Disable NLA via Custom Script Extension
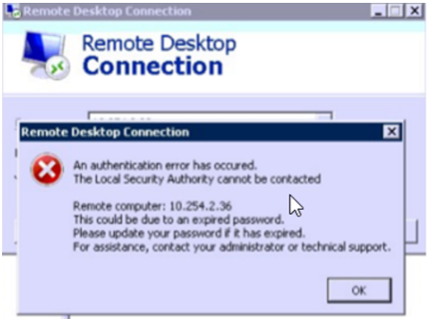
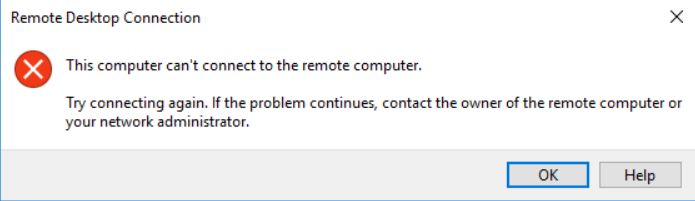
Symptoms: When attempting to RDP to your virtual machine you receive an error regarding Network Level Authentication (NLA):
Resolution:
Note: The below steps are using Custom Script Extension in the Azure Portal. If that is not an option as the Guest Agent is not responding you can also run the same commands via Remote PowerShell, PSExec or make the changes via Remote Registry.
1) Open up a Blank Notepad and paste the following into it:
Set-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "SecurityLayer" -value 0
Set-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "UserAuthentication" -value 0
Set-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "fAllowSecProtocolNegotiation" -value 0
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server' -name "fDenyTSConnections" -Value 0
2) Save the file as disableNLA.ps1
3) Navigate to the Azure Portal
4) Select the impacted VM
5) Select extensions
6) Select Add
7) Select Custom Script Extension
8) Select Create
9) Select the disableNLA.ps1 created in the previous steps
10) Install the .ps1 file. No arguments are needed.
11) Go back to the extensions tab and wait for the Custom Script to report as successful
12) Attempt to RDP to the machine. If it fails, restart the VM and attempt to RDP to it again.