Managing the Trusted Platform Module with Windows
Written by Mark Farrugia, Senior Microsoft Premier Field Engineer.
There are many volume encryption technologies out there, and some of these are now taking advantage of technology that Microsoft BitLocker has been using from its inception. The Trusted Platform Module (TPM) chip is a micro-computer built onto all new motherboards that contains its own CPU and Flash Memory and is capable of creating, storing and managing encryption keys.
Every TPM Chip has the following capabilities:
- Performs cryptographic functions
- RSA, SHA-1 and RNG
- Each TPM chip provides
- a unique endorsement key (EK)
- a unique Storage Root Key (SRK)
- Anchors chain of trust for keys and credentials
- Protects itself from attack
Managing TPM for Individual Users
By default I have seen many manufacturers shipping their computers with the TPM chip disabled in the BIOS. Obviously before we can use BitLocker and or any other TPM enabled application we will need to enable the TPM chip. This can be accomplished with the following command from Windows 7.
manage-bde -tpm –TurnOn
Once the TPM is enabled you can start the BitLocker wizard and it will guide you through the rest of the process to get your machine protected, and or you can take ownership of the TPM by issuing the following command from within Windows 7:
manage-bde -tpm -TakeOwnership test_password
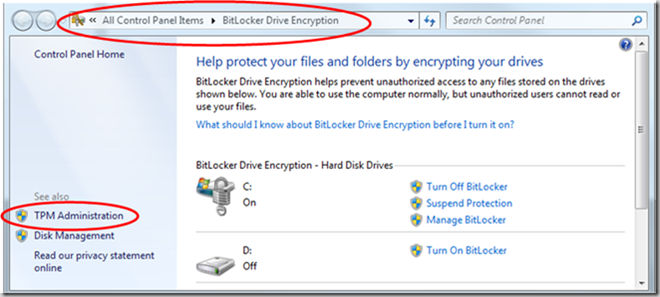
Additionally the same tasks can be accomplished through the graphical user interface in Windows 7. Go to the START ? CONTROL PANEL ? BITLOCKER DRIVE ENCRYPTION ? TPM ADMINSTRATION
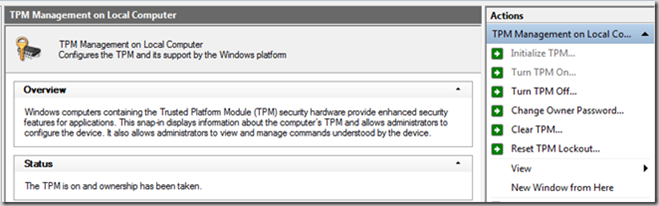
This will open a new MMC snap-in that will allow you to perform the same tasks as listed above.
Managing TPM in the Enterprise
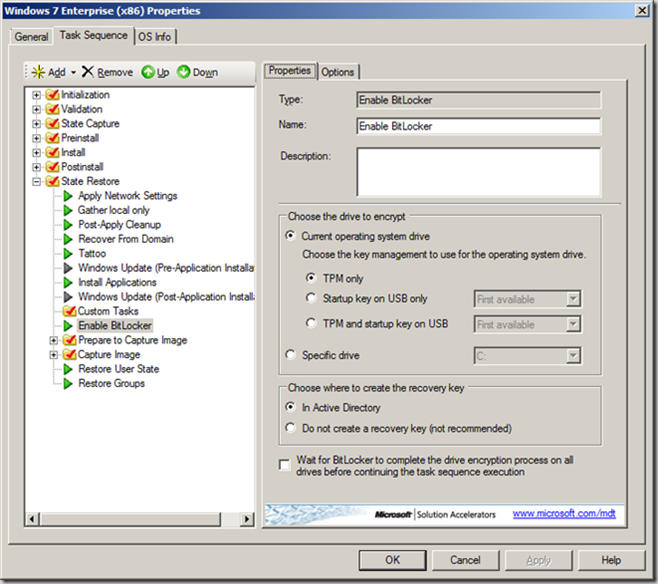
The above is all well and good for an individual user, but for an enterprise that is doing a mass deployment of Windows 7 to mobile computers, there must be an easier way. And fortunately there is, within the Microsoft Deployment Toolkit (MDT) and SCCM task sequencer there are steps in the task sequence that have been prebuilt to enable BitLocker and initialize the TPM as part of the deployment of Windows 7.
From the screenshot above it becomes easy to choose which option for TPM you would like to complete.
Other TPM Resources
There are many resources on the Microsoft website that detail how to use the TPM chip with BitLocker to allow for a seamless experience of using volume encryption with Microsoft Windows 7. Here are some of the ones I recommend: