Security Focus: Check the AdminSDHolder ACL - Part 2
Two weeks ago we used PowerShell to report on the AdminSDHolder ACL. We ended up with a CSV file of security principals from the ACL and a more detailed XML report.
This week, I'll show you how to quickly compare the CSV files, to see if the AdminSDHolder ACL has changed. And, here you go:
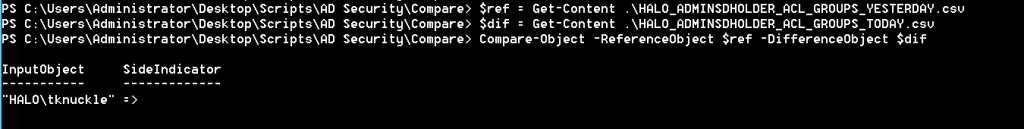
$ref is the content of yesterday's group report.
$dif is today's report.
Compare-Object let's us perform an easy comparison of these files.
Immediately, we a security principal that appears in today's file, but not yesterday's... it appears someone has added 'HALO\tknuckle' to the AdminSDHolder ACL since the report was last ran. BTW ' => ' signifies that the right hand side, i.e. the difference object (today's report), contains the discrepancy. If we have a ' <= ' side indicator then we know a principal has been removed.
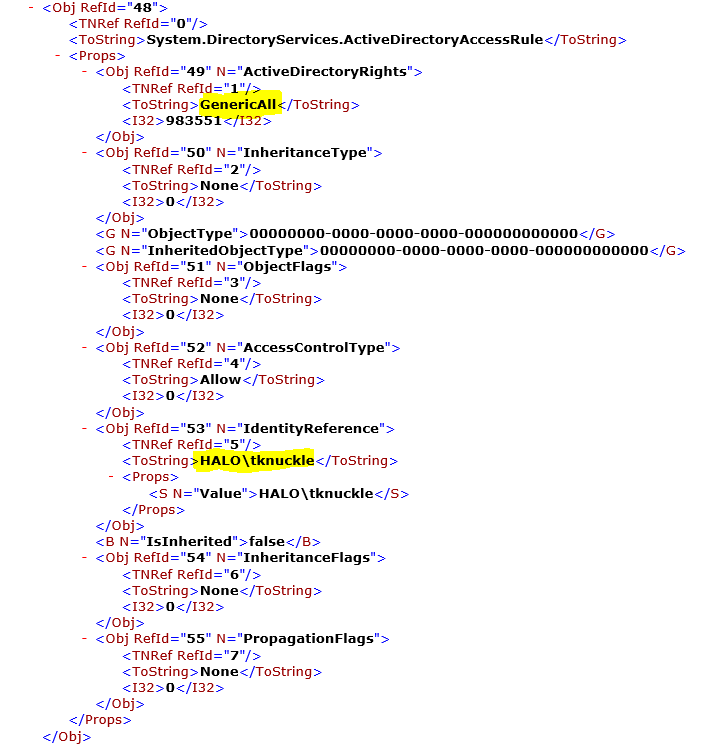
We can now search the XML report for more information.
We've found the entry for 'HALO\tknuckle' and if we look at the ActiveDirectoryRights node, we see that the principal has 'GenricalAll', i.e. full control. This means that 'HALO\tknuckle' will have full control on anything in the directory marked with the AdminCount attribute configured to 1, e.g. the Domain Admins group... not good.
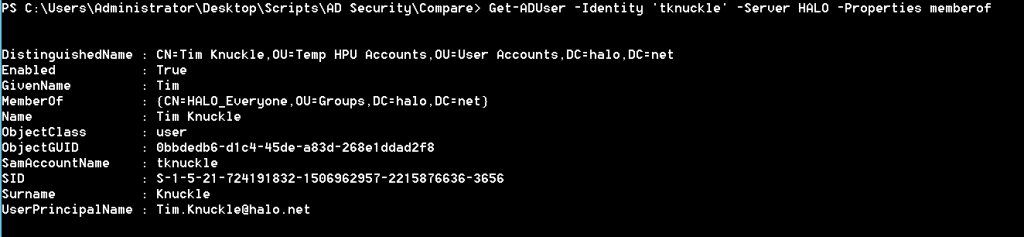
Now let's look at 'HALO\tknuckle'
Hmmm... a member of a non-privileged group. So... we have a non-privileged user with the ability to make changes to our privileged principals... not good.
Post Script
Consider automating the generation and comparison of the AdminSDHolder ACL reports.