Use PowerShell to Restrict DNS Resource Record Registration
I'm going to start with the PowerShell.
Actually, in writing that sentence, I realise I've not started with the PowerShell!
#Execute on domain controller to be 'hidden'
$DataValue = "Ldap","Gc","DcByGuid","Kdc","Dc","Rfc1510Kdc","GenericGc","Rfc1510UdpKdc","Rfc1510Kpwd","Rfc1510UdpKpwd"
New-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" -Name DnsAvoidRegisterRecords -Value $DataValue -PropertyType Multistring
Restart-Service -Name Netlogon
Got that? Good. No need for me to go on then! What? Oh, alright...
Some Context: Minimising Risk During Active Directory Upgrades
A few years back, a fellow chap called Glenn LeCheminant published a great blog post on how to perform testing, in production, of a new domain controller running a newer operating system. This was particularly pertinent at the time due to the number of security configuration changes introduced with Windows Server 2008 R2. The post recommended isolating the new DC in a 'hidden' site. This was achieved by controlling the SRV records registered by the DC: domain specific records aren't registered; only site-specific records and those required for replication and normal DNS function are kept. This creates an operational boundary - the site. Only clients placed in the site can use the DC.
Phew!
To summarise the steps:
- create a new site
- use the PowerShell above to prevent the soon-to-be-DC from registering certain SRV records
- promote the new DC to the new site (assumes Schema extension already performed)
- add a client to the site - it will use the new DC
- perform testing
Of course, restricting DNS resource record registration is not just for domain upgrade testing. You could use it to hide a disaster recovery site, or... well, the world of Active Directory is your proverbial oyster!
Some More Context: Background Reading
Restrict the DNS resource records that are updated by Netlogon
Enough Context: Get Restricting!
In the following example I’m going to ensure that only clients in the same site as my test DC, HALODC02, can access that DC, i.e. there will be only site-specific resource records registered by the DC.
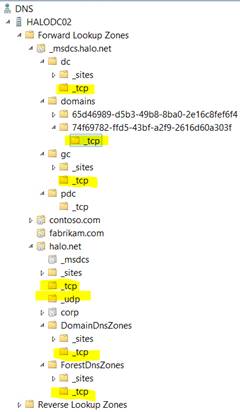
The below example shows the location of various DC-specific records to be removed from DNS:
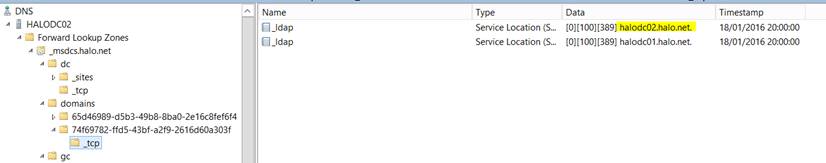
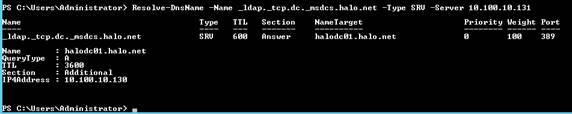
Here’s an example of an existing SRV record for the target DC:
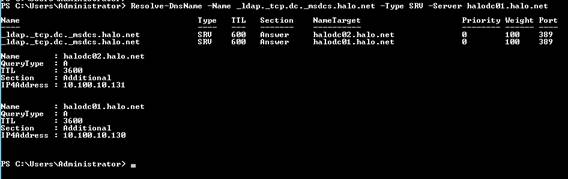
Here’s what we get when we do a lookup of domain-specific SRV records with PowerShell (two entries returned):
Resolve-DnsName -Name _ldap._tcp.dc._msdcs.halo.net -Type SRV -Server halodc01.halo.net
Now, to make the change with PowerShell:
$DataValue = "Ldap","Gc","DcByGuid","Kdc","Dc","Rfc1510Kdc","GenericGc","Rfc1510UdpKdc","Rfc1510Kpwd","Rfc1510UdpKpwd"
New-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" -Name DnsAvoidRegisterRecords -Value $DataValue -PropertyType Multistring
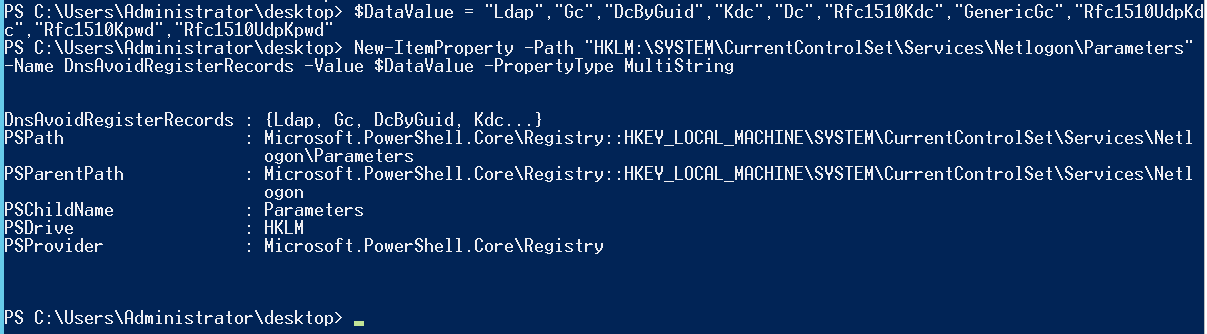
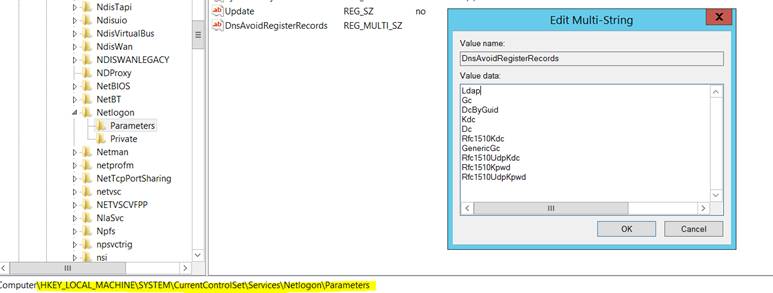
Here’s a graphical representation of what the PowerShell does. First, here's the path to the key in the registry on the DC to be hidden:
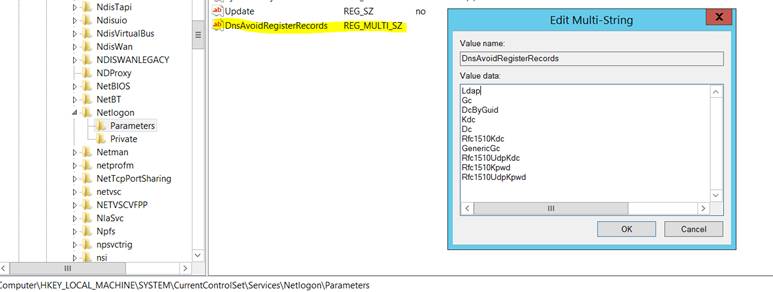
Here’s the Multi-String value to add to the registry:
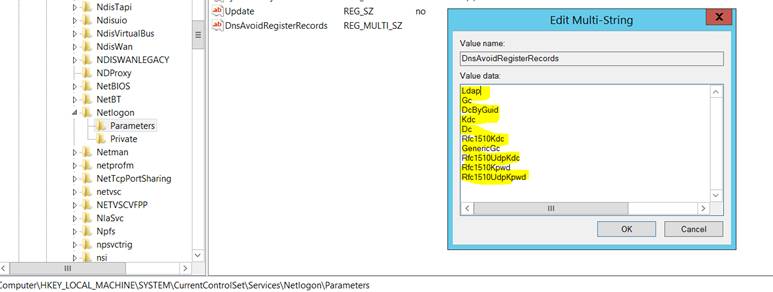
Here’s the value data for the addition:
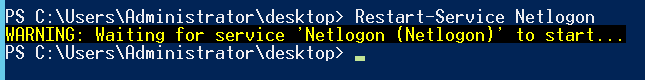
Now, restart Netlogon on the DC in question (or wait up to 15 minutes for Netlogon to auto-refresh):
Restart-Service -Name Netlogon
The sample SRV record from earlier has now gone:
Here’s what we get when we do a lookup of DCLocator, domain-specific SRV records with PowerShell (only one entry returned):
Resolve-DnsName -Name _ldap._tcp.dc._msdcs.halo.net -Type SRV -Server halodc01.halo.net
Finally, here's something a little more real-world-ready:
#Check to see if the registry entry already exists
Get-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" -Name DnsAvoidRegisterRecords -ErrorAction SilentlyContinue
#Remove the entry if it already exists
if ($?) {
Remove-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" -Name DnsAvoidRegisterRecords
}
#Create the registry key data value
$DataValue = "Ldap","Gc","DcByGuid","Kdc","Dc","Rfc1510Kdc","GenericGc","Rfc1510UdpKdc","Rfc1510Kpwd","Rfc1510UdpKpwd"
#Set the new registry key
New-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" -Name DnsAvoidRegisterRecords -Value $DataValue -PropertyType MultiString
#Restart the netlogon service
Restart-Service -Name Netlogon
#Test DNS
Resolve-DnsName -Name _ldap._tcp.dc._msdcs.halo.net -Type SRV -Server halodc01.halo.net
I guess I should now create an advanced function or something...