Finding an Attribute's Property Set
Attributes vs Property Set
If you are granting access on an attribute level it's most likely you end up with long lists of Access Control Entries (ACEs) on objects in Active Directory. This will lead to database growth, the NTDS.dit will get bigger. It will also lead to degrading performance of you Domain Controller when it have to check all Access Control Entries.
Better would be to make use of property set's to grant access to predefined list of attributes, if that is suitable in your scenario.
Control Access Rights
Property set belongs to a category of objects called Control Access Rights, which are divided in three groups:
Extended Rights - ADS_RIGHT_DS_CONTROL_ACCESS (256)
Property Set - ACTR_DS_READ_PROP (16) and the ACTRL_DS_WRITE_PROP (32)
Validated Writes - ADS_RIGHT_DS_SELF (8)
Control Access Rights with the value of 48 in the validAccess attribute are property sets.
Property sets have a RightsGUID. For each attribute that belongs to a property set have the corresponding GUID in the attributeSecurityGUID property.
Example:
Attribute: TelePhone-Number
attributeSecurityGUID: 77b5b886-944a-11d1-aebd-0000f80367c1
Property set: Personal-Information
RightsGUID: 77B5B886-944A-11d1-AEBD-0000F80367C1
Attributes can only belong to one property set (attributeSecurityGUID is a single valued attribute).
These are default property set in Active Directory (you will get more with products like Microsoft Exchange for example):
- Account Restrictions
- DNS Host Name Attributes
- Domain Password & Lockout Policies
- General Information
- Group Membership
- Logon Information
- MS-TS-GatewayAccess
- Other Domain Parameters (for use by SAM)
- Personal Information
- Phone and Mail Options
- Private Information
- Public Information
- Remote Access Information
- Terminal Server License Server
- Web Information
Which Property Set To Use?
By using an property set you can grant read and write access to many attributes with one ACE, instead of a single ACE for each attribute.
Ok! But how can I identify the property set for my attribute?
First of all it's documented on MSDN: Property Sets
A faster way would be to search your Active Directory for a your attribute.
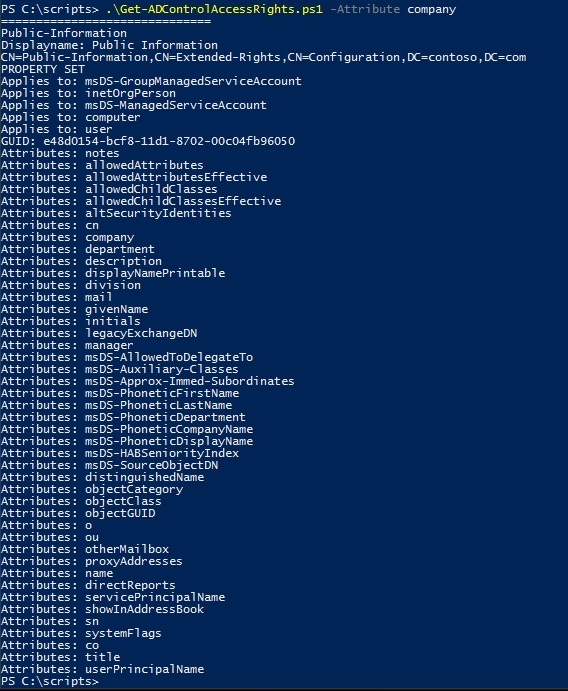
Let's say I want to know the property set for the attribute "company"
There's a script for that available in the Script Center: Get-ADControlAccessRights.ps1 .
How to retrieve the property set for "company":
Review the list of attributes to see if there is no harm in including a couple of more attributes when delegating the access. If you can live with a couple of more attributes in the access there could be a big win, instead of creating dozens of Access Control Entries.
All attributes does not belong to a property set. So If you search for a property set for an attribute and don't receive any information back, your attribute does not have a property set.
For example you might want to delegate access to one of these:
- employeeID
- employeeNumber
- employeeType
But none of them belong to a property set.
Good Luck, in delegating access! :)