New cybersecurity report details risk of running unsupported software
Posted by Tim Rains
Director, Trustworthy Computing, Microsoft
On Tuesday, Trustworthy Computing released volume 15 of the Microsoft Security Intelligence Report, which provides threat intelligence and analysis of cyber threats in over 100 countries/regions worldwide.
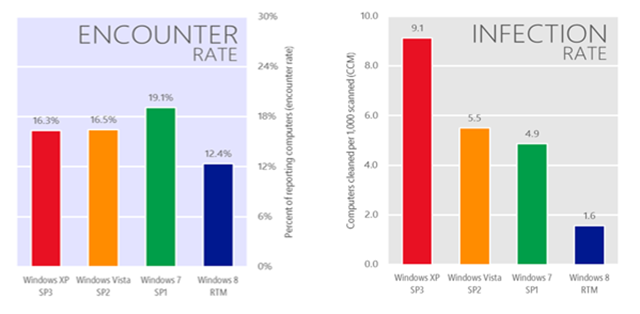
Among the numerous key findings in the new report, one of the more interesting things to surface was the increased risk of using unsupported software. The report found that in the first half of 2013, nearly 17 percent of computers worldwide that run Microsoft real-time security products encountered malware that tried to get on or stay on those systems, but Microsoft anti-malware products blocked this from happening.
What’s interesting is the difference between encountering malware and actually being infected by it. During the first half of 2013, currently supported versions of Windows desktop operating systems (Windows XP, Windows Vista, Windows 7 and Windows 8) all had roughly similar malware encounter rates – between 12 and 20 percent. But Windows XP systems had an infection rate that was six times higher than Windows 8.
The findings emphasize the positive impact security innovations and technologies in newer software are having to better help protect against cybercriminals and the importance of upgrading to a more modern operating system. More modern operating systems, include advanced security technologies that are specifically designed to make it harder, more complex, more expensive, and, therefore less appealing to cybercriminals to exploit.
Microsoft Windows XP was released almost 12 years ago, which is an eternity in technology terms. While we are proud of Windows XP’s success in serving the needs of so many people for more than a decade, inevitably there is a tipping point where dated software and hardware can no longer defend against modern day threats and increasingly sophisticated cybercriminals.
Since the launch of Windows XP, the number of people using the Internet has grown from 360 million to more than 2.4 billion. We have witnessed the rise of the Internet citizen with members of society connected through email, instant messaging, video-calling, social networking and a host of Web-based and device-centric applications. As the Internet becomes more and more woven into the fabric of society, it has also become an increasingly popular destination for malicious activity. In 1991, there were about 1,000 forms of malware or threats known to exist. Today, that number is in the millions. Today’s cybercriminals aren’t the hobbyists we saw developing malicious software from their basements in the 1990s. Cybercriminals today are no longer motivated by fame and notoriety; they are well funded underground organizations, often with advanced capabilities that include large-scale malware automation, who are motivated by profit or seek to cause real financial or political harm.
On April 8 2014, support will end for Windows XP. This means Windows XP users will no longer receive security updates, non-security hotfixes or free/paid assisted support options and online technical content updates. After end of support, attackers will have an advantage over defenders who continue to run Windows XP. After April next year, when we release monthly security updates for supported versions of Windows, attackers will try and reverse engineer them to identify any vulnerabilities that also exist in Windows XP. If they succeed, attackers will have the capability to develop exploit code to take advantage of them. 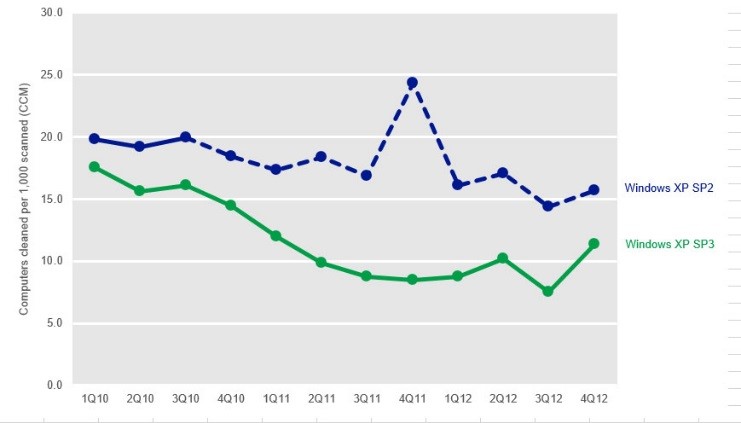
We have already had a glimpse into what happens when a Windows XP-based platform goes out of support. In the two years after Windows XP Service Pack 2 went out of support, its malware infection rate was 66 percent higher than Windows XP Service Pack 3 - the last supported version of Windows XP. As past Microsoft Security Intelligence Reports have shown, running a well-protected solution means regularly applying security updates for all software installed on the system (including Oracle Java, Adobe products and others), running real-time anti-malware software, and using the latest versions of software that have modern security technologies and mitigations and benefit from ongoing support.
For more information, or to learn about other key findings in the new Security Intelligence Report, I encourage you to visit www.microsoft.com/sir.