Beyond Antivirus Software: 7 Additional Ways to Secure a Windows Desktop
Written by Mark Farrugia, Senior Microsoft Premier Field Engineer.
 Most computer end-users thinks that if they’re running antivirus software then their safe from all the malicious users out on the internet. People feel their antivirus software is the first and last line of defense in the ongoing battle of online security. People feel because they may pay for a service (antivirus subscription services), that they have now passed on the responsibility of their personal security to a third party agency. This is not the correct mentality to have; personal security is your responsibility. This article will discuss at a high level some of the steps a user can perform on their very own machines to better secure themselves against the growing number of online threats.
Most computer end-users thinks that if they’re running antivirus software then their safe from all the malicious users out on the internet. People feel their antivirus software is the first and last line of defense in the ongoing battle of online security. People feel because they may pay for a service (antivirus subscription services), that they have now passed on the responsibility of their personal security to a third party agency. This is not the correct mentality to have; personal security is your responsibility. This article will discuss at a high level some of the steps a user can perform on their very own machines to better secure themselves against the growing number of online threats.
1. Leverage the Standard User Account
 This should be a standard practice for all users and enterprises. Running day to day tasks as a consumer of the computing device should not require the user to have elevated privileges all the time. To create content, be it a web page, document, spreadsheet, presentation, video etc. does not require administrative rights, but installing applications, changing system settings etc. does. These tasks that require those elevated rights are usually performed at the time the machine is setup, and it should not be necessary to revisit those settings regularly.
This should be a standard practice for all users and enterprises. Running day to day tasks as a consumer of the computing device should not require the user to have elevated privileges all the time. To create content, be it a web page, document, spreadsheet, presentation, video etc. does not require administrative rights, but installing applications, changing system settings etc. does. These tasks that require those elevated rights are usually performed at the time the machine is setup, and it should not be necessary to revisit those settings regularly.
An ideal scenario for a home user would be to have a standard account (e.g. User) with a strong password, and an administrative account (e.g. User-Adm) with a different, stronger password. In addition, Microsoft has made certain system level tasks like changing the time-zone in Windows a user level task now. This enables road warriors to run their day-to-day tasks as a standard user.
If you want to change your account type without losing your working profile can follow this small article - Change a user's account type.
For an enterprise, the excuse to have users running as local administrators should be less. Through the use of automated system management software, group policy, and centralized administration the computer is just an end point to allow your customers to get their job done. The biggest culprit impacting corporate environments today that forces them to provide administrative privileges to their users is legacy software. There is no real solution, except remediating the application through upgrades, rewriting the application if it is an in house solution, virtualization, and/or application hosting.
2. Don’t Ignore User Account Control (UAC)
 User Account Control is an often misunderstood technology. It is commonly categorized a security feature, when I would actually describe it more as an educational tool to inform the user that their actions could have consequences. The way I like to think of User Account Control is to give you a scenario to compare it to. You’re out with friends, and had a couple of drinks. At the end of the night you grab your car keys and start to head out the door of the establishment. Your buddy UAC jumps in and says “Are you okay to drive?” You reply “Yes,” and UAC responds “Are you sure you’re not drunk?” “Yes,” you reply, and UAC just allows you to continue on. In that scenario, UAC would not stop you from doing something foolish if you had too much to drink; hence it’s the same thing on your computer. UAC will warn and prompt you when something potentially bad could happen, but it will not stop you from doing something bad. UAC is good thing to have around, but ultimately you’re responsible for your actions.
User Account Control is an often misunderstood technology. It is commonly categorized a security feature, when I would actually describe it more as an educational tool to inform the user that their actions could have consequences. The way I like to think of User Account Control is to give you a scenario to compare it to. You’re out with friends, and had a couple of drinks. At the end of the night you grab your car keys and start to head out the door of the establishment. Your buddy UAC jumps in and says “Are you okay to drive?” You reply “Yes,” and UAC responds “Are you sure you’re not drunk?” “Yes,” you reply, and UAC just allows you to continue on. In that scenario, UAC would not stop you from doing something foolish if you had too much to drink; hence it’s the same thing on your computer. UAC will warn and prompt you when something potentially bad could happen, but it will not stop you from doing something bad. UAC is good thing to have around, but ultimately you’re responsible for your actions.
Therefore, when UAC prompts you and you were not expecting a prompt, stop and take a moment to actually read the prompt. It may be the difference between having a safe computing experience and having malware installed on your machine.
An excellent article written by Microsoft’s own Mark Russinovich on UAC can be read at the following link - Inside Windows 7 User Account Control.
3. USB Lockdown
 I have previously blogged about USB Lockdown, so I will not go into great detail here again, but recently a very nasty and targeted worm called Stuxnet was making its way around the Internet. The virus itself was too big to be emailed (~700 KB) without being noticed. This worm’s initial and primary method of transfer was to copy itself to removable media such as a USB key. Had many of these targeted systems employed USB control procedures they could have limited their exposure to this worm.
I have previously blogged about USB Lockdown, so I will not go into great detail here again, but recently a very nasty and targeted worm called Stuxnet was making its way around the Internet. The virus itself was too big to be emailed (~700 KB) without being noticed. This worm’s initial and primary method of transfer was to copy itself to removable media such as a USB key. Had many of these targeted systems employed USB control procedures they could have limited their exposure to this worm.
4. Application Locker (AppLocker)
 AppLocker is another topic I had previously blogged about, but in the same vein as the USB Lockdown example, controlling which applications execute on your machine helps prevent malware from automatically running and installing itself on your workstation. Both the USB and Application lockdown policies can assist you in preventing a zero-day attack on an unreported/unpatched vulnerability.
AppLocker is another topic I had previously blogged about, but in the same vein as the USB Lockdown example, controlling which applications execute on your machine helps prevent malware from automatically running and installing itself on your workstation. Both the USB and Application lockdown policies can assist you in preventing a zero-day attack on an unreported/unpatched vulnerability.
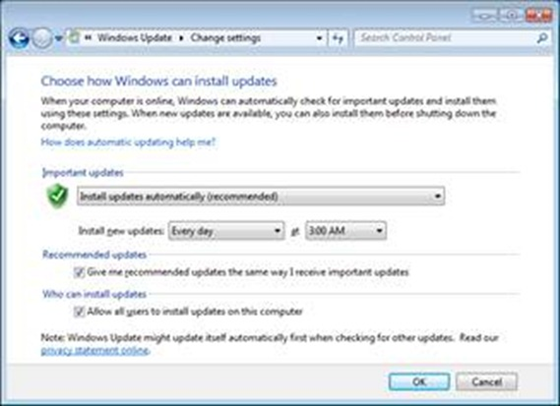
5. Windows Update
 If you’re the type that likes to see which updates are being applied to your computer, you’ll probably want to be prompted for Windows update. If you’re the type that doesn’t care, you’ll probably set your Windows update to automatically install updates without prompting you. Notice that I never said disable updates, please do not disable Windows Update.
If you’re the type that likes to see which updates are being applied to your computer, you’ll probably want to be prompted for Windows update. If you’re the type that doesn’t care, you’ll probably set your Windows update to automatically install updates without prompting you. Notice that I never said disable updates, please do not disable Windows Update.
Regardless of which type of schedule you choose, installing updates to your operating system and applications is one of the best ways to protect your machine.
For a small or medium business, you may not have an enterprise software distribution system that will distribute patches for you, so at the very minimum Windows Server Update Services (WSUS) should be considered. The advantages to this are that it provides a centralized management point for Windows updates, allows the administrator to choose which updates and products get updated, and provides flexibility that if the user is on the road, they can choose to connect back to the central server of Microsoft Update to receive the latest hot fixes. More information on WSUS can be found here.
For an enterprise, a centralized software distribution system such as System Center Configuration Manager R3 (ConfigMgr R3) should be providing windows updates to all machines.
6. Windows Firewall
 Use of a software firewall is mandatory today on the internet. Microsoft strongly recommends running a desktop, server and perimeter firewall, and instead of having a wide open network, only the necessary TCP/UDP ports, protocols and services are allowed to pass through the firewall. Microsoft Windows has been shipping an enhanced firewall since the introduction of Windows Vista and is enabled by default in every Windows installation.
Use of a software firewall is mandatory today on the internet. Microsoft strongly recommends running a desktop, server and perimeter firewall, and instead of having a wide open network, only the necessary TCP/UDP ports, protocols and services are allowed to pass through the firewall. Microsoft Windows has been shipping an enhanced firewall since the introduction of Windows Vista and is enabled by default in every Windows installation.
Windows Firewall offers three profiles by default, Domain, Private and Public, to be used respectively in your work, home and public. The Microsoft Windows Firewall with Advanced Security can be administered locally through the built-in Microsoft Management Console (MMC) snap-in, and or centrally through Windows Group Policy.
More information on the Firewalls can be found at the Network Security site. Additional information on the Microsoft Windows Firewall can be found here.
7. Leverage Virtual Machines
 An easy way to mitigate all this risk while surfing the Internet is to browse the Internet from a virtual machine on your desktop. The advantage to the virtual machine is that it is isolated from the physical host; in addition the VM can be set to have a differencing disk, and upon shutdown or reboot of the virtual machine all the changes that were incurred during that session can be discarded, and your previously fresh virtual machine can be used once again.
An easy way to mitigate all this risk while surfing the Internet is to browse the Internet from a virtual machine on your desktop. The advantage to the virtual machine is that it is isolated from the physical host; in addition the VM can be set to have a differencing disk, and upon shutdown or reboot of the virtual machine all the changes that were incurred during that session can be discarded, and your previously fresh virtual machine can be used once again.
There are many free virtualization software packages, Microsoft provides Virtual PC 2007 for Pre-Windows 7, and Windows Virtual PC for Windows 7.
Install an Antivirus solution
 The whole point of this article was to find additional ways to secure your desktop, but if you are not running antivirus then this may be all for not. Microsoft’s Defense in Depth strategy talks in some detail on how you can secure your data, applications, host, internal network and perimeter. Each of the above components can be part of your solution.
The whole point of this article was to find additional ways to secure your desktop, but if you are not running antivirus then this may be all for not. Microsoft’s Defense in Depth strategy talks in some detail on how you can secure your data, applications, host, internal network and perimeter. Each of the above components can be part of your solution.
There is no excuse for not using antivirus software today, as many vendors, Microsoft included, are providing free antivirus software. You can obtain Microsoft Security Essentials (MSE) for free from Microsoft download center, and or if your home machine does not have antivirus, you may see MSE listed as an optional download form Microsoft Update. I highly recommend you take advantage of the free protection.
In conclusion, you can see how many different approaches Microsoft Windows offers to further secure your computer besides just running Antivirus software. Each of the approaches listed above complements your antivirus software when implemented properly.