How To Control Applications In Windows 7 With AppLocker
Written by Mark Farrugia, Senior Microsoft Premier Field Engineer
 For my follow up article to How to use Windows 7 to lock down removable media and keep your computer safe, I would like to discuss another feature within Windows 7 Enterprise and Ultimate editions that both individuals and enterprises can take advantage of – AppLocker.
For my follow up article to How to use Windows 7 to lock down removable media and keep your computer safe, I would like to discuss another feature within Windows 7 Enterprise and Ultimate editions that both individuals and enterprises can take advantage of – AppLocker.
AppLocker is a new feature built within Windows 7 that allows an organization or individual to whitelist applications on their workstation. In the past, Windows had made use of “Software Restriction Policies” that were there to blacklist applications, however with AppLocker we have the ability to do either task – whitelist or blacklist an application. Software Restriction Policies were easy to implement, but operationally it was a difficult task to maintain.
Why Do We Need A Mechanism To Control Which Applications Are Allowed To Run On A Workstation?
Good question. Some organizations continue to give out local administrator privileges on the workstation to their general users, therefore enabling those users to install any piece of software they wish. Unfortunately, that software is most likely not on the company approved vendor list, may not be legally licensed, and/or it may have provisions in the EULA that are in direct conflict with company policy. This can be both harmful and a potential liability for the enterprise from license compliance perspective.
From an individual owner’s perspective, and even an enterprise’s perspective, an additional benefit to AppLocker is that it can aid and assist in reducing your exposure to malware attacks by limiting what code can execute your machine.
In this post I want to introduce the AppLocker configuration wizard and interface to get you familiar with the basics, so you can begin to create elaborate policy that will help you lockdown and control your organization’s application inventory.
AppLocker Requirements
To use AppLocker you must be running one of the following operating systems:
- Windows Server 2008 R2 Standard
- Windows Server 2008 R2 Enterprise
- Windows Server 2008 R2 Datacenter
- Windows Server 2008 R2 for Itanium-Based Systems
- Windows 7 Ultimate
- Windows 7 Enterprise
How to Get to AppLocker
As mentioned, AppLocker is available in Windows 7 Enterprise and Ultimate SKUs from a client perspective. Additionally, the same policies are available in Windows Server 2008 R2. This feature is accessed through Windows Group Policy, so it’s is available individually (gpedit.msc) or from an enterprise standpoint (gpmc.msc) in an Active Directory environment.
Once your group policy editor is opened, to find AppLocker navigate to the following location.
COMPUTER CONFIGURATION – > POLICIES – > WINDOWS SETTINGS – > SECURITY SETTINGS – > APPLICATION CONTROL POLICIES à APPLOCKER
The AppLocker User Interface
The interface to AppLocker is designed to be simple, yet powerful.
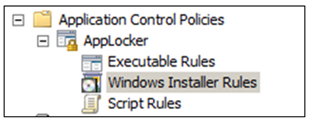 As depicted in this image, you have three sections to create your rules against – Executable Rules, Windows Installer Rules and Script Rules. Executable Rules and Script Rules define which programs or scripts are or are not allowed to execute on the target machine. Similarly, Windows Installer Rules defines which MSI packages can or cannot be installed onto a target machine.
As depicted in this image, you have three sections to create your rules against – Executable Rules, Windows Installer Rules and Script Rules. Executable Rules and Script Rules define which programs or scripts are or are not allowed to execute on the target machine. Similarly, Windows Installer Rules defines which MSI packages can or cannot be installed onto a target machine.
Left Clicking on each one of those nodes, and then navigating to the whitespace on the screen to the right in the editor, and right clicking in the empty whitespace will bring up a context menu to create a new rule.
The three options we are interested in are at the top of the context menu:
- Create Default Rules
- Create New Rules…
- Automatically Generate Rules…
1. Create Default Rules
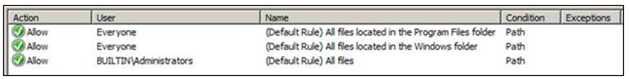
This is the simplest to explain so we will start here, by choosing this option AppLocker will create a default rule set for your configuration. This is a great starting point for understanding rules and to get a basic set of rules implemented. The following will be created by default for Executable Rules:
Similar rule sets will be created for Windows Installer Rules and Script Rules.
2. Automatically Generate Rules
This option will point to a specific location on a machine, and automatically scour the machine for executables, MSIs and or scripts and configure the rules automatically as a base starting point. This option is extremely useful for an Enterprise that is building their base image and wants to quickly generate a rule set that can be applied to the user community.
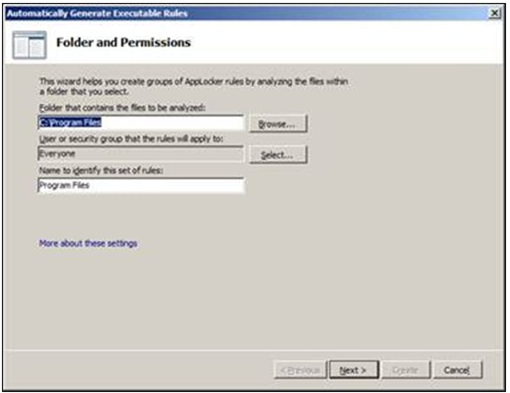
When starting the wizard this is the first screen you will be presented with. In this screen you have to choose your path, and an identifier for the configured rules.
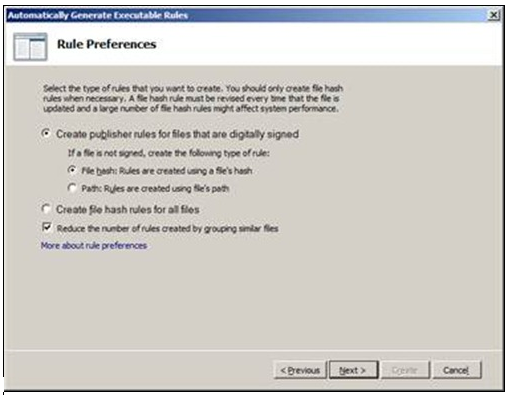
Clicking on Next will show a default rule set screen that will allow you to configure the behavior of the discovery.
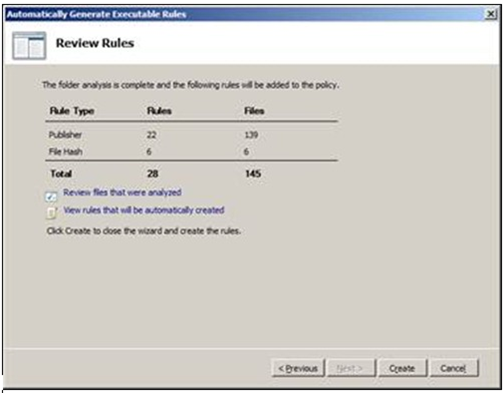
Clicking on Next will start the discovery, after which a summary screen will be displayed.
You have the option to view all the files that were examined as part of the search, and the corresponding rules that will be created. Click on create to create the rules.
3. Create New Rule…
When “Create New Rule…” is chosen, a new rule a wizard will open up that will guide you through the process of configuring AppLocker. For the purpose of this post I will go through the screens of the wizard for the Executable Rules, but the other wizards are very similar in design.
The first screen is a welcome screen that can be chosen to skip by default.
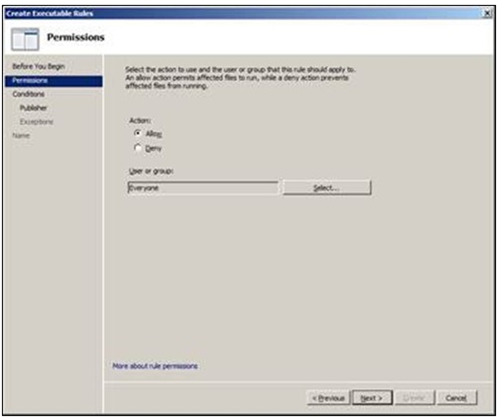
The second screen is where the configuration begins, this is where we choose if the behavior of this rule is going to allow or deny access, and to whom is the rule going to be scoped. On an individual workstation I don’t believe the user or group option will have a significant impact, but in an enterprise organization this is where the power of AppLocker starts to shine.
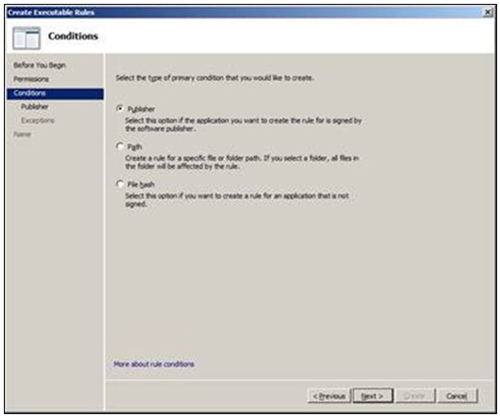
After clicking on Next, the following screen is presented that will have three options. Choose the option that will make the most sense for that particular application.
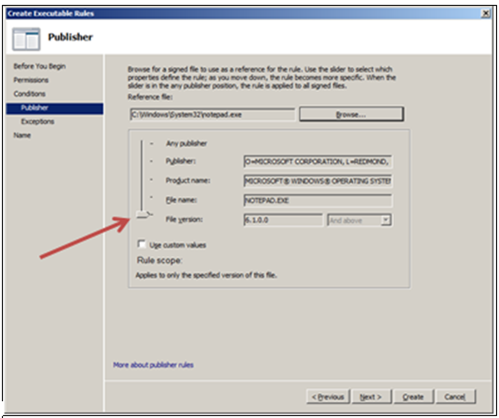
For this example I choose “Publisher” and after clicking on Next, you’re presented with the following screen. After browsing for your signed executable, all the fields will be populated automatically. The most important and simplest function on this screen is the slide control that is highlighted. This will let you scope the granularity of the rule from most restrictive (File Version) and slide it up to least restrictive (Any Publisher). Using custom values will allow you to edit the fields that are prepopulated.
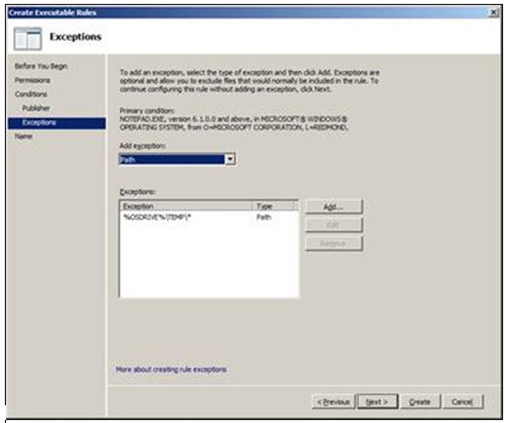
Upon continuing in the wizard, the following screen is the exceptions screen, where you can once again add an exception based on Publisher, Path and or File Hash. I have added the path %OSDRIVE%\TEMP\* as an exception.
And finally after clicking on Next, name your rule and choose to create it.
In my example above, I created an Executable Rules rule. Within that rule I allowed Notepad.exe to be run by Everyone, however I added an exception that if Notepad.exe is located in %OSDRIVE%\TEMP\*, it will not be allowed to execute.
Enabling the AppLocker Rules
So you’ve gone through the exercise of creating all these great rules. You’ve scoped the rules to the appropriate user groups, and you’ve linked your new policy to your organizational unit within Active Directory that contains all your Windows 7 machines. However, you discover that your AppLocker rules are not applying.
There is one final step, which is to right click on the AppLocker top level node, and choose properties.
Once you do that you will be presented with the final configuration step necessary to enable AppLocker.
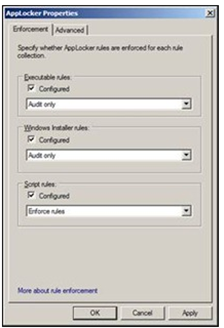 On the Enforcement tab, you have to choose which rules you want to enable.
On the Enforcement tab, you have to choose which rules you want to enable.
You will have two options – Audit Only and or Enforce Rules.
It is HIGHLY RECOMMENDED that any initial deployment of AppLocker is set to Audit Only. This will create log entries in the event log, located under Application and Services Logs – > Microsoft – > Windows, click AppLocker.
Use this log to view how your rules are behaving before making any enforcement is enabled.
In my next posting, I’ll share some examples of how to use AppLocker for both individual and enterprise use.