Managing IE Sites for EMET with ASR (Attack Surface Reduction)
If you haven’t started testing EMET 5.0 please consider doing so especially if you are charged with piloting the product for your organization as this version is the latest and has more fixes and protections than are available in the 4.x platform.
One of the great new features we introduced with 5.0 is ASR or Attack Surface Reduction. ASR is a generic plugin blocker that works primarily with Internet Explorer as well as some with Office programs such as Word, Excel and Powerpoint. ASR currently is a simple yes/no type of operation where if a certain plugin is detected in a protected application ASR will not allow the specified plugin to load in the protected application.
There are 2 slight variations to ASR. For the Office Suite of applications that are protected it is a simple yes/no operation as to whether the plugin is allowed in the application. For example when a Word document is opened that contains a Flash plugin EMET will not allow the plugin to load. On the other hand ASR within Internet Explorer allows a little more variation on the yes/no operation. By default it will block plugins such as Java on the “Internet” security zone however will allow the plugin on the “Intranet” and “Trusted Sites” security zone.
So the key here is if you deploy this widely in an enterprise is how do you manage the exceptions? I.e. you have either an internal business web site or external site where you absolutely need Java to work on that website in order to get work done. In order to do this you are probably going to need to use GPO’s to manage sites into the “Trusted” sites zone or “Intranet” zone. The best way I’ve seen so far for doing this is using GPP (Group Policy Preferences) to add sites to a users Trusted Sites while still leaving whatever settings they had previous intact. Below is a process for accomplishing this:
I’m going to use www.java.com as my site as they obviously have a handy page that loads java to detect the version installed on my system. Create or modify a GPO that is applied to the users I need to allow exclusions for. Currently this is somewhat different than applying EMET policies as we normally target systems and not users. I think there is probably a way to do this via GPP for the computer object to apply to all users on a system but haven’t figured it out yet. When I do I’ll post an update to this.
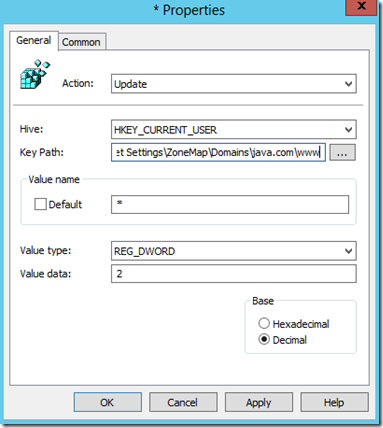
In the GPO we are going to create a new registry item under User configuration>Preferences>Windows Settings>Registry the key path we want to use will be Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\java.com\www , The “Value name” property will be * and the Value Type REG_DWORD with a data value of 2
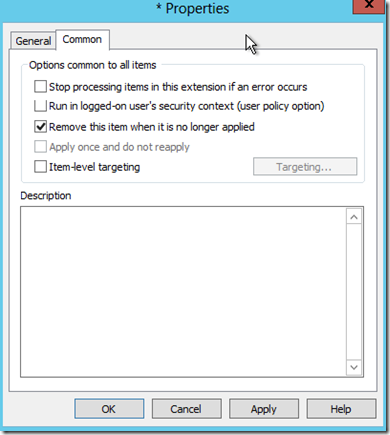
I typically like to use the “Remove this item when it is no longer applied” setting on the “Common” tab as well as this makes sure things are cleaned up in my environment if I were to remove this GPO later on.
Once I apply this GPO to my users and refresh this will add the site into my “Trusted” sites zone. The Value data of 2 specifies that the site will be placed into Trusted Sites. If I wanted the site in the “Local Intranet” zone instead I would use a Value data of 1 for the DWORD value instead. In general for Internet sites that you need to trust put them in “Trusted” sites versus sites that actually exist on your networks should be placed into “Intranet” instead.
If you have any questions or comments/suggestions please feel free to leave them in the comments below. Thanks