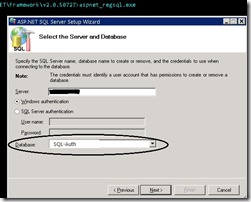
Here are the steps:- Browse to "C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727".
- Used the command 'aspnet_regsql' to launch the ASP.NET SQL Server Setup Wizard.
- Choose 'Configure SQL Server for application services' (the default choice) on the 'Select a Setup Option' screen and click Next.
- You can choose an existing database to add the membership elements to, or you can type in a new name and the database will be created for you.
- Specify the SQL Server name (Instance Name), database name to create (in this case, it is 'SQL-Auth’).
- Wait for the database to be created successfully.- Microsoft ships providers that work with a SQL Server database. There is a tool called “aspnet_regsql” that can be used to configure a database to use ASP.NET application services. This is located at ‘C:\Windows\Microsoft.NET\Framework\v2.0.50727’.
Create a new Web Application with 'Claims-based authentication' Create a new web application and configure it for Mixed-mode (Windows + SQL authentication) authentication.
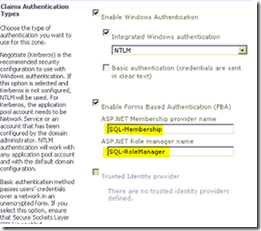
**Provisioning a Claims based web application using UI** 1. From the Central Administration (CA) site, go to 'Application Management'. 2. Click on 'Manage Web Applications' link. 3. From the Ribbon, click on the ’New’ button to create a new web application. [![clip\_image001\[6\]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/77/19/metablogapi/2678.clip_image0016_thumb_362219B1.png "clip_image001[6]")](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/77/19/metablogapi/1106.clip_image0016_52134EA9.png) 4. Make sure to select the 'Claims Based Authentication’5. In the Authentication Type section, select Enable Windows Authentication and select NTLM or Kerberos.
6. In the Authentication Type section, select “ Enable Forms Based Authentication (FBA)' ” .
7. Enter in the ASP.NET Membership provider and Role manager name as 'SQL-membership' and 'SQL-Rolemanager'
respectively.Click on “OK” button to create the web application.
Enable Claims-based authentication on an existing web application
When you provision a web application in SharePoint 2010, you get an option to enable Claims-based authentication. However, after the provisioning, there is no option in the GUI to turn it on. This is where PowerShell comes in. We can update the authentication method from classic to claims-based authentication using the lines below:
$WebApp = Get-SPWebApplication "https://WebAppURL"
$WebApp.UserClaimsAuthentication = "True"
$WebApp.Update()
3. Modify the Web.config files (Forms Web Application, Central Admin and Security Token
Service)
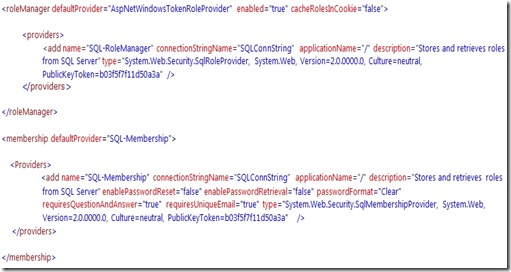
- Modify web.config of FBA web application Add connection String:
Connection String has to be added after </SharePoint> but before the <system.web> element.
Add membership Provider and Role Manager:
- Modify web.config of the Central Administration web application. Add connection String:
- Add membership Provider and Role Manager:
- Modify web.config of
Security Token Service (STS)
Note: You can locate the STS web.config from %Programfiles%\common files\Microsoft Shared\web server extensions\14\WebServices\SecurityToken
Add connection String:
Add membership Provider and Role Manager:
The preceding entry has to be added before the </configuration> element. Save and close the Web.Config file.
After adding the preceding entry, save and close the Web.Config file.
- If this does not work, changed the web.config of the STS as follows:
- Save and close the Web.Config file.
4. Add A User Policy
In case you have already created the users, you can add them to the web application. If not, we need to create the users who will be a
part of the membership database.To begin, we will create the connection string and the providers (Role Provider and Membership Provider). Here are the steps:
- Open Internet Information Services (IIS) manager on the server
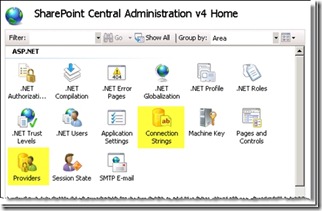
- Expand the 'Sites' node and select the SharePoint Central Administration v4 site.
- On the Home Page, the two main options that we need are "Connection Strings" and "Providers" as highlighted below:
- Open the Connection Strings Page.
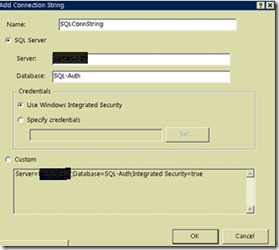
- Under Actions menu on the right, select Add.. to create a new connection string.
- Provide the details for the membership database for the new connection string
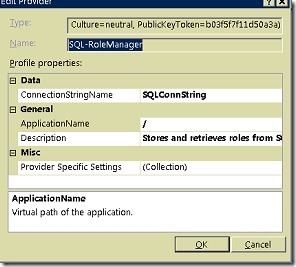
Add a Role Provider
- Highlight the web application in IIS.
- Set feature to .NET Roles
- Click Add… in the Actions pane to add a new role provider.
- Name it 'SQL-Rolemanager'
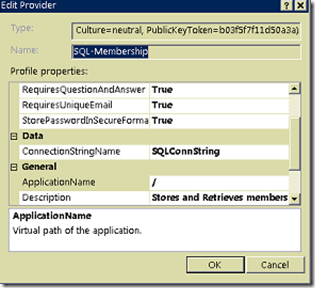
Add a Membership Provider
- Highlight the web application in IIS.
- Set feature to .NET Users.
- Click Add.. in the Actions pane to add a new membership provider
- Name it 'SQL-Membership'
Add Users to the Web Application
- Open Internet Information Services (IIS) manager on the server
- Expand the 'Sites' node and select the newly created web application
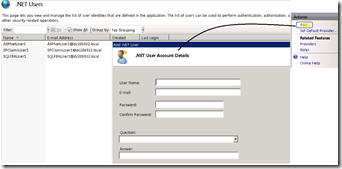
- Create some users by using the '.Net Users' feature.
- When prompted with an error stating the feature cannot be used because the default provider is not a trusted provider, click OK.
- In the Actions pane, click Set Default Provider.
- In the Edit .NET Users Settings dialog box, note that the default provider configured in SharePoint Server 2010 is "i". In the Default Provider list, click SQL-Membership, and then click OK.
- In the Actions pane, click Add..
- When prompted with an error stating the default .NET Roles provider does not exist, click OK.
- In the Add .NET User dialog:
- On the .NET User Account Details page, type the appropriate values in the User Name, E-mail, Password, Confirm Password, Question, and Answer boxes, and then click Next.
- On the .NET User Roles page, click Finish.
- I named the user as 'SQLFBAUser1' and then added it to the 'SQL-Rolemanager' role provider.
- In the Actions pane, click Set Default Provider..
- In the Edit .NET Users Settings dialog box, in the Default Provider list, click 'i', and then click OK.
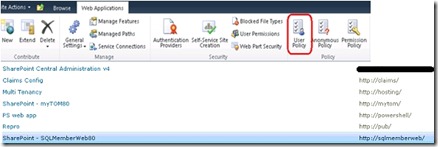
- Coming back to adding the users to the web application, browse to 'Central Administration - Applications Management - Manage Web Applications' page. and click the 'SharePoint - SQLMemberWeb80' item.
- Click on 'User Policy' in the ribbon to bring up the User Policy dialog.
- Click on the 'Add Users' link.
- You are then asked what zone to configure users for, choose “Default” and click Next.
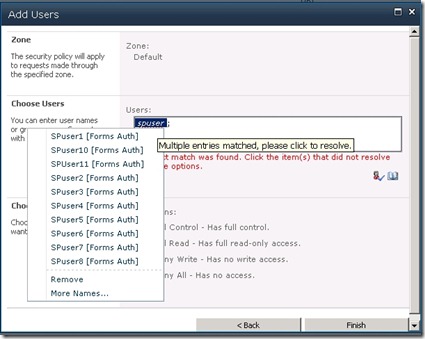
- Even if we enter a part of the user name, we should see a few suggestions in the people picker as below:
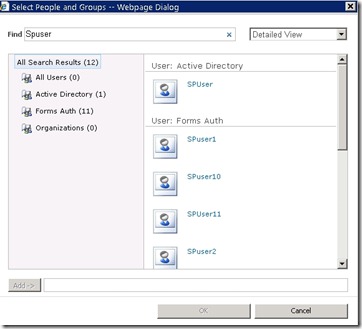
- Alternatively, click on 'Browse' (the Address book icon) which will bring up the people picker.
- This has a new interface and it allows you to search in one dialog and show matches from ALL of the directories you have configured. Type in a partial name like NT login name or account name (use whatever nomenclature you prefer here) and click the search button. You will see something like the following, showing our Forms Auth user and the user in the active directory (if there is a corresponding account)
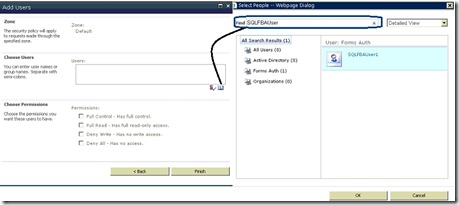
- You can also enter a user name like 'SQLFBAUser' which is limited to being a .Net user.
- Click on the find button and the user name should resolve.
- Choose the required permissions for the user and hit Finish.
That’s it!!
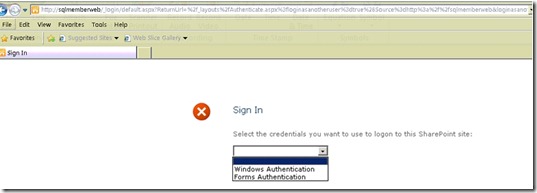
- Now that we have specified the permissions on the web application, go ahead and browse to the site as https://SQLMemberWeb.
- You should get an initial prompt to choose the kind of authentication method you want to use to access the site (i.e.) between Windows Authentication (NTLM) and/or Forms-based Authentication (ASP.NET Membership) .
- Choosing Windows Authentication will use the credentials of the currently logged on user for authentication.
- When we choose 'Forms Authentication' from the drop down, the page posts back with a standard forms login page.
- Enter the credentials of the user to which you granted the Full Control user policy and you should log into the site.
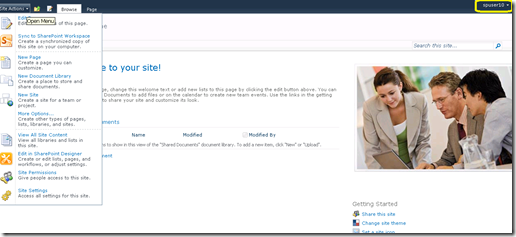
- You are now logged into your site as SPUser, with site administrator privileges (note the 'Site Actions' menu contains privileged capabilities).
Wrap up
- Create the database using 'aspnet_regsql'
- Add users and roles using the Web Site Administration Tool
- Add connection strings in the web.config for:
- Your web application
- Central Administration
- Security Token Service Application
- Add membership and role providers for:
- Your web application
- Central Administration
- Security Token Service Application
- Edit web.config for Central Administration
- Set the default provider for roles as AspNetWindowsTokenRoleProvider
- Set the default provider for membership as your new membership provider
- Add the PeoplePickerWildcards entry
- Edit web.config for the Secure Token Service Application
- Set the default provider for roles as your provider.
- Set the default provider for membership as your provider
- Add the FBA administration user to Central Administration.
Manage Users
In order to manage users in the SQL DB, you can access the users that are in the database from SharePoint and grant them permissions, but you cannot actually add roles or users to the SQL DB.
Here are a few other options which I thought could act as pointers:
1. Use the IIS manager
Open IIS manager on the server
Expand the 'Sites' node and highlight the site that has been enabled with mixed-mode authentication (NTLM and SQL provider)
In the right-hand pane, click on '.Net Users' and we will receive the following error:
This feature cannot be used because the default provider type could not be determined to check whether it is a trusted provider.
You can use this feature only when the default provider is a trusted provider. If you are a server administrator, you can make a provider a trusted provider by adding the provider type to the trusted providers list in the Administration.config file. The provider has to be strongly typed and added to the GAC (Global Assembly Cache).
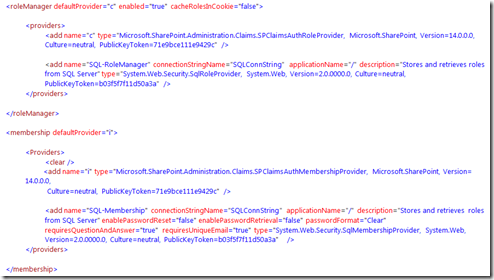
- This is expected as the default provider set in the web.config is "i" and it not added as a Trusted provider
- This is specified in the "Administration.config" file located in "C:\Windows\System32\inetsrv\Config\".
The provider can be added to the trusted assemblies by adding the following line to your <trustedProviders> section in the 'Administration.config' file
<add type=”Microsoft.SharePoint.Administration.Claims.SPClaimsAuthMembershipProvider, Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c” />
In order to use IIS Manager to manage your SQL users, you need to set the default provider to your Forms provider, like 'SQLMembership'. In order for it to work, we need to set it to the SharePoint claims provider. Go back to '.NET Users' and reset the default provider to “i” which is for the Microsoft.SharePoint.Administration.Claims.SPClaimsAuthMembershipProvider
You should also check the default Role Provider for the web application and ensure that is set to “c”. If this is set to the SQL provider that you created, you will get an unexpected error after you logon like 'Access Denied', unable to login to the site etc.
As mentioned earlier, this is a glitch/a caveat in IIS 7.
Workaround
You could work around this by creating another IIS web site, configure the same way you did for SharePoint – FBA (or whichever site you are using), and use that for managing users.
- You can add a new user to the ASP.NET Membership database by clicking on Add… on the Actions pane.
- Select a User, Email, and Password.
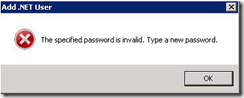
- If you have not configured the password rules, you may see an error message as follows:
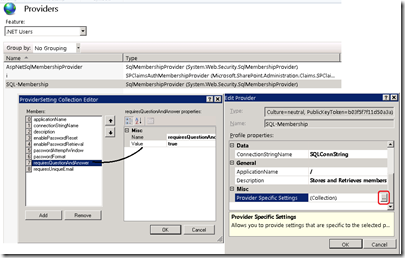
- Go back to the .NET Users Providers module from the IIS Manager console, and click on the 'Collections' button under
Misc. -> Provider Specific Settings.
- Change the configuration of the Provider setting like 'enablePasswordReset', 'requireQuestionAndAnswer' etc..
2. Membership Seeder
To create users and groups, manage passwords, etc. for forms-based authentication (FBA), you will need a tool to manage that information. Use the Membership Seeder tool. You can use it as-is for simple user and role management, or you can use the source code as basis for creating your own tool.
It allows you to create individual users or a batch of users (for scenarios such as testing). You can change passwords, delete users, and set their email addresses at account creation time. For roles, you can create and enumerate roles, add and remove users from roles (either individually or in batch), and enumerate the list of users in each role. Membership Seeder should work with any ASP.NET Membership and Role provider, so it’s valuable for testing the functionality of custom built providers as well.
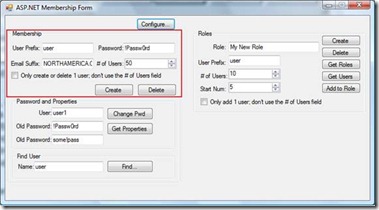
The next few screenshots will illustrate how to add some users and groups that you can use for testing your FBA implementation. Here is a screenshot of the application:
The first time you run the Membership Seeder application, click on the Configure… button. This brings up a dialog where you enter the name of the SQL Server that your SQL membership database is hosted. After you enter that information and save your changes, you need to restart the Membership Seeder application so that it will use the new server name.
NOTE: You can also manually change the settings for both the connection string as well as the provider that is used by editing the MembershipSeeder.exe config file.
To create a batch of new users for testing purposes, type a value in the User Prefix edit field, type the password you want each user to have in the Password edit field, then select the number of users you want to create in the # of Users field. When you click the Create button it will create users where the user name is the value of the User Prefix field with an incrementing number added to the end. For example, if the User Prefix field is "user" and # of Users is 2, then two users will be created and named "user1" and "user2". If you only want to add a single user and not add the numeric value to the end of the user name then check the "Only create or delete 1 user; don't use the # of Users field" checkbox. Deleting users works in a similar manner as creating users.
3. CreateUser wizard
You can make a page with the createuserwizard for user addition and there is definitely a lot that you can do with the basic wizards, but it may help, as most likely if you are using this form of authentication, users will be registering themselves for the site anyway. This wizard is a basic template for registration for your users.
4. Using Visual Studio
You can use Visual studio to open the web site that SharePoint created and go to the website menu, then ASP.NET Configuration and create more users/roles as we did with the first one. For more information on this, please visit:
- Use Web Site Administration Tool in Visual Studio: https://blogs.msdn.com/b/sridhara/archive/2010/01/15/setup-claims-using-aspnetsqlmembershipprovider.aspx
- Using the Web Site Administration Tool to Add Users: https://blogs.msdn.com/b/kaevans/archive/2010/07/09/sql-server-provider-for-claims-based-authentication-in-sharepoint-2010.aspx
Additional Information
- Implementing a Membership Provider - https://msdn.microsoft.com/en-us/library/f1kyba5e.aspx
- Introduction to Membership (MSDN) - https://msdn.microsoft.com/en-us/library/yh26yfzy.aspx (A great introductory material on ASP.NET Membership basics)
- A free 23-minute video explaining ASP.NET Membership: Understanding ASP.NET Memberships -
https://www.asp.net/security/videos/understanding-aspnet-memberships - Configure FBA in SP 2010 - https://blogs.technet.com/b/mahesm/archive/2010/04/07/configure-forms-based-authentication-fba-with-sharepoint-2010.aspx
- Setting up FBA Claims in SharePoint 2010 with Active Directory Membership Provider: https://blogs.msdn.com/b/sridhara/archive/2010/01/07/setting-up-fba-claims-in-sharepoint-2010-with-active-directory-membership-provider.aspx