Security Monitoring–Using SCOM to Detect Legacy TLS Protocol Usage
Disclaimer: Due to changes in the MSFT corporate blogging policy, I’m moving all of my content to the following location. Please reference all future content from that location. Thanks.
This has been on my bucket list for a while now, and I finally got around to figuring it out. TLS is a transport layer protocol that is effectively a part of SSL. Basically, it’s used to encrypt web based traffic so that prying eyes cannot see. Like every protocol, over time its weaknesses are exposed and newer versions are released. Like every protocol, the older versions remain on given that legacy applications can break. Last year, Microsoft started releasing updates to their applications to eliminate TLS 1.0 and 1.1 from usage, and it’s officially recommended that these protocols be shut off with only TLS 1.2 being used.
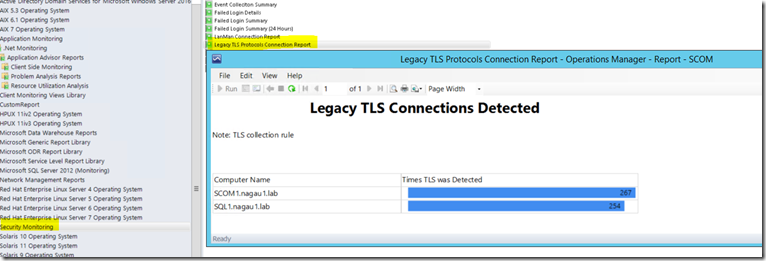
I spent some time trying to figure out how to audit legacy TLS usage and found that to be an incredibly frustrating search. There’s not much out there on auditing TLS. The answer, as it usually is, was right in front of me from a Kevin Holman article on how to force SCOM to use TLS 1.2. As such, I’ve setup a collection rule to collect these events. That said, this is not plug and play. Before I get into the details, it’s worth noting that event collection rules can generate lots of data in your DataWarehouse. In my own lab, I’m seeing about 600 events a day across 2 systems. So just imagine for a second what that might look like with thousands of systems. You may want to consider turning this on in small quantities (and turning it off once you have the data you need).
Step 1 – Enable Schannel Logging. Kevin covered the details of how to do this in his post. I simply created a GPO and linked it at the domain, though you may want to link to specific OUs instead. In my case, I set a GPO preference to change the following registry key: HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\ EventLogging
This is a REG_DWORD value that needs to be set to 7.
Step 2 – wait a day and run the report. It should look like this: