Managing Trusted Sites via Policy for EMET ASR
Part of the new functionality of EMET allows you to block or allow plugins in IE based on the zone that a web site is located in. The default example is the java plugin is blocked on the “Internet” zone but allowed on the “Intranet” and “Trusted” sites zones. Currently the recommendation is to use the “Trusted” sites zone for sites that are external to your organization but are sites that you require a blocked ASR plugin to function on. There are a few different ways to programmatically manage the sites that are in the trusted sites zones for your users and I will cover those here.
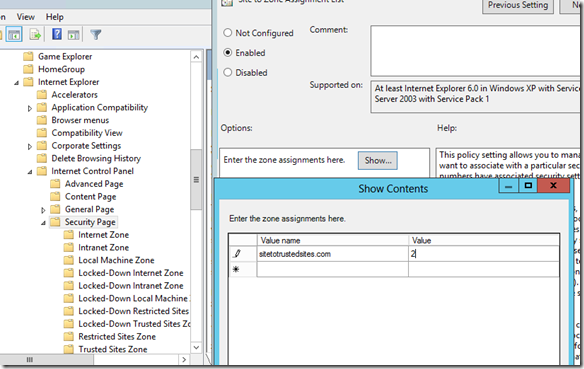
The default settings that are available in a GPO can be located at
Computer Configuration | Administrative Templates | Windows Components | Internet Explorer | Internet Control Panel | Security Page .. and by modifying the Site to Zone Assignment List
You can add sites here and put the number 2 to the right which indicates that it will be a member of the Trusted Sites zone.
While this method works well it will also completely grey out modifying the trusted sites for the users on the system removing anything they had previously and disallowing them to modify this selection any more. This may be the desired result in your environment depending on your security posture.
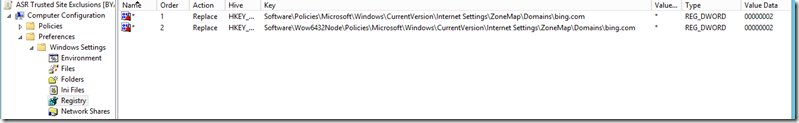
On the other hand if you want to add sites to computers regardless of user and still allow the user to modify the selection this can be accomplished via Group Policy Preferences. For reference purposes see https://support.microsoft.com/kb/182569 which labels out many of the keys and values of interest in performing this task. The first step is to create a new GPO to contain these settings, you may just want to add this to an existing GPO that is being used to configure EMET as technically it falls in the same realm. Within the GPO create 2 new registry keys for each site under Computer Configuration > Preferences > Windows Settings > Registry
The first key will be under HKLM\Software\Policies\Microsoft\Windows\CurrentVersion\InternetSettings\ZoneMap\Domains\domainname.com with a dword value named * and value data of 2
The second key will be under HKLM\Software\Wow6432Node\Policies\Microsoft\Windows\CurrentVersion\InternetSettings\ZoneMap\Domains\domainname.com with a dword value named * and a value data of 2.
Make sure you use the domain name you want and not domainname.com ![]() I’m using bing.com in my screenshot above. Also the 2 keys makes sure that we are covering both the x86 and x64 versions of IE.
I’m using bing.com in my screenshot above. Also the 2 keys makes sure that we are covering both the x86 and x64 versions of IE.
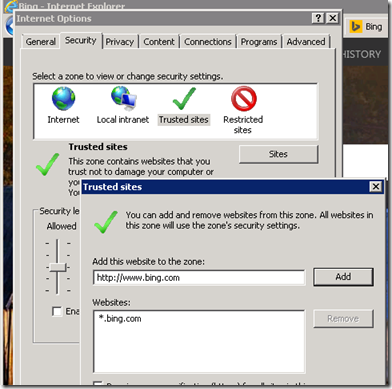
You can verify that the site was successfully added after doing a GPO refresh and checking in IE Internet Options > Security > Trusted Sites > Sites and should see something like this..
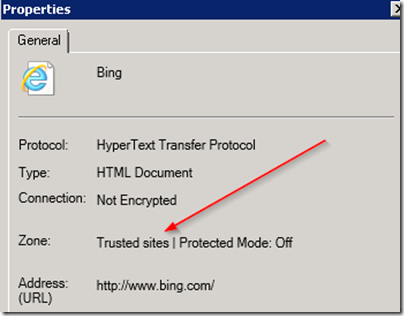
Or you could also pull up properties on the web site after visiting it by hitting Alt-F and R and hopefully see the following
The same registry keys work if you changed to HKCU and targeted user accounts instead however most org’s typically target computers for security settings such as these so I didn’t do much investigation on that part of it.
So not really an EMET post per say but functionality of the OS that you can use in conjunction with a good feature of EMET to more fully manage this setting in your organization. If you have any questions please leave them in the comments ![]() thanks
thanks
Kurt
Adding a couple of links to excellent resources that Aaron Margosis has on reg keys that control site to zone mappings as well as a tool to show on a system which sites are assigned to which zones and what is the effective policy.
https://blogs.technet.com/b/fdcc/archive/2011/09/22/iezoneanalyzer-v3-5-with-zone-map-viewer.aspx