Use the OMS log search feature to report on custom OMS alerts
Summary: Learn how to use Microsoft Operations Management Suite log search to report on the results of custom OMS alerting.
This post is the fifth post in a multi-part series of blog posts about OMS alerting. To fully understand this post, you should read the entire series in order.
Here are the posts in the series:
- OMS alerting is now generally available
- Learn how to get started using OMS alert management
- Use OMS to create alerts for missing security and other updates
- Set up an Operations Management Suite alert that detects suspicious executables
- Use the OMS log search feature to report on custom OMS alerts
Good morning everyone, Ed Wilson here, and today I want to talk about the capabilities of Microsoft Operations Management Suite to search for alerts that OMS alerting generates.
Search for alerts
It probably comes as no surprise that I can use the OMS search capabilities to search for alerts. The cool thing is that the new custom alerts that I created can also be identified and searched for. The thing that is great is that I can then report on how many alerts are generated in a certain time frame, and even which of my custom alerts generated the alert.
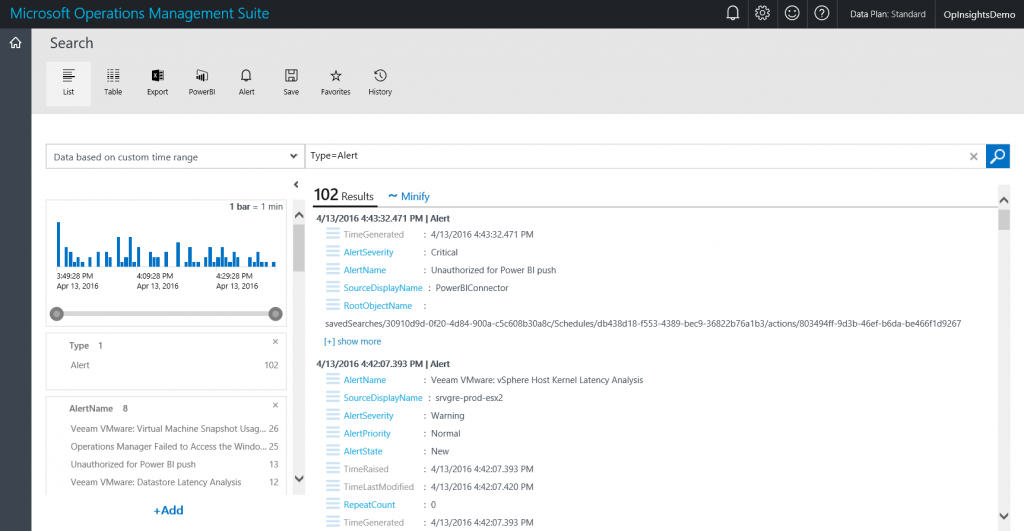
So, if I want to search for alerts, I set the type of alert. This is shown here:
Type=Alert
There are all kinds of alerts. The generic alert query and output is shown here:
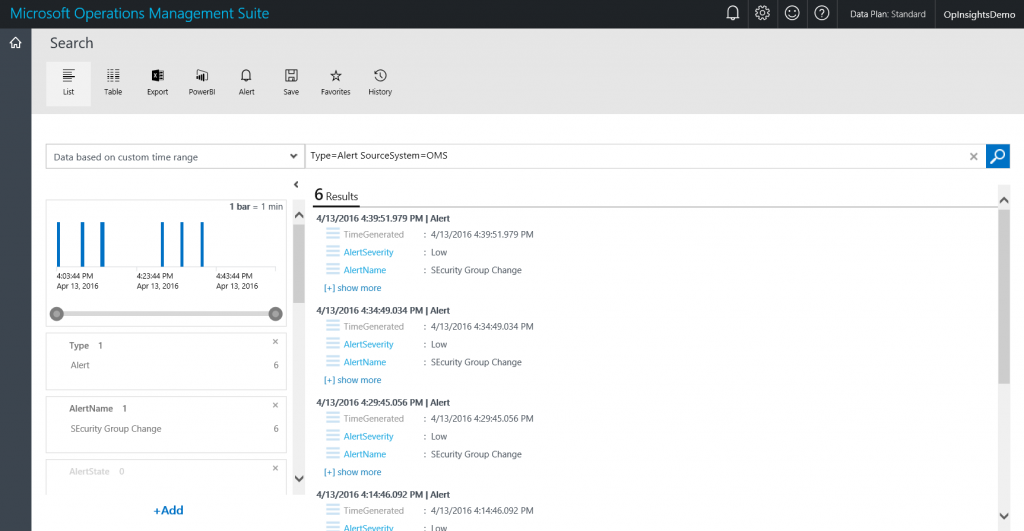
If I want to find my custom OMS alerts, I add a source for the alert. To do this, I use the SystemSource keyword and specify that it comes from OMS. This query is shown here:
Type=Alert SourceSystem=OMS
The query and output is shown in the figure here:
After I know how to find my custom OMS alerts, then I can add filters to the search string to drill into the alert results.
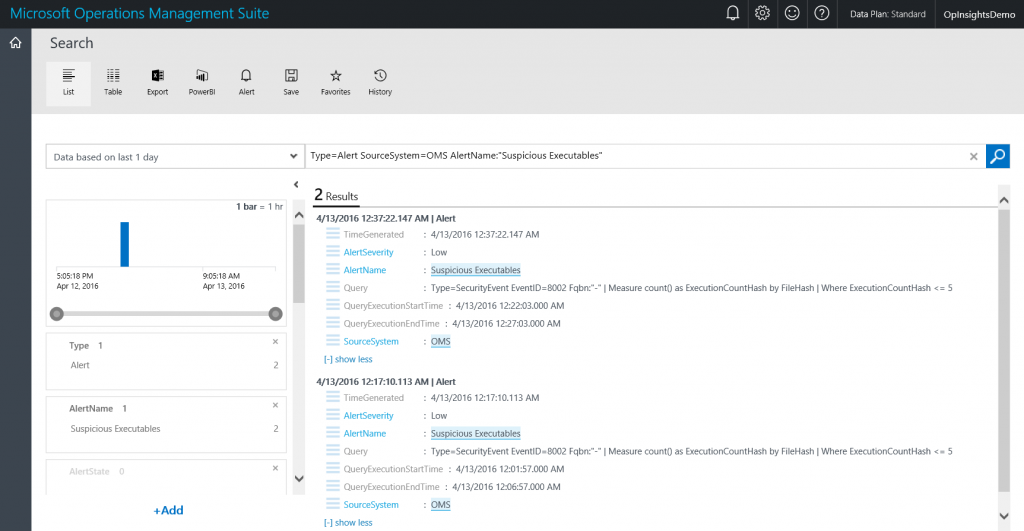
For example, if I want to drill into my Suspicious Executables query that I wrote yesterday, I add the AlertName parameter and set it equal to “Suspicious Executables”.
NOTE: This is, in my mind, a good reason to avoid spaces in alert names.
So, the query that I create is shown here:
Type=Alert SourceSystem=OMS AlertName:"Suspicious Executables"
The query and the output from the query is shown here:
One of the great things about this query is that it returns the query that was executed to create the alert in the first place. This is a good troubleshooting technique.
You can get a free Microsoft Operations Management Suite (#MSOMS) subscription so that you can test the new alerting features. You can also get a free subscription for Microsoft Azure as well.
That is all I have for you today. Join me next week when I will have more cool OMS stuff.
I invite you to follow me on Twitter and the Microsoft OMS Facebook site. If you want to learn more about Windows PowerShell, visit the Hey, Scripting Guy Blog. If you have any questions, send email to me at scripter@microsoft.com. I wish you a wonderful day, and I’ll see you tomorrow.
Ed Wilson
Microsoft Operations Management Team