Managing Microsoft BitLocker in the Enterprise
Written by Mark Farrugia, Senior Microsoft Premier Field Engineer.
In my previous posts I introduced the concept of BitLocker and talked about managing the Trusted Platform Module, now let’s talk about how we can enforce policy to ensure clients are indeed encrypting their system and data volumes. In this post I will discuss some of the major group policies that an enterprise should keep in mind when configuring policy for BitLocker.
Enforcing BitLocker Policy via Group Policy
To enforce BitLocker policy, we will not reinvent the wheel. Instead, we’ll take advantage of the built-in group policy settings to ensure the client is enforcing the settings set out by the enterprise. The group policy settings for BitLocker are located in:
COMPUTER CONFIGURATION ? POLICIES ? ADMINISTRATIVE TEMPLATES ? WINDOWS COMPONENTS ? BITLOCKER DRIVE ENCRYPTION
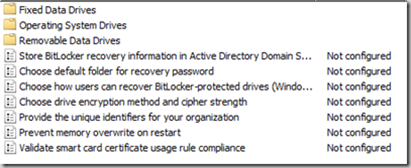
Within this node you will find a number of settings that can be configured to enforce BitLocker compliance.
Specifically you can choose to store your BitLocker recovery information to Active Directory. There are some prerequisites that need to be fulfilled before this policy can be enabled:
- The Active Directory schema needs to support the BitLocker extensions. If you are running Windows 2008 Active Directory or newer, you are okay and no further work is needed. If you are running Windows 2003 Active Directory, the schema will need to be extended to allow the computer account to accept the BitLocker Recovery Key.
- The machines need to be given permission to allow “SELF” to write an attribute to their own machine account.
- The machine must be domain joined before enabling BitLocker.
- This domain policy must be enabled before enabling BitLocker.
If you so choose to and or you do not enable Active Directory integration, you can have BitLocker upload the recovery key to a predefined network location. To configure this option, enable “Choose default folder for recovery password” and provide a UNC path that the machine account has permissions to write to. I recommend you make it a hidden share, and lock it down tightly and audit who has access to this share. This option must be enabled prior to BitLocker being enabled so that the wizard will upload the key accordingly.
There are additional options that can be configured, like “Provide the unique identifiers for your organization”. This option is key in an enterprise with a properly configured PKI. By inputting your organization’s unique identifier into a special field, manage-bde will update the encrypted volume with your organizations certificate. This is important for a large organization because it is used in combination with the "Deny write access to removable drives not protected by BitLocker" policy setting to help control the use of removable drives in your organization.
Recovery Options for BitLocker-Enabled Devices
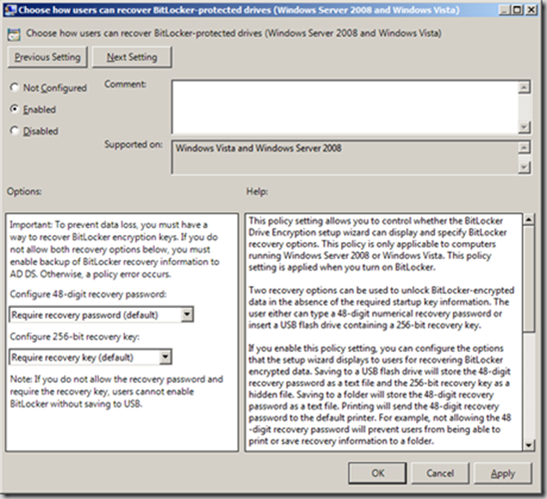
Further options for BitLocker protection include how to recover a BitLocker enabled volume. The default values require a 48-digit recovery password and or a 256-digit recovery key. The 48-digit key is saved to a text file on a USB flash drive, and up to a network share if configured; the 256-digit key is saved as a hidden file on a flash drive. The 48-digit key will not be available in FIPS compliance mode. Additionally, if choose not enable these recovery methods, you have to enable the option to save recovery information to Active Directory to avoid a policy conflict error.
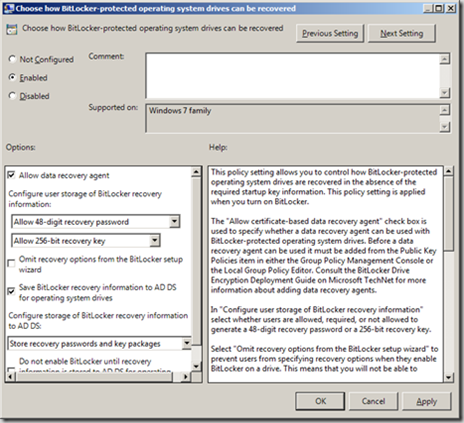
The policy above is related to how users can recover a BitLocker protected drive, however you can also have options on how different volumes (operating system, fixed drive and removable drives) can be recovered. For Operating system you can choose to enable the use of the recovery keys through the data recovery agent, to enable the saving of the information to Active Directory, and further choose to not enable BitLocker until the recovery information is stored in ADDS. This final option is important to prevent users from enabling BitLocker when disconnected from the domain, this will ensure recovery information is stored to Active Directory properly.
More Information on BitLocker
The above are some of the major settings I tell organizations to keep in mind when configuring/enabling BitLocker in their environments. Further information can be found on BitLocker at these following locations: