Locking up Your BitLocker
Hello,
Today I want to talk about securing your Bitlocker-enabled devices against a common attack vector: Direct Memory Access/Side channel attack.
BitLocker quick overview
First, a little primer on how BitLocker works is in order
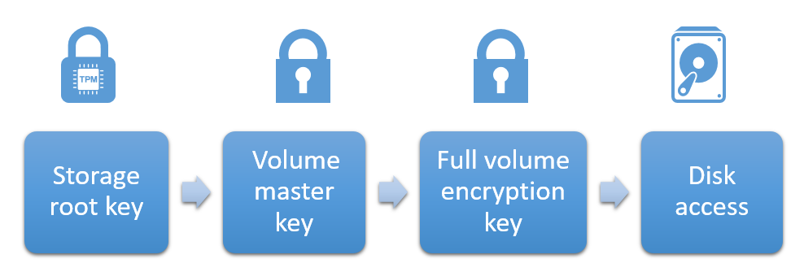
Trusted Platform Module (TPM) is a hardware security device that stores a master key, or Storage Root Key (SRK), and Platform Configuration Registers (PCRs) for a given computer.
Upon starting, the TPM checks various startup components, which can include the MBR and Boot Loader of the hard drive, to verify that the computer has same values when it did the shut down
and then provides the SRK to the system.
SRK is then used to decrypt the Volume Master Key (VMK) which is stored on an unencrypted partition for each volume.
Once the VMK is decrypted, it’s then being used to decrypt the File Volume Encryption Key (FVEK), which is then used to decrypt the data on the encrypted drive.
- Storage Root Key is stored in the TPM
- Volume Master Key is stored in the volume metadata
- File Volume Encryption Key is also stored in the volume metadata (OEM vendor string)
There are few well-known attacks vectors against these keys, this blog post will be focused on Direct Memory Access attacks.
Direct Memory Access
So, what’s Direct Memory Access? Direct Memory Access (DMA) allows certain hardware devices to communicate directly with a system memory (RAM) and thus improving the performance. These devices are including FireWire, CardBus, ExpressCard, Thunderbolt, PCI, and PCI Express.
To perform a DMA attack, attacker is typically using a special software to utilize a device that supports Direct Memory Access from a second PC, and when connected he can obtain full memory dump that contains the encryption key among other stuff. This is the way most BitLocker recovery toolkits are working.
Countermeasures against Direct Memory Access attacks
This guidance is updated to Windows 10 1703 “Creators Update”.
I recommend on testing carefully and apply the following:
UEFI Level
- Prevent the ability to boot from anything but your primary hard drive
- Enable a firmware password to prevent changing boot settings
- Disable unneeded external DMA interfaces
Windows Level
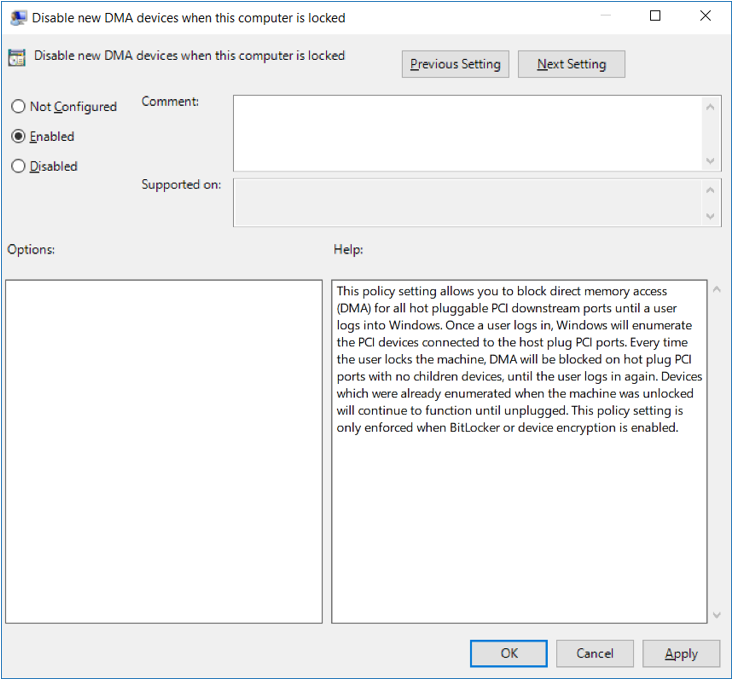
- Block direct memory access (DMA) for all hot pluggable PCI downstream ports until a user logs into Windows (Windows 10)
- GPO Setting Location: Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\ (disableExternalDMAUnderLock)
Block the SBP-2 driver and Thunderbolt controllers: https://support.microsoft.com/en-us/help/2516445/blocking-the-sbp-2-driver-and-thunderbolt-controllers-to-reduce-1394-dma-and-thunderbolt-dma-threats-to-bitlocker
Disable standby states mode and enable Hibernation instead (make sure that the Hyberfil.sys is stored on the encrypted volume)
Configure Protectors:
- TPM Only – protects against stealing the hard drive or offline access
- The computer is as secure as your Windows installation and configuration (strong lockout policies, strong passwords, local firewall policies, patches and running as non-admin)
- Recommended for tablets, laptops (without DMA ports), devices with integrated RAM
- TPM+PIN - Adds pre-boot authentication, BitLocker will not load the encryption keys before a valid PIN has been provided
- Recommended for highly secure devices, desktops, laptops (with DMA ports)
- Prefer to use Enhanced PIN
- Deployments that include fixed-location workstations may prefer to use BitLocker Network Unlockas an alternative to a PIN
- TPM Only – protects against stealing the hard drive or offline access
Additional reading:
- Blocking the SBP-2 driver and Thunderbolt controllers to reduce 1394 DMA and Thunderbolt DMA threats to BitLocker: https://support.microsoft.com/en-us/help/2516445/blocking-the-sbp-2-driver-and-thunderbolt-controllers-to-reduce-1394-dma-and-thunderbolt-dma-threats-to-bitlocker
- Protect BitLocker from Pre-Boot Attacks: https://technet.microsoft.com/en-us/library/dn632180(v=ws.11).aspx