Security Focus: Report on Protocol Transition
A couple of weeks ago I showed how to report on Constrained Delegation. This week, I'm going to talk about a related concept - Protocol Transition.
Protocol Transition
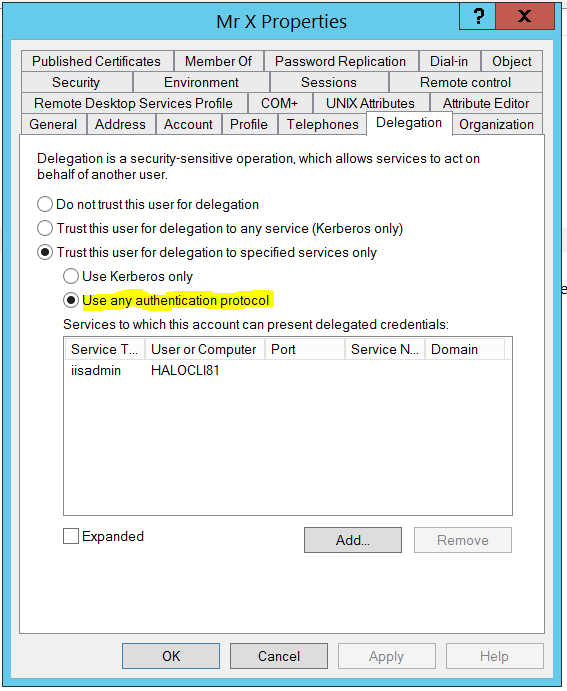
The lesser know relative of Constrained Delegation! Where you find Protocol Transition, you'll always find Constrained Delegation. Introduced in Windows Server 2003, Protocol Transition allows you to switch from a non-Kerberos authentication mechanism to Kerberos, and then use constrained delegation to pass the identity on. Why bother? It's all rather old school now, but, imagine you have an internet-facing web application that utilises form-based authentication. You then need to use Kerberos authentication and delegation to access downstream Windows servers. Well, in the previous example, it's Protocol Transition that allows you to switch from non-Windows authentication to Kerberos authentication and delegation.
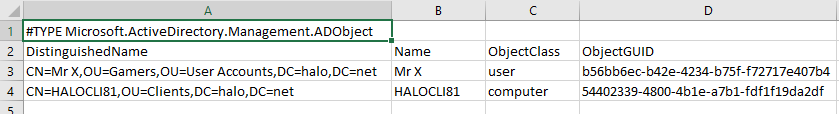
To find if you have this configured in your domain we turn to our old friend UserAccountControl. User and Computer accounts store a number of configuration settings in the their UserAccountControl property. The option that configures an account for protocol transition is stored as part of a binary mask in the 'UserAccountControl' attribute of the user or computer object. In the binary mask, each positional bit represents a different possible user account option that can be switched on or switched off. Like a light switch - when switched on, the option is active. These settings can be queried using PowerShell's 'binary And' ( -band) operator. The hexadecimal setting for protocol transition is 0x1000000 and we use -band to check that it is present (switched on) in the binary mask.
$TRUSTED_TO_AUTH_FOR_DELEGATION = 0x1000000
$Findings = Get-ADObject -Filter {UserAccountControl -band $TRUSTED_TO_AUTH_FOR_DELEGATION}
if ($Findings) {
$Findings | Export-Csv -Path ".\TRUSTED_TO_AUTH_FOR_DELEGATION.csv"
}
Here's an example of what the CSV might look like.
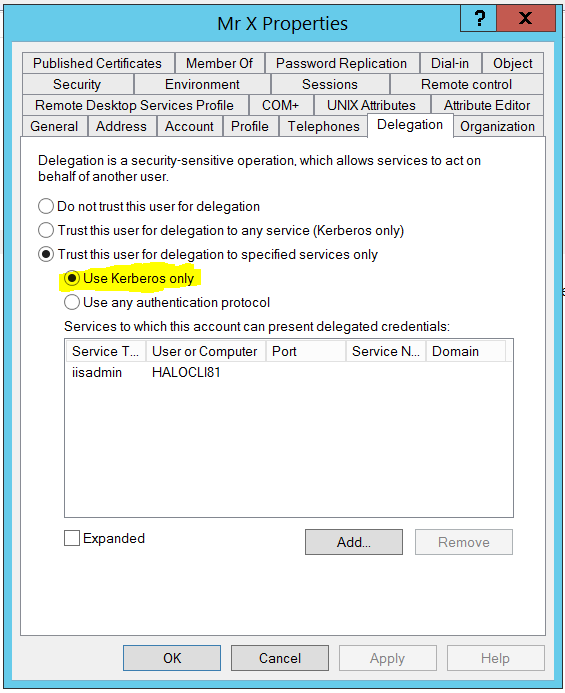
It's easy enough to turn off protocol transition with PowerShell.
Set-ADAccountControl -TrustedToAuthForDelegation $false -Identity "CN=Mr X,OU=Gamers,OU=User Accounts,DC=halo,DC=net"
And, so, we go from this:
To this: