How to Securely Configure the SCCM 2007 Management Pack for SCOM 2007
Written by Nicolas Pasquali, Microsoft Premier Field Engineer
The Microsoft System Center Configuration Manager 2007 (ConfigMgr) Management Pack for System Center Operations Manager 2007 helps administrators manage and administer Configuration Manager 2007 servers. It’s a powerful tool for monitoring the health of your IT infrastructure which is available as a free download here. Like many other management packs this one needs to be set up and tuned.
Microsoft System Center Operations Manager (SCOM) and Configuration Manager (SCCM) administrators that wish to follow security best practices (i.e. the low privilege scenario) may have experienced some difficulties when granting the agent action account permissions on SMS WMI Classes (highlighted below) at the class level as stated in the following TechNet article: Deploying the Operations Manager 2007 Agent. Here’s a summary of the article’s instructions:
Resource |
Access Type |
Instructions |
Windows Event Log |
Read |
The Action Account must be given the Manage auditing and security log privilege using Local or Global Policy. |
SMS registry keys |
Read |
HKLM\Software\Microsoft\SMS Add the Action Account to the registry properties and provide read access that is inherited by all subkeys. |
Win32 Services registry keys |
Read |
HKLM\System\CurrentControlSet\Services Add Action Account to the local users group. |
Script generated temp files |
Read and Write |
The path specified by the TMP variable for the Action Agent. For Local System this is %Windir%\Temp Add the Action Account to the local users group. |
SMS log files |
Read |
<ConfigMgrInstallFolder> \Logs Add the Action Account to the folder properties. |
WMI namespaces |
Read |
root and root\cimv2 No action should be required. |
SMS WMI namespaces |
Read |
No action should be required. |
SMS WMI classes |
Read |
SMS_Site SMS_R_System SMS_SiteControlFile SMS_ProviderLocation SMS_SCI_SiteDefinition SMS_SystemResourceList SMS_SystemResourceList SMS_SiteSystemSummarizer Add the Action Account to the class for all instances |
Security login rights to the default instance |
Grant access |
For the default instance on a managed SQL Server computer, the Action Account must be given Grant access rights for security logins. In SQL Server Enterprise Manager, add the Action Account to the following node: instancename\Security\Logins. |
Access to the Master database on the default instance (required to identify the SMS Site database) |
Permit |
For the default instance on a managed SQL Server computer, the Action Account must be given permit access to the Master database. In SQL Server Enterprise Manager, add the Action Account to the following node: instancename\Databases\Master\Users. Keep all default permissions associated with this new user. |
Access to the SMS Site database on the default instance |
Permit |
For the default instance on a managed SQL Server computer, the Action Account must be given permit access to the SMS Site database. In SQL Server Enterprise Manager, add the Action Account to the following node: instancename\Databases\< Keep all default permissions associated with this new user. |
To correct any difficulties you might experience, grant the agent action account the required permissions by following these simple instructions:
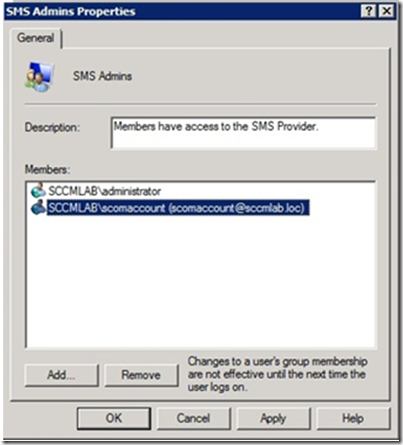
1. Add the OpsMgr Agent Action Account in the SMS Admins group of the monitored site server.
- Impacted class : SMS_ProviderLocation
- Impacted class : SMS_SystemResourceList
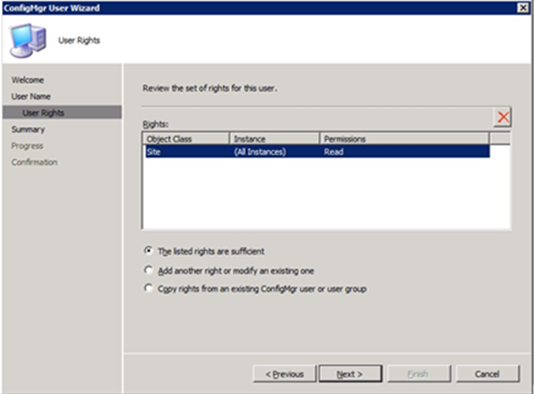
2. Add a “class security right” for the OpsMgr Agent Action Account on the class SITE, rights : READ in the ConfigMgr console.
- Impacted class : SMS_Site
- Impacted class : SMS_SiteControlFile
- Impacted class : SMS_SCI_SiteDefinition
- Impacted class : SMS_SiteSystemSummarizer
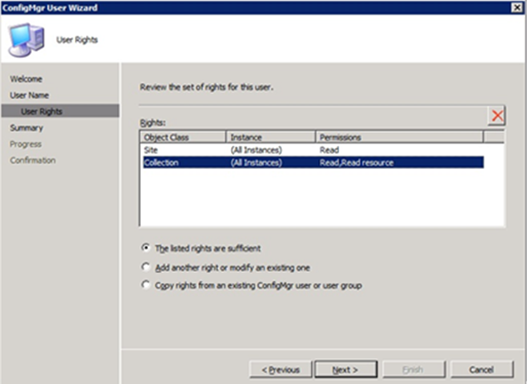
3. Add a “class security right” for the OpsMgr Agent Action Account on the class COLLECTION, rights : READ, READ RESOURCE in the ConfigMgr console
- Impacted class : SMS_R_System
That’s it!