Security Focus: Defending PowerShell with the Anti-Malware Scan Interface (AMSI)
Naturally, I was intrigued when I heard that some new anti-virus and anti-malware capabilities were coming to PowerShell in the form of...
The Anti-Malware Scan Interface
As we know, PowerShell is an incredibly powerful administration and automation tool, but that same power can be wielded by the bad guys. In fact, PowerShell has proved to be a popular propagation and persistence mechanism. The fact that a payload can exist just in memory and can be obfuscated has made detection challenging. This is where AMSI comes into its own...
AV vendors have to emulate each script host, e.g. PowerShell, VBScript, to attempt capture the bad stuff. They have to write code to detect and undo obfuscation techniques employed, i.e. unpick the steps the bad guys use to hide their payloads. This is complicated and expensive. Wouldn't it be great if there was an interface an application could submit content to for a scan?
And, here's what AMSI allows us to do:
- evaluate code just prior to execution by the script host
- and, therefore, evaluate code after all the obfuscation has been stripped away
Furthermore, because we submit the code prior to execution by the script host it doesn't matter if it's come from on disk or just resides in memory. This overcomes another limitation of the traditional AV approach, i.e. focus on file system activity.
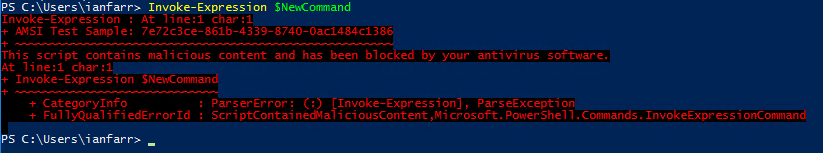
Here's a very simple example of AMSI in action. I have a script with some nasty content on a share on a compromised computer. The contents of the script have been very simply obfuscated to base64. I'm going to get the base64 string from a remote share and assign it to a variable. I'm then going to convert it back to normal and use Invoke-Expression to run the payload.
$Command = Get-Content '\\halocli1002\C$\AV_Test\AMSI2.ps1'
$NewCommand = [system.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($Command))
Invoke-Expression $NewCommand
Here's what happens:
"The script contains malicious content and has been blocked by your antivirus software."
Nice. The decoded, in-memory payload was passed to AMSI prior to execution by the script host.
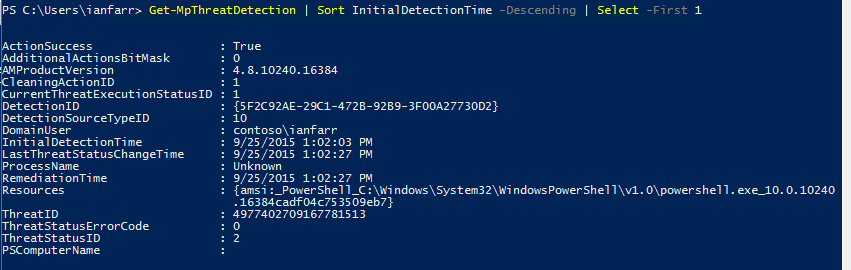
Here's the detected threat:
Note the Resources property.
PS - AMSI isn't just for PowerShell or script engines. It's designed to be used with... well, whatever wants to make use of it!