Identify Yourself - One or Two Passwords?
To be allowed into Office 365 a user needs to be authenticated. Authentication means verifying that the user is who he/she claims to be. Once authenticated we can decide what actions the user is authorized to perform in Office 365.
Identity management deals with identifying individuals in a system and controlling access to the resources in that system.
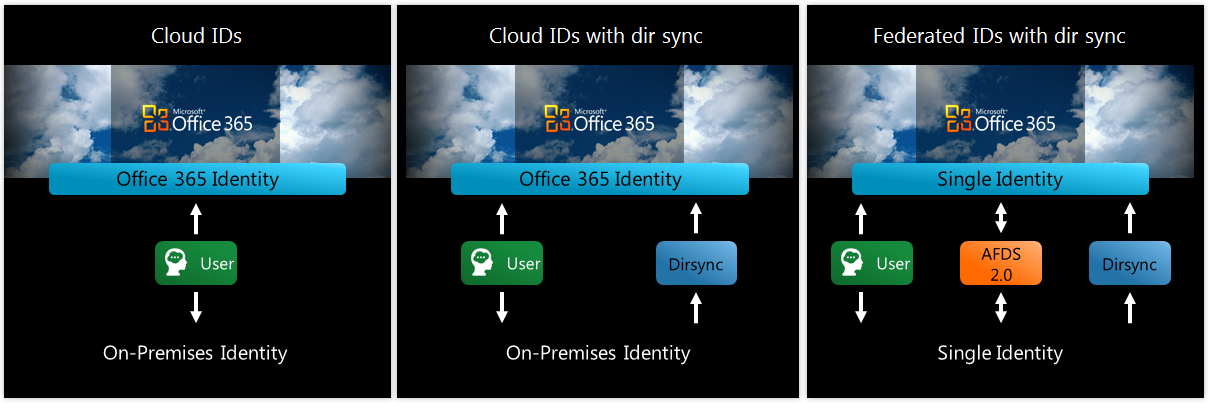
In Office 365 we support three core customer scenarios for identity management:
- Cloud IDs
suitable for organizations without on-premises active directory
- Cloud IDs with directory synchronization
suitable for organizations with on-premises active directory
- Federated IDs with directory synchronization
suitable for organizations with on-premises active directory that need single sign-on
Different benefits and limitations exist for these three core scenarios (see also 'Key terminology' at the end of this article):
1. Cloud IDs
With Microsoft Online Services cloud IDs (Cloud Identity), user credentials for signing into Office 365 services are stored in the cloud
Benefits
- Ease of deployment, management and support if there is no On-Premises deployment
- No additional servers required On-Premises
Limitations
- Separate credentials for Online Services
- Separate Password policies for On-Premises and Online applications
- No two factor authentication
- No Single Sign-on to Services On-Premises and Online
2. Cloud IDs with directory synchronizationFor larger organizations that may want to streamline provisioning, the Microsoft Online Services Directory Synchronization Tool can be used to replicate existing Active Directory user accounts (and other Active Directory objects) into the Office 365 Cloud ID. Unlike manually created accounts, accounts created by the Directory Synchronization Tool are fully populated with user account information from Active Directory (for example, department, and phone number).
Benefits
- Directory synchronization between On-Premises and Online
- Objects are mastered On-Premises
- Reuse existing directory implementation On-Premises
- Third party password synchronization possible
Limitations
- Additional Server for Directory Synchronization
- No Two factor authentication
- No Single Sign-on to Services On-Premises and Online
- No native password synchronization
- Requires FIM for Multi-forest AD
3. Federated IDs with directory synchronization
Federated IDs (Federated Identity) is a more sophisticated approach for larger organizations. In companies with Federated Identity set up, users can sign into Office 365 services using their Active Directory credentials. The corporate Active Directory authenticates the users, and stores and controls the password policy. With federated Identity, credentials are authenticated by on premises Active Directory Federation Services 2.0 server and a logon token is obtained by the user so that the Office 365 sign-in service can verify them. While this model may require some server investments and deeper architectural decision making, it does allows support for richer single sign on with your corporate credentials, integration with on-premises multi-factor authentication and a configurable password policy.
Benefits
- Identities mastered On-Premises with federation to Office 365
- Single Sign-on for On-Premises AD and Office 365 Services
- Client access control based on IP address
- Dual Factor Authentication for additional security
Limitations
- Requires AD FS
- Requires Directory Synchronization
- Require FIM for Multi-forest AD On-Premises
- Additional Servers On-Premises for DirSync and ADFS
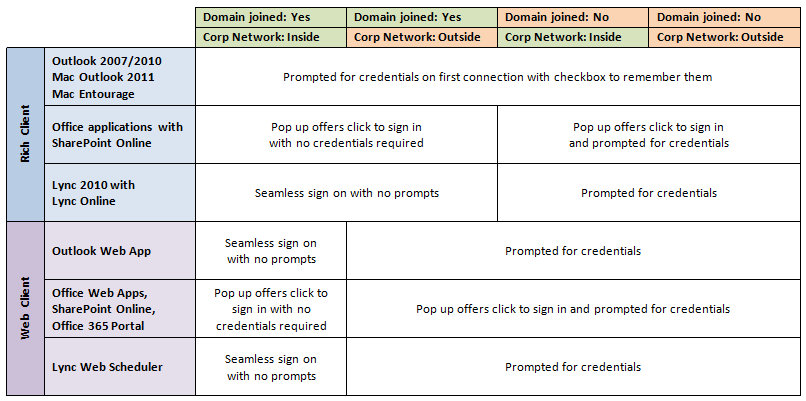
Sign-On Experience with Federated ID
End-users can use their AD credentials to access online resources, through ADFS. The experience they have will vary depending on the client types, access methods (inside or outside corporate network) and whether the device has joined the domain
See the Office 365 Identity Service Description "Signing In to Office 365" section for more information
To learn more about these Identity Management options you can go to the Office 365 Community Wiki “Office 365 Identity Management”
Key terminology
- Single sign-on (SSO): We define Single Sign-On (SSO) as the ability for customers to use a single set of credentials to access both on-premises and online resources. This single set of credentials is managed in the customer’s Active Directory, and requires Active Directory Federation Services.
- Active Directory Federation Services (ADFS) : AD FS is an identity access solution that provides browser-based and rich clients (internal or external to your network) with seamless, "one prompt" access to one or more applications, even when the user accounts and applications are located in completely different networks or organizations. Active Directory Federation Services (AD FS) 2.0 helps simplify access to applications and other systems with an open and interoperable claims-based model. AD FS 2.0 provides support for claims-aware identity solutions based in interoperable standards for federation (WS –Trust, WS-Federation and Security Assertion Markup Language (SAML). AD FS 2.0 is integrated with Windows Server® and is dependent on Active Directory Domain Services for authenticating users. AD FS can be used to provide users with access to internal applications as well as those hosted externally at partners or in different cloud providers that support any of the federation standards.
- Active Directory Synchronization (DirSync) : The Microsoft Online Services Directory Synchronization tool maintains two-way directory synchronization of all user accounts and mail-enabled contacts and groups from your local Active Directory to Microsoft Online Services.
- Secure Token Service (STS) : Secure Token Service is a web service that issues tokens in a given Security domain
See also