Cross-Forest Free Busy with Shared Namespace
I’ve come across with certain implementations of Cross-Forest Availability service referring online documentations on this subject which includes a well written blog: How to Configure the Availability Service for Cross-Forest Topologies and a TechNet article: Configure the Availability Service for Cross-Forest Topologies. Being these articles talks all in and out of setting-up Availability service in Cross Forest environments, However, I thought of posting a content which talks specifically on setting-up Cross-Forest Availability service with Shared Namespace.
Think of a scenario where an organization is planning to migrate its users from an existing Exchange forest to newly created Exchange forest with the same SMTP address. There may probably be several scenarios as well based on business requirements, but this is the one from the common scenarios.
How to set-up:
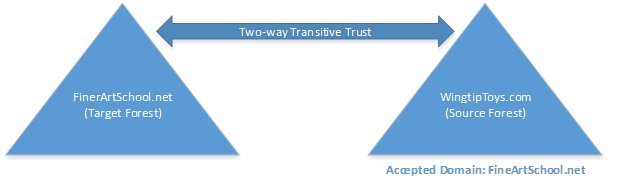
- Trusted Forests:
- A unique SMTP domain name as an Accepted domain in any of the two forests since Autodiscover of shared domain can only point to one Exchange forest at a single time. For an instance, we have the two forests Fineartschool.net and Wingtiptoys.com. Fineartschool.net is a domain which is to be shared between these two forests and WingtipToys.com is a unique SMTP domain. And adding, Fineartschool.net as an Authoritative Accepted Domain to Wingtiptoys.com (Not discussing mailflow for now).
-
- Export Autodiscover configuration from target forest to source forest. In this case, export the Autodiscover configuration from Fineartschool.net to Wingtiptoys.com using below shell command:Export-AutoDiscoverConfig -TargetForestDomainController <TargetForestDomainControllerName> -TargetForestCredential (Get-Credential)
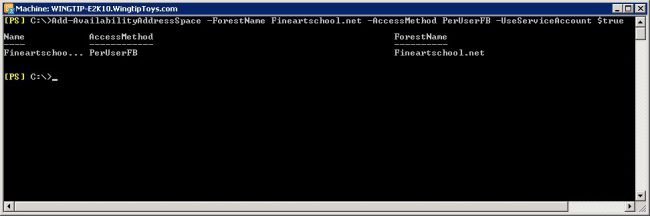
For more information, please visit: Export-AutodiscoverConfig. - AvailabilityAddressSpace of shared domain must be added in the source forest with an AccessMethod PerUserFB. Here in this case for an example, AvailabilityAddressSpace has been added in Wingtiptoys.com for Fineartschool.net.
- Export Autodiscover configuration from target forest to source forest. In this case, export the Autodiscover configuration from Fineartschool.net to Wingtiptoys.com using below shell command:Export-AutoDiscoverConfig -TargetForestDomainController <TargetForestDomainControllerName> -TargetForestCredential (Get-Credential)
-
- Source forest’s Client Access Servers must have token serialization permissions on the target forest’s Client Access Servers. The same can be set using below shell command on target forest.
Get-ClientAccessServer | Add-ADPermission -AccessRights extendedright -ExtendedRights "ms-exch-epi-token-serialization" -User "<sourceforest\Exchange Servers>"
-
- Mail contacts of target forest users in the source forest must have an ExternalE-mailAddress stamped with a shared SMTP suffix. In this case it would be Fineartschool.net. For example, user’s mail contact has ExternalE-mailAddress FinUser1@fineartschool.net.
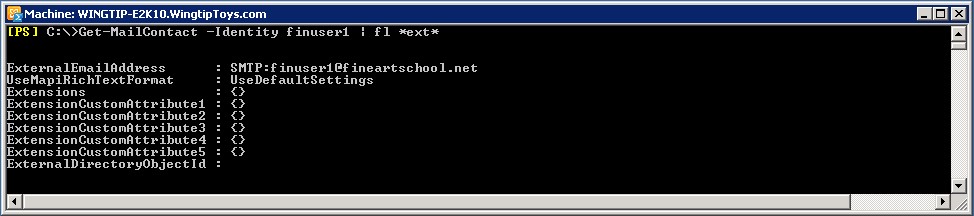
- Mail contacts of target forest users in the source forest must have an ExternalE-mailAddress stamped with a shared SMTP suffix. In this case it would be Fineartschool.net. For example, user’s mail contact has ExternalE-mailAddress FinUser1@fineartschool.net.
-
- And, a pre-defined HTTP Autodiscover URLs for respective SMTP domains including unique SMTP domain must have a SSL certificates and root of it must be trusted by both the forests.
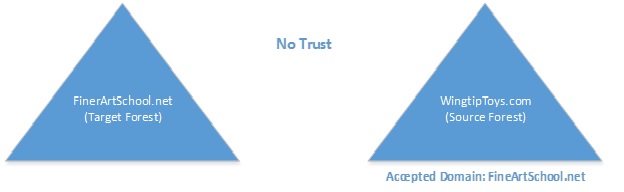
Untrusted Forests:
- Exchange Web Services must have an ExternalURL set on its virtual directories.
- Outlook Anywhere must be enabled in an Exchange environment so that Autodiscover pulls up HTTP URLs for outside users to connect.
- A unique SMTP domain name as an Accepted domain in any of the two forests since Autodiscover of shared domain can only point to one Exchange forest at a single time. For an instance, we have the two forests Fineartschool.net and Wingtiptoys.com. Fineartschool.net is a domain which is to be shared between these two forests and WingtipToys.com is a unique SMTP domain. And adding, Fineartschool.net as an Authoritative Accepted Domain to Wingtiptoys.com.
-
- Autodiscover URL for a shared domain must have an external DNS “A” record and pointed to an operational IP address of the target forest Exchange environment so that source forest can resolve it to an Autodiscover endpoint in the target forest
- AvailabilityConfig in the target forest to be configured with an account which will be used for authenticating the Exchange Web Service requests towards the target forest. For an example, setting up AvailabilityConfig in Fineartschool.net with a local account named as “FB” (This account can be a low privileged account only with ‘Domain Users’ group membership). Below is the shell command is to achieve the same:Set-AvailabilityConfig –OrgWideAccount <Domain\Username>
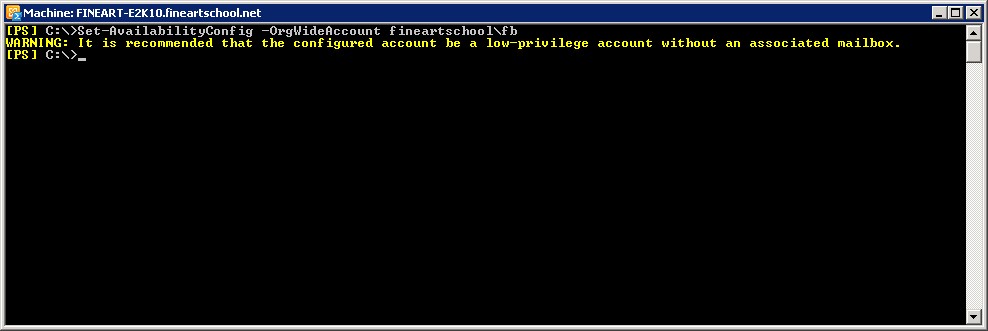
AvailabilityAddressSpace of shared domain must be added in the source forest with an AccessMethod OrgWiderFB with the credentials of the user configured in the target forest’s AvailabilityConfig . Here in this case for an example, AvailabilityAddressSpace has been added in Wingtiptoys.com for Fineartschool.net.
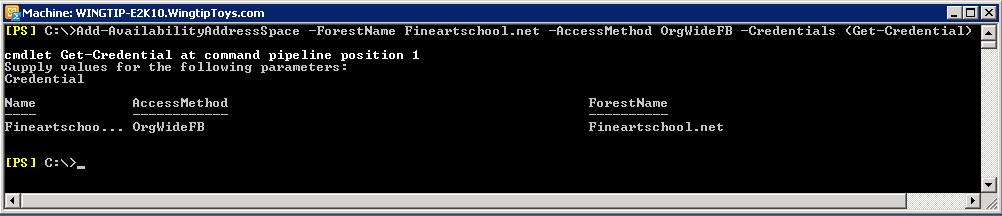
-
- Mail contacts of target forest users in the source forest must have an ExternalE-mailAddress stamped with a shared SMTP suffix. In this case it would be Fineartschool.net. For example, user’s mail contact has ExternalE-mailAddress FinUser1@fineartschool.net.
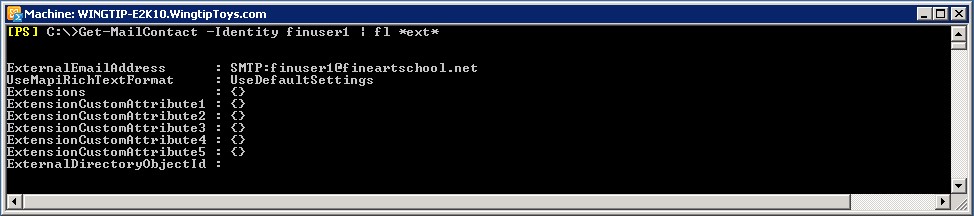
-
- And, a pre-defined HTTP Autodiscover URLs for respective SMTP domains including unique SMTP domain must have a SSL certificate installed on the target forest’s Client Access Servers and root of it must be trusted by both the forests.
NOTE: ExternalE-mailAddress of a mail contact must be stamped with a shared SMTP suffix in the source forest since Availability Service attempts Autodiscover initially which primarily looks at ExternalE-mailAddress of a mail contact. If it isn’t unique from default domain of source forest, it will again attempt to see the Primary SMTP Address of the mail contact.
How it works:
- In Trusted scenarios,
Here,
Target Forest: Fineartschool.net, User: FinUser1
Source Forest: Wingtiptoys.com, Accepted Domain: Fineartschool.net, User: FinUser2
Important: There may be some situations like new implementation of another Exchange forest where there are chances to may have same domains in both the forests. In those cases, it is required to have a unique domain which should be added as an accepted domain in any of the forests because Autodiscover can point to only one forest at a time.
-
- FinUser2 in source forest pulls up the free/busy information of FinUser1 which resides in Fineartschool.net (Target Forest).
- Request goes to a Client Access Server in source forest and it resolves it to a mail-contact of FinUser1.
- Availability Service looks at the ExternalEmailAddress of mail-contact of FinUser1 which is stamped with FinUser1@Fineartschool.net and tries to find the matching AvailabilityAddressSpace.
- If it finds the matching AvailabilityAddressSpace in source forest then looks at the AccessMethod of AvailabilityAddressSpace for Fineartschool.net which is set to PerUserFB.
- Here, Availability service realizes that it is a Trusted Forest proxy call, Availability Service initiates making the Autodiscover call and looks for Service Connection Point in Target Forest.
- It’ll do the DNS lookups for the LDAP URL (which was exported to source forest) using Export-AutodiscoverConfig) and will search for Kerberos service records in the target forest. In response it resolves the LDAP path and sends Kerberos ticket request to KDC of target forest.
- It gets the Kerberos service key, with a use of which it makes a LDAP call to find the Autodiscover endpoint and likewise then makes an Autodiscover call to target forest’s Autodiscover SCP and yanks the EWS ExternalURL.
- Now, EWS ExternalURL has been sent in a response by the target forest’s Client Access Servers and source forest’s Client Access Servers will check if they have Token Serialization permissions or not on target forest’s Client Access Servers. If it’s there then it returns the Free/Busy information.
In Untrusted scenarios,
Here,
Target Forest: Fineartschool.net, User: FinUser1
Source Forest: Wingtiptoys.com, Accepted Domain: Fineartschool.net, User: FinUser2
Important: There may be some situations like new implementation of another Exchange forest where there are chances to may have same domains in both the forests. In those cases, it is required to have a unique domain which should be added as an accepted domain in any of the forests because Autodiscover can point to only one forest at a time.
-
- FinUser2 in Source Forest pulls up the free/busy information of FineUser1 which resides in Fineartschool.net (Target Forest).
- Request goes to a Client Access Server in Source Forest and it resolves it to a mail-contact of FinUser1.
- Availability Service looks at the ExternalEmailAddress of mail-contact of FinUser1 which is stamped with FinUser1@Fineartschool.net and looks for matching AvailabilityAddressSpace.
- If it finds the matching AvailabilityAddressSpace in a Source Forest, it looks at the AccessMethod of that AvailabilityAddressSpace which is set to OrgWideFB.
- Here, Availability service realizes that it is an Untrusted Forest proxy call, it initiates the Autodiscover call and tries to resolve Autodiscover.Fineartschool.net using DNS method and resolves to an external host “A” record.NOTE: Autodiscover of shared domain named must be pointed to an IP Address of an operational Client Access Server in target forest. Being this is an untrusted scenario, external DNS ‘A’ record is required for Autodiscover.Fineartschool.net.
- Once it is able to resolve and discovers an Autodiscover endpoint in target forest, it now makes Autodiscover call to Client Access Servers Fineartschool.net and pulls up the EWS ExternalURL of target forest.
- Now, EWS ExternalURL will be sent in a response by the Fineartschool.net Client Access Servers to source forest Client Access Servers post authenticating the request with the Service Account configured in AvailabilityConfig. Availability service will then connect to EWS URL returned and returns the Free/Busy information.
Related Reading(s): Configure the Availability Service for Cross-Forest Topologies How to Configure the Availability Service for Cross-Forest Topologies White Paper: Understanding the Exchange 2010 Autodiscover Service Export-AutoDiscoverConfig