Hyper-V Virtual Identification
Since virtual machines can be easily moved between physical hosts (parents), it becomes important to track where virtual machines are physically residing for both asset management as well as troubleshooting purposes. The following post focuses on discovering the relationship between virtual hosts (parents) and the virtual machines (children) from both the perspective of the parent as well as the perspective of the child.
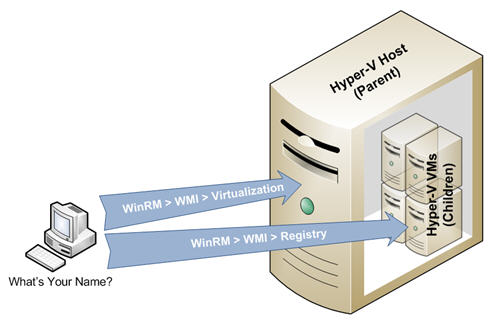
Note: The following examples use the WinRM and WinRS command-line utilities which shipped with Windows Vista and Windows Server 2008, but are also available as an Out-Of-Band install for Windows XP SP2+ and Windows Server 2003 SP1+ here .
Query the Parent:
Most commonly used for asset collection, this model gathers the names (and other virtual machine characteristics) of all the children running on a virtual host. This method queries the Hyper-V specific WMI provider/class by using the following command.
winrm enumerate wmi/root/virtualization/msvm_computersystem /r:<remote Hyper-V Host>
With the following sample output:
Msvm_ComputerSystem
AssignedNumaNodeList = 0
Caption = Virtual Machine
CreationClassName = Msvm_ComputerSystem
Description = Microsoft Virtual Machine
ElementName = PROV-XP
EnabledDefault = 2
EnabledState = 2
HealthState = 5
InstallDate
Datetime = 2008-07-01T21:47:02Z
Name = 31F497F1-2437-4E89-8308-BE07FB5C14C2
NameFormat = null
OnTimeInMilliseconds = 432464839
OperationalStatus = 2
OtherEnabledState = null
PrimaryOwnerContact = null
PrimaryOwnerName = OTTOH-HOST\Administrator
ProcessID = 2628
RequestedState = 12
ResetCapability = 1
Status = null
TimeOfLastConfigurationChange
Datetime = 2008-07-30T17:07:06Z
TimeOfLastStateChange
Datetime = 2008-07-30T17:07:06Z
Query the Child:
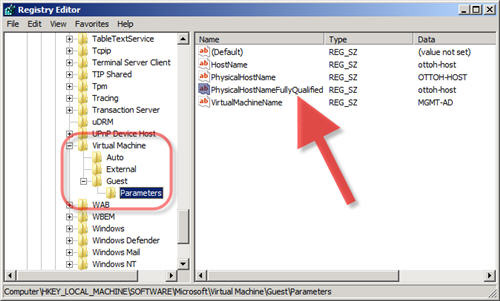
Most commonly used for troubleshooting scenarios where a virtual machine is being evaulated and needs to be queried in order to determine its physical host (parent). The following command queries the registry on the child in order to determine its host (parent):
Remote Access Method #1 (the /f parameter merely structures the output in XML – handy for scripting, especially in PowerShell):
winrm invoke GetStringValue wmi/root/default/StdRegProv @{hDefKey="2147483650";sSubKeyName="Software\Microsoft\Virtual Machine\Guest\Parameters";sValueName="PhysicalHostNameFullyQualified"} /r:<Remote VM> /u:<Username> /p:<Password> /f:pretty
Remote Access Method #2:
winrs /r:<Remote VM> /u:<Username> /p:<Password> reg query "HKLM\Software\Microsoft\Virtual Machine\Guest\Parameters" /v PhysicalHostNameFullyQualified
Note: The first method demonstrates a powerful way to access the value of any registry key using the ‘StdRegProv’ WMI provider via WS-Man/WinRM for remote transport. Other registry hives can be accessed with the following hDefKey values: HKLM=2147483650, HKCU=2147483649, HKCR=2147483648, HKEY_USERS=2147483651.