Prevent Lateral Movement With Local Accounts
What is Lateral Movement?
Lateral movement is an activity used when an attacker is scavenging a network for credentials, typically used in a Pass-The-Hash scenario.
From Mitigating Pass-the-Hash (PtH) Attacks and Other Credential Theft Techniques.pdf
"In this activity, the attacker uses the credentials obtained from a compromised computer to gain access to another computer of the same value to the organization. For example, the attacker could use stolen credentials for the built-in local Administrator account from the compromised computer to gain access to another computer that has the same user name and password."
The local accounts issue
- What's the problem with local accounts, they're local to the machine right?
Well, there is a functionality like the "Windows for Workgroups" behaviour, inherited from previous versions of Windows, that makes local accounts a security issue. In this behaviour a client trust a local account from another machine if the password is exactly the same. This means that if you know the password of the local administrator account on one machine you could use that account to connect to other machines where the local administrator password is identically.
Normally you do not need local accounts when your machine is domain joined. You should use domain accounts instead.
How do you solve it?
One really good mitigation is to make the local administrators accounts passwords unique. Then you cannot use this account to connect to other machines.
But , how about other local accounts? Can you be sure there's no other local accounts created anywhere?
The best way is to prevent all local accounts to access other machines over the network via a group policy.
This can be done with the two new Well-known groups:
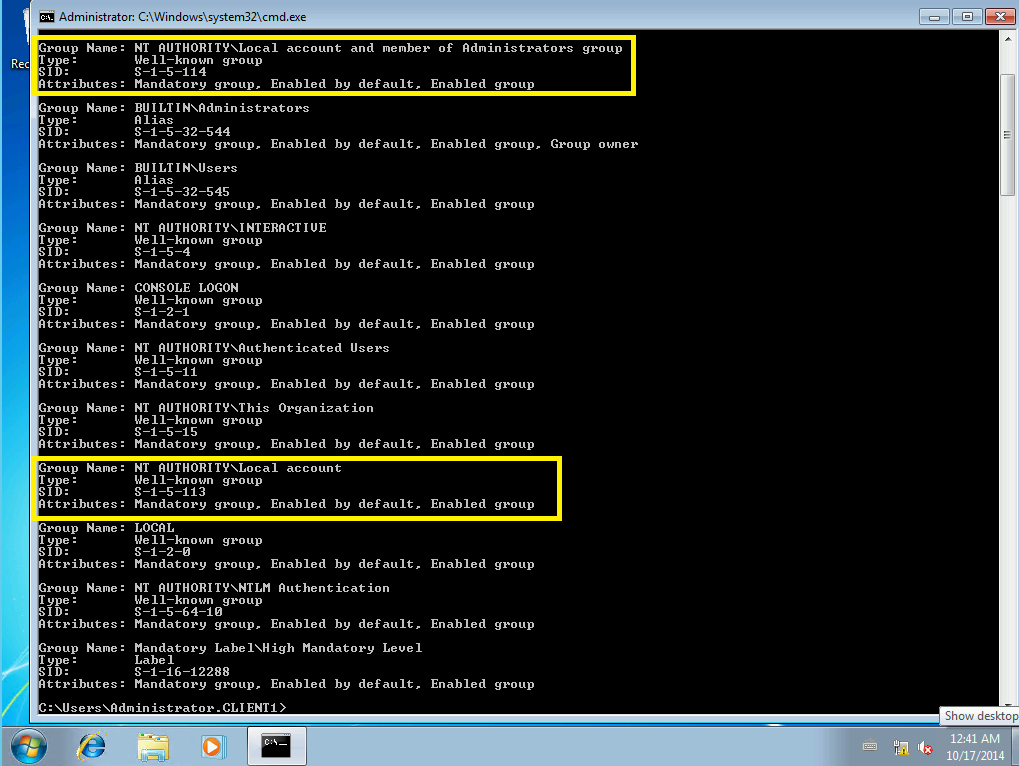
Local account S-1-5-113
All accounts in the local SAM .
Local account and member of Administrators group S-1-5-114
All accounts in the local SAM and member of the administrators Group.
How do you get these two new groups?
If you already have Windows 8.1/Windows Server 2012 R2 they're there waiting to be used.
If you have Windows 7, Windows Server 2008 R2, Windows 8 or Windows Server 2012 machines you have to install the security update KB2871997.
This update adds the new groups among other new great security features.
Before installing KB2871997 the group list for the local administrator account will look like this:
With KB2871997 installed:
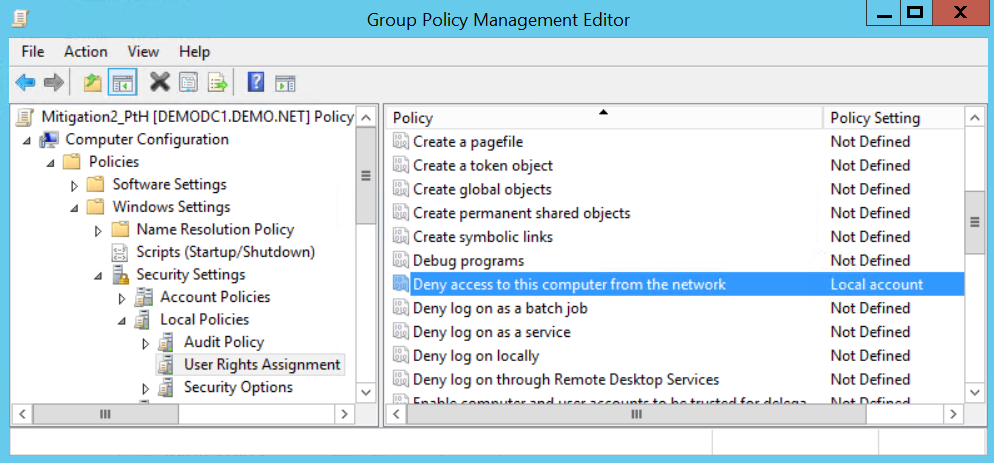
Create the Group Policy
By adding the new group "Local Account" to the user right assignment "Deny access to this computer from the network", you deny access to the computer for local accounts over the network. Set this setting in a group policy and apply it to your machines you would like to protect. I suggest you to make sure you do not have an application relying on this old legacy behaviour before applying it to the masses.
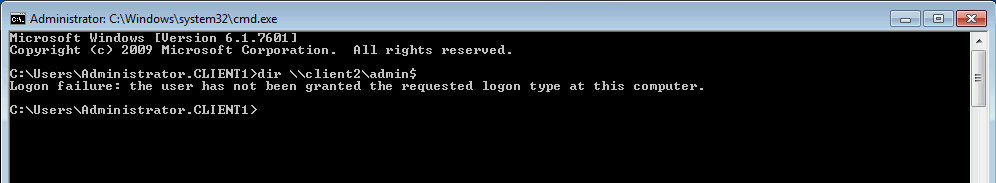
The Result
Local accounts will be limited to the machine where they are stored.
Perfect! They are kept right where they belongs.
Conclusion
This setting in combination with unique password and preventing local accounts from logging on using remote desktop you have relatively easy made a big impact on security!
From: Mitigating-Pass-the-Hash-Attacks-and-Other-Credential-Theft-Version-2.pdf