Prepopulate Passwords to RODCs with PowerShell
Hello!
The sun is shining, spring has sprung and it's nearly the weekend... life is sweet!
Today, I'm going to talk about using the AD Replication cmdlets, introduced with Windows Server 2012, to prepopulate passwords to your RODCs.
No more repadmin, no more DSA.msc... just pure, unadulterated PowerShell. Today gets better and better!
Let's begin...
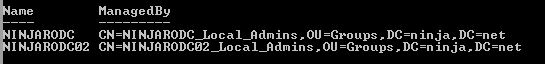
I advocate using a domain local group to grant low-privileged users the ability to administer an RODC. This delegation is stored in the ManagedBy attribute of the RODC computer object. Here's how to see which groups are configured to administer each RODC in a domain:
Get-ADDomainController -Filter {IsReadOnly -eq $True} |
ForEach-Object {Get-ADComputer -Identity $_.Name -Property ManagedBy} |
Format-Table Name,ManagedBy -AutoSize
This is pretty simple stuff - each retrieved RODC is piped into the Get-ADComputer cmdlet with an additional property request for ManagedBy. The output is then filtered:
Wouldn't it be nice to enumerate the members of those groups and then prepopulate their passwords to the associated RODC? Well, I certainly think so!
Here's how:
$RODCs = Get-ADDomainController -Filter {IsReadOnly -eq $True}
foreach ($RODC in $RODCs) {
$GroupDN = Get-ADComputer -Identity $RODC.Name -Property ManagedBy
Get-ADGroupMember -Identity $GroupDN.ManagedBy -Recursive |
ForEach-Object {
Get-ADObject -Identity $_.distinguishedName |
Sync-ADObject -Destination $RODC.Name -PasswordOnly -PassThru
} #end of ForEach-Object
} #end of foreach ($RODC in $RODCs)
This time we store the RODCs found in the $RODCs array.
We then loop through that array with foreach.
The results of the Get-ADComputer command are stored in $GroupDN.
The computer ManagedBy property is used as the Get-ADGroupMember identity using this notation - $GroupDN.ManagedBy.
We then get the AD object for each group member by referencing their DistinguishedName.
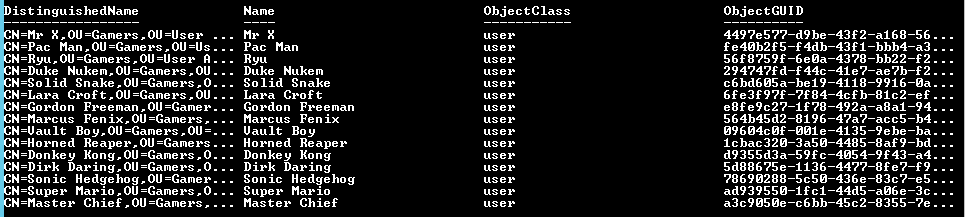
This is piped into Sync-ADObject, one of the AD replication cmdlets. The Destination parameter is the current RODC - $RODC.Name . The PasswordOnly parameter processes the synchronisation of the group member's password to the RODC.
Finally, as I have the PassThru parameter included, this is what my output looks like:
Why is prepopulating passwords important? Without access to an RWDC, an RODC is unable to authenticate users or computers whose passwords aren't already stored on the RODC.
Here's a scenario:
- a RODC becomes isolated (unable to communicate with a RWDC)
- a delegated admin needs to do some work on the isolated RODC
- the delegated admin has never previously logged on to the RODC
- the delegated admin's password has never been prepopulated
In this scenario, the delegated admin would not be able to get onto the RODC until connectivity with a RWDC is resumed. If the admin's password had been prepopulated then they could have happily performed their work! Happy admins -eq happy RODCs!
Finally, take a look at my Sync-ADRodcManagedByPassword function.
TTFN