How to Configure DirectAccess in Windows Server 2012 to Work with an External Hardware Load Balancer
Summary: Gregg O’Brien , a Microsoft Premier Field Engineer from Canada, provides insight and walks us through how to configure DirectAccess in Windows Server 2012 to work with an External Hardware Load Balancer.
DirectAccess is quickly becoming a popular solution for providing remote access to users, especially since the release of Windows Server 2012.
DirectAccess can be installed in a standalone configuration using only one server, or it can be installed using one of two load balancing mechanisms: Integrated Windows Network Load Balancing and External Hardware Load Balancing. Both of these methods have their benefits, but customers looking for load balancing across large geographies, higher levels of performance, or to leverage an existing investment may choose to go with an external hardware-based load balancer.
The DirectAccess wizard takes care of the configuration of the Integrated Windows Network Load Balancing, but what about when an external hardware load balancer will be used? Let’s have a look at the steps involved in accomplishing this task.
For the purpose of this article, we will assume that you already have an existing standalone DirectAccess 2012 server that currently works.
To configure your DirectAccess environment for use with the external hardware load balancer, we perform the following steps:
1) Logon to the DirectAccess server that is currently in operation. This will be Node1. Launch the Remote Access console to begin the DirectAccess configuration.
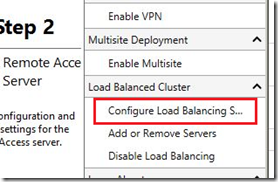
2) From the right-most pane, select “Configure Load Balancing”
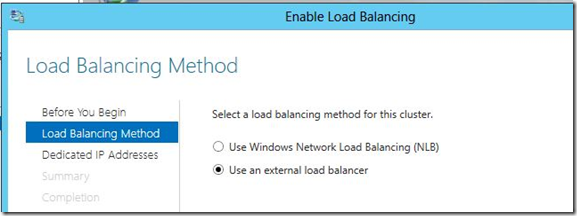
3) Selection the option for “Use an external load balancer” and click “Next”
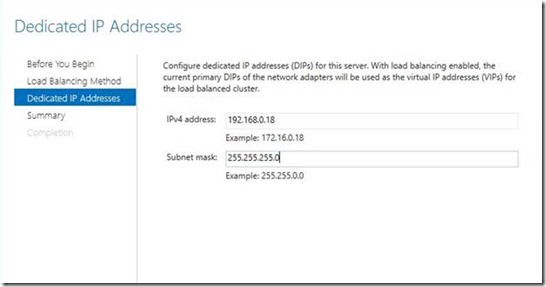
4) The wizard will ask for a new dedicated IP address for Node 1. The existing dedicated IP address will be used as the virtual IP address of the load balancer to avoid requiring any DNS changes as a result of this process.
If you receive the error message “Either the server is configured as an ISATAP router or no IPv6 addresses were detected on the internal adapter on the server. This is not supported in a cluster configured to use an external load balancer. Either deploy IPv6 in the internal network, or deploy an external ISATAP router, and configure IPv6 connectivity between the router and the Remote Access server”, then head over to Microsoft Support to obtain a hotfix that will resolve the issue. Once the hotfix has been applied, run through the steps again.
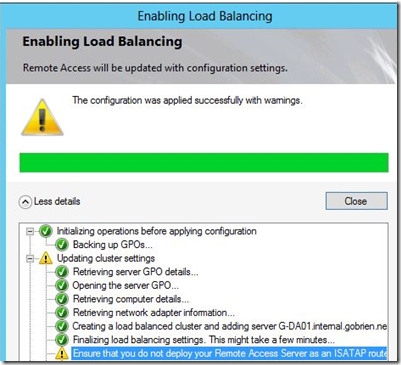
5) Click “Next” to proceed to the Summary page and then click “Commit” to apply the changes.
6) Upon committing the changes, you will see a warning message regarding ISATAP:
This warning occurs because we may not be able to use ISATAP on the DirectAccess server any longer. In this scenario, there are two options: place an external load balancer that supports ISATAP on the internal network and enable ISATAP on either DirectAccess servers, or disable ISATAP completely which then disables the “manage-out” functionality of DirectAccess.
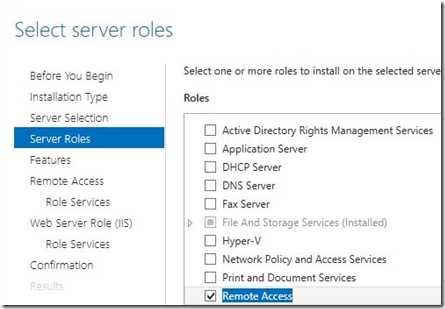
7) Now head over to Node2 and configure the Roles and Features to add the Remote Access components.
8) Once the Roles and Features installation is complete, be sure to import the IP-HTTPS certificate used in the initial DirectAccess configuration into the Computer Store of Node2. (A self-signed certificate will not work in this scenario)
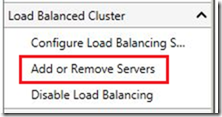
9) Now head back to Node1 and open the Remote Access console.
10) Look for the option to “Add or Remove Servers” in the right pane
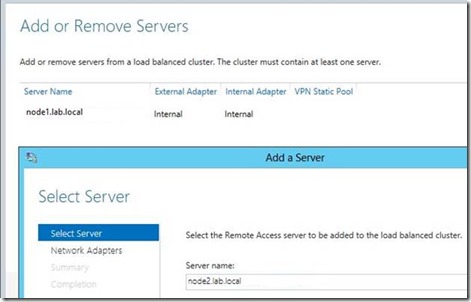
11) Type in the name of Node2 and click “Next”
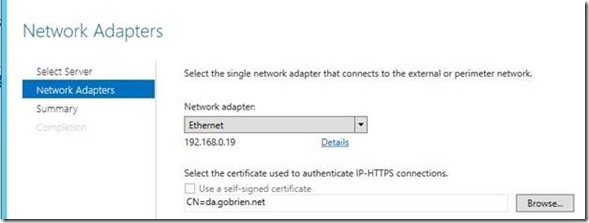
12) Now select the Network Adapter and the IP-HTTPS certificate that Node2 will be using:
13) Click “Commit” and then close to apply the configuration.
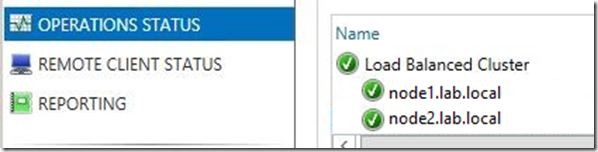
14) Once the configuration is complete, you can click on the “Operations Status” link in the console to check the status of the array:
Once the load balancer can communicate with both nodes, they should turn green with a check mark.
For more information about configuring the external load balancer, be sure to consult with the vendor of the equipment. For example, F5 published a great whitepaper on how to configure F5 load balancers to support DirectAccess.
And with that all completed, we have a single-NIC DirectAccess 2012 deployment with external load balancing!