MS16-072 - Known Issue - Use PowerShell to Check GPOs
UPDATE - 30/06/2016
Official detect and fix script released. See here:
Powershell script to adjust permissions for Authenticated Users on Group Policy
Further information:
Deploying Group Policy Security Update MS16-072 \ KB3163622
Hello,
There is a known issue with the application of particular GPOs once MS16-072 is applied. Click the following link and browse to 'Known Issues' for more information:
MS16-072: Security update for Group Policy: June 14, 2016
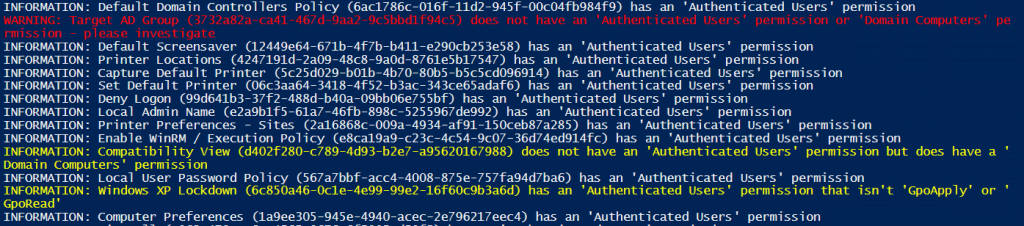
In response, I've put together the below PowerShell example to help identify GPOs, from the current domain, that might experience the issue once the update is applied. The output should be the basis for further investigation, i.e. it lists GPOs that may need the 'Authenticated Users' read permission or 'Domain Computers' read permission adding.
In the above image, a red 'WARNING:' message indicates a GPO that may experience the known issue.
There are also three types of 'INFORMATION' message*:
1) yellow - the GPO does not have an 'Authenticated Users' permission, but does contain a 'Domain Computers' permission
2) yellow - the GPO has an 'Authenticated Users' permission that is not 'GpoApply' (Read / Apply) or 'GpoRead' (Read)
3) white - the GPO has the expected 'Authenticated Users' permission.
*NB - all three 'INFORMATION:' messages can be commented out in the script to reduce the output to screen, although the first two may require further investigation
You should also take a look here:
New Group Policy Patch MS16-072– “Breaks” GP Processing Behavior
Cheers,
Mr P. Chap.
#Load GPO module
Import-Module GroupPolicy
#Get all GPOs in current domain
$GPOs = Get-GPO -All
#Check we have GPOs
if ($GPOs) {
#Loop through GPOs
foreach ($GPO in $GPOs) {
#Nullify $AuthUser & $DomComp
$AuthUser = $null
$DomComp = $null
#See if we have an Auth Users perm
$AuthUser = Get-GPPermissions -Guid $GPO.Id -TargetName "Authenticated Users" -TargetType Group -ErrorAction SilentlyContinue
#See if we have the 'Domain Computers perm
$DomComp = Get-GPPermissions -Guid $GPO.Id -TargetName "Domain Computers" -TargetType Group -ErrorAction SilentlyContinue
#Alert if we don't have an 'Authenticated Users' permission
if (-not $AuthUser) {
#Now check for 'Domain Computers' permission
if (-not $DomComp) {
Write-Host "WARNING: $($GPO.DisplayName) ($($GPO.Id)) does not have an 'Authenticated Users' permission or 'Domain Computers' permission - please investigate" -ForegroundColor Red
} #end of if (-not $DomComp)
else {
#COMMENT OUT THE BELOW LINE TO REDUCE OUTPUT!
Write-Host "INFORMATION: $($GPO.DisplayName) ($($GPO.Id)) does not have an 'Authenticated Users' permission but does have a 'Domain Computers' permission" -ForegroundColor Yellow
} #end of else (-not $DomComp)
} #end of if (-not $AuthUser)
elseif (($AuthUser.Permission -ne "GpoApply") -and ($AuthUser.Permission -ne "GpoRead")) {
#COMMENT OUT THE BELOW LINE TO REDUCE OUTPUT!
Write-Host "INFORMATION: $($GPO.DisplayName) ($($GPO.Id)) has an 'Authenticated Users' permission that isn't 'GpoApply' or 'GpoRead'" -ForegroundColor Yellow
} #end of elseif (($AuthUser.Permission -ne "GpoApply") -or ($AuthUser.Permission -ne "GpoRead"))
else {
#COMMENT OUT THE BELOW LINE TO REDUCE OUTPUT!
Write-Output "INFORMATION: $($GPO.DisplayName) ($($GPO.Id)) has an 'Authenticated Users' permission"
} #end of else (-not $AuthUser)
} #end of foreach ($GPO in $GPOs)
} #end of if ($GPOs)