Custom RBAC Management Roles–Part 2
In a previous post, I explained how to create a Custom RBAC role which removes certain abilities from the Administrative team. A comment was posted asking how to do the opposite, and create a role group with only certain cmdlets available, for an application to manage mobile devices. Here is the request:
Could you please assist me to create a new RBAC role group with permissions to the below powershell cmd-lets? Get-MailboxGet-CASMailboxGet-ActiveSyncDeviceStatisticsSet-CASMailboxClear-ActiveSyncDevice (Remote Wipe)Remove-ActiveSyncDeviceGet-ActiveSyncMailboxPolicySet-ActiveSyncMailboxPolicyNew-ActiveSyncMailboxPolicyRemove-ActiveSyncMailboxPolicyGet-MailboxServerGet-ActiveSyncOrganizationSettings |
The first step in working on this, is choosing the appropriate parent management roles. Now, all custom management roles must be based on a parent role, and cmdlets and parameters can be removed in the child role. Cmdlets which do not exist in the parent role, cannot be added later. Therefore, we must begin by finding which Built-in management roles contain these cmdlets. This can be done with the Get-ManagementRoleEntry cmdlet.
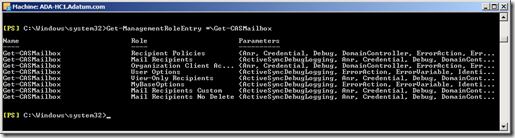
For each cmdlet above, we run Get-ManagementRoleEntry *\CmdletName which will give us an output like so
By repeating this command for all of the above cmdlets, we can see that we will need to create custom versions of the following built in role groups
- Mail Recipients
- Recipient Policies
- Exchange Servers
- Organization Client Access
From here, we can create child groups based on these parent roles, using the New-ManagementRole cmdlet.
We run four commands, to create our groups.
- New-ManagementRole “Mail Recipients Mobile Devices” –Parent “Mail Recipients”
- New-ManagementRole “Recipient Policies Mobile Devices” –Parent “Recipient Policies”
- New-ManagementRole “Exchange Servers Mobile Devices” –Parent “Exchange Servers”
- New-ManagementRole “Organization Client Access Mobile Devices” –Parent “Organization Client Access”
Now we have our Custom Roles created, (with descriptive names so we know later what they are for) we can start to remove the unwanted cmdlets.
To do this, we use the syntax posted in the last blog post.
Get-ManagementRole "Recipient Policies Mobile Devices" | Get-ManagementRoleEntry | Where {$_.Name -like "Get-DetailsTemplate”} | Remove-ManagementRoleEntry
We repeat this for all the unwanted cmdlets in all four new groups
We can then create our custom Role Group, containing these four new management roles.
To start, we run “New-RoleGroup “Mobile Device Management” to create the role group.
Then we can run New-ManagementRoleAssignment –SecurityGroup “Mobile Device Management” –Role “Mail Recipients Mobile Devices” to assign the new management role to the role group. We then repeat this for the remaining four roles.
We now have a role group created with a custom set of RBAC permissions. This should be fully tested in the lab to ensure that the service account for the mobile device software is able to run sufficiently using these permissions. These steps can be used to create other custom role groups if needed.