RSA keys under 1024 bits are blocked
Public key based cryptographic algorithms strength is determined based on the time taken to derive the private key using brute force methods. The algorithm is deemed to be strong enough when the time required to derive private key is prohibitive enough using the computing power at disposal. The threat landscape continues to evolve. As such, we are further hardening our criteria for the RSA algorithm with key length less than 1024 bits.
To further reduce the risk of unauthorized exposure of sensitive information, Microsoft has created a software update that will be released in August 2012 for the following operating systems: Windows XP, Windows Server 2003, Windows Server 2003 R2, Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2. This update will block the use of cryptographic keys that are less than 1024 bits.
Some issues that you may encounter after applying this update may include:
- Error messages when browsing to web sites that have SSL certificates with keys that are less than 1024 bits
- Problems enrolling for certificates when a certificate request attempts to utilize a key that is less than 1024 bits
- Creating or consuming email (S/MIME) messages that utilize less than 1024 bit keys for signatures or encryption
- Installing Active X controls that were signed with less than 1024 bit signatures
- Installing applications that were signed with less than 1024 bit signatures (unless they were signed prior to January 1, 2010, which will not be blocked by default).
To prepare for this update, you should determine whether your organization is currently using keys less than 1024 bits. If it is, then you should take steps to update your cryptographic settings such that keys under 1024 bits are not in use.
- The security advisory is located at https://technet.microsoft.com/security/advisory/2661254.
- The KB article is available at https://support.microsoft.com/kb/2661254.
Certificate Chain Build Block of Keys under 1024 Bits
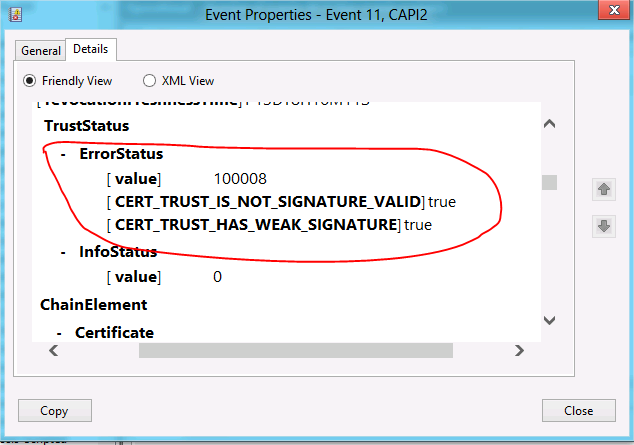
The Crypto API builds a certificate trust chain and validates that chain using time validity, certificate revocation, and certificate policies (such as intended purposes). Once the update is applied, during chain building there is an additional check to ensure that no certificate in the chain has key length less than 1024 bits). Chain building is done using the CertGetCertificateChain function. If a key chain building issue is encountered with such a certificate, then the errors produced are as follows:
Event 11, CAPI2
• CERT_TRUST_IS_NOT_SIGNATURE_VALID
• CERT_TRUST_HAS_WEAK_SIGNATURE
Working CSPs that Default to Allow Minimum 512 Bit Keys
There are three cryptographic service providers (CSPs) that default
to allow minimum 512 bit keys in Windows Server 2008 R2:
- Microsoft Base Cryptographic Provider v1.0 (RSA)
- Microsoft Base DSS and Diffie-Hellman
Cryptographic Provider (DH) - Microsoft DH SChannel Cryptographic Provider
(DH)
When working with V2 certificate templates, if you do not specify the key size, then the default CSP with default key size will be used to generate the key. If the default CSP is one of the above 3 CSPs on the client box, then the generated key will be under 1024 bits. The CA which has been updated with weak key protection will reject such request. As a result, we recommended that you do the following:
- Configure the template to specify the cryptographic providers that you want to be utilized by selecting Requests must use on of the following
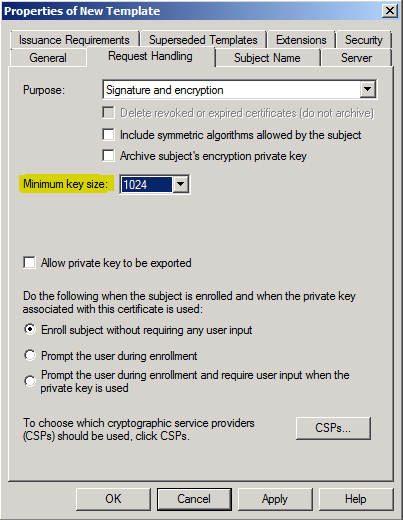
providers. - Configure the Minimum key size to 1024 bit or larger.
When using certreq, ensure that you specify a 1024 bit or larger key in the INF file. For additional information, see Best Practice for Configuring Certificate Template Cryptography.
Discovering Usage of Keys under 1024 Bits in Certificate Templates
You can run the following query on your Certification Authorities (CAs) in order to discover certificate templates that are utilizing
keys under 1024 bits:
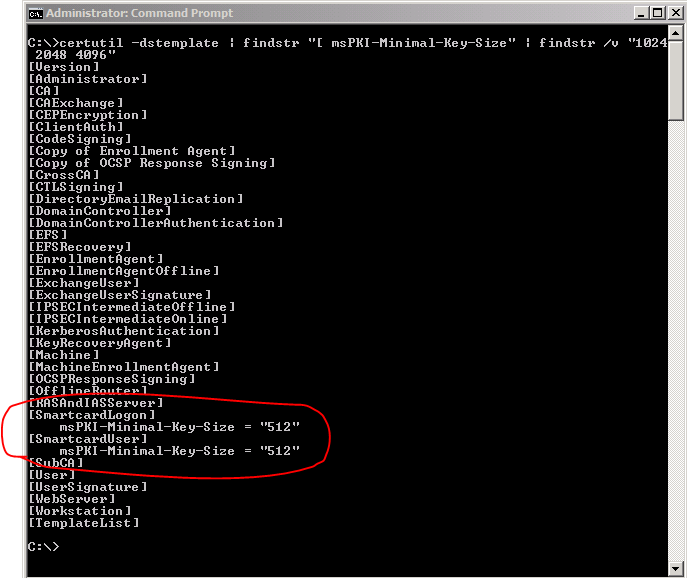
Certutil -dstemplate | findstr "[ msPKI-Minimal-Key-Size"| findstr /v "1024 2048 4096"
Note: The command should be run in each forest in your organization.
If you run this query, templates that utilize keys that are smaller than 1024 bits will be shown with their key size. The following figure illustrates that two of the built-in templates SmartcardLogon and SmartcardUser templates have default key lengths that have minimum key sizes of 512 bits. You may also discover other templates that were duplicated with minimum key sizes of less than 1024 bits.
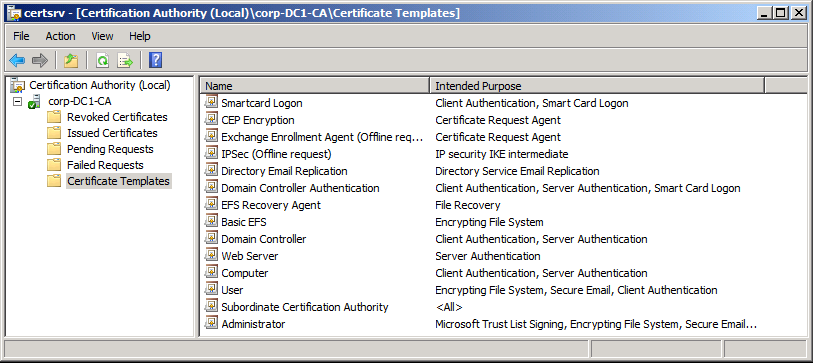
For each template you discover that allow less than 1024 bit keys, you should determine whether it is available to issue certificates as shown in the Certificate Templates section of the Certification Authority console.
For these templates, you should consider increasing the Minimum key size to a setting of at least 1024 (assuming the devices to which these certificates are to be issued support a larger key size).
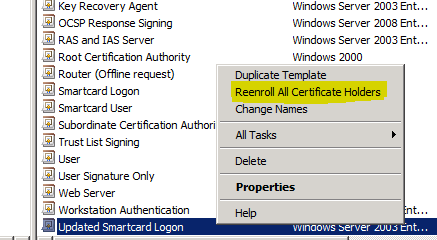
You should use Reenroll All Certificate Holders to cause the client computers to reenroll and request a larger key size (assuming certificate autoenrollment is enabled).
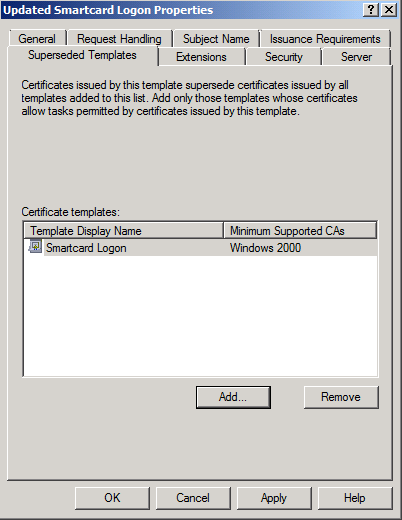
If you have issued certificates using the built-in Smartcard Logon or Smartcard User templates, you will not be able to adjust the minimum key size of the template directly. Instead, you will have to duplicate the template, increase the key size on the duplicated template, and then supersede the original template with the duplicated template.
After you have superseded the template, you should use Reenroll All Certificate Holders to cause the client computers to reenroll and request a larger key size.
Discovering usage of RSA keys under 1024 Bits in Cryptographic Operations
You can utilize CAPI2 logging starting with Windows Vista or Windows Server 2008 computers to help identify keys under 1024 bits. You can then allow the computers to perform their normal operations and check the log after a period of time to help identify such keys. You can then use that information to track down the sources of the certificates and make the necessary updates.
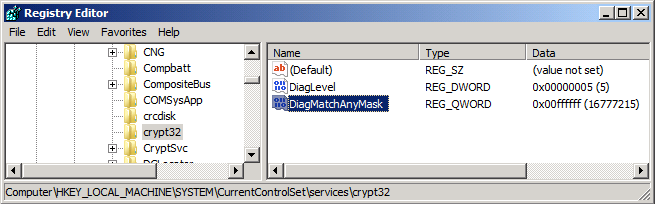
To accomplish this, you must first enable verbose diagnostic logging. To enable verbose mode logging:
- Open the Registry Editor (regedit.exe).
- Navigate to the following registry key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\crypt32
- Add a DWORD (32-bit) value DiagLevel with value of 0x00000005
- Add a QWORD (64-bit) value DiagMatchAnyMask with value of 0x00ffffff
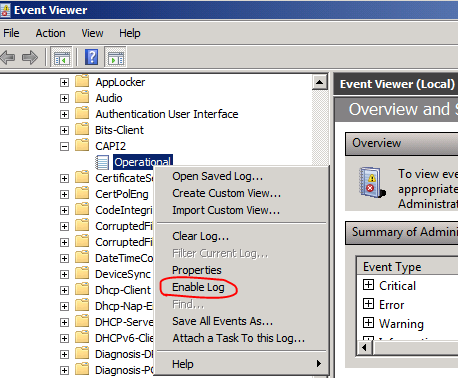
Once you do this, you can then enable CAPI2 operational logging in the Event Viewer. The CAPI2 Operational log is located under Applications and Service Logs, Microsoft, Windows, and CAPI2 in the Event Viewer. To enable logging, right-click the Operational log and select Enable Log.
Once you've collected the log, you can use the following filter to reduce the number of entries that you have to search through in order to find certificate operations with keys under 1024 bits. The following filter looks for keys of 512 bits.
<QueryList>
<Query Id="0"
Path="Microsoft-Windows-CAPI2/Operational">
<Select Path="Microsoft-Windows-CAPI2/Operational">Event[UserData[CertGetCertificateChain[CertificateChain[ChainElement[PublicKeyAlgorithm[@publicKeyLength='512']]]]] and
UserData[CertGetCertificateChain[CertificateChain[ChainElement[PublicKeyAlgorithm[@publicKeyName='RSA']]]]]]</Select>
</Query>
</QueryList>
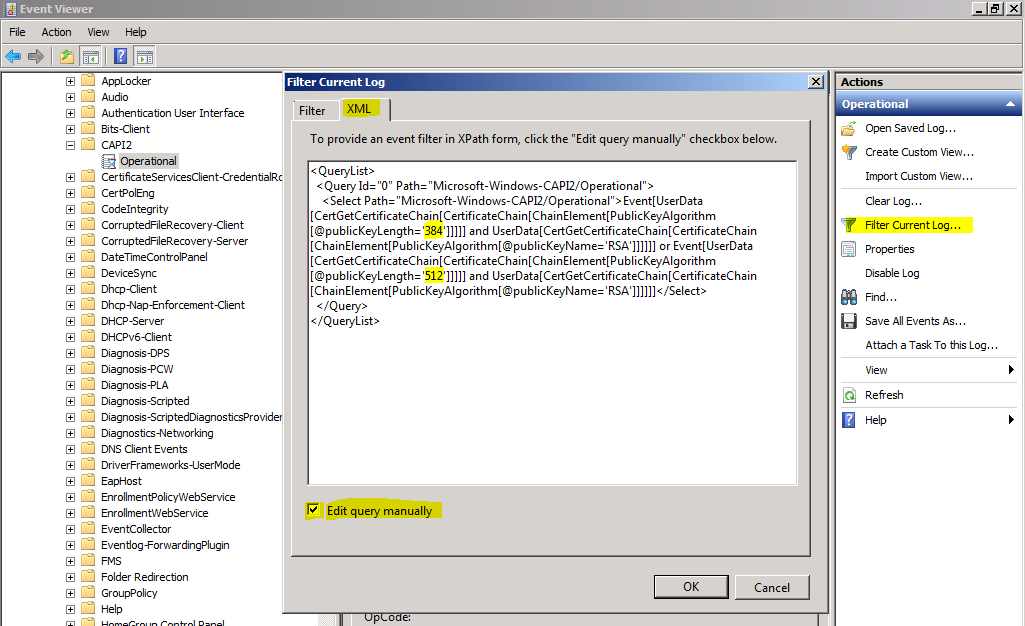
You can also query multiple key lengths with a single query. For example, the following filter queries for both 384 bit and 512 bit keys.
<QueryList>
<Query Id="0"
Path="Microsoft-Windows-CAPI2/Operational">
<Select Path="Microsoft-Windows-CAPI2/Operational">Event[UserData[CertGetCertificateChain[CertificateChain[ChainElement[PublicKeyAlgorithm[@publicKeyLength='384']]]]] and
UserData[CertGetCertificateChain[CertificateChain[ChainElement[PublicKeyAlgorithm[@publicKeyName='RSA']]]]]]
or
Event[UserData[CertGetCertificateChain[CertificateChain[ChainElement[PublicKeyAlgorithm[@publicKeyLength='512']]]]] and
UserData[CertGetCertificateChain[CertificateChain[ChainElement[PublicKeyAlgorithm[@publicKeyName='RSA']]]]]]</Select>
</Query>
</QueryList>
Discovering issued RSA certificates with keys less than 1024 bits
Ingolfur Arnar Stangeland came up with a certutil command to show whether a CA has issued RSA certificates with keys less than 1024 bits. He published the instructions in his blog post "How to identify if your ADCS has issued any certificates with public keys <1024 bits (in preparation for KB2661254)" https://blogs.technet.com/b/instan/archive/2012/08/03/how-to-identify-if-your-adcs-has-issued-any-certificates-with-public-keys-lt-1024-bits-in-preparation-for-kb2661254.aspx
Additional resources
Security advisory https://technet.microsoft.com/security/advisory/2661254.
KB 2661254: https://support.microsoft.com/kb/2661254
Additional blog posts:
https://blogs.technet.com/b/pki/archive/2012/07/13/blocking-rsa-keys-less-than-1024-bits-part-2.aspx
https://blogs.technet.com/b/pki/archive/2012/08/14/blocking-rsa-keys-less-than-1024-bits-part-3.aspx