Logparsing FCS to find files that were infected
Working an interesting case at the moment where we have multiple files across servers that were infected and we are needing to generate a list of all the files that were infected on each server.
So the first thing to realize is that the 1006 and 3004 events in the system event log under the source FCSAM are the ones that show the detection and include the path that the infection was found in. You could technically probably do the logparser syntax to run locally on the system and parse the event log directly for the paths or even the .evt file if you exported it however I am working with data collected from multiple servers and sent directly to me so have done the syntax for parsing the data that I have currently. As part of our MPS reports utility we export the system event log to a .csv file which you can do easily from the eventvwr gui as well.
You will need to install Logparser 2.2 and ensure it is in your path to run this.
I am basically running the following against the system.csv in order to gather the file paths that were detected.
logparser -i:textline -o:csv "SELECT SUBSTR(Text, ADD(INDEX_OF(Text, 'file:'), 5), SUB(INDEX_OF(Text, '\r\n\r\n\tAlert'), ADD(INDEX_OF(Text, 'file:'), 5))) into pathsfinal.csv from *SYSTEM.csv where
text like '%threatid%' and (text like '%3004%' or text like '%1006%')"
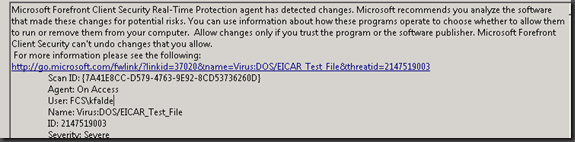
You will need to replace threatid with the actual threatid that you are interested in for example Eicar would probably be 2147519003 so you would replace threatid with 2147519003 if you were looking for paths of files that were infected with Eicar. In my case I’m working more with Sality/Virut file reinfectors so Eicar probably wouldn’t apply but you should get the idea.
Unfortunately I don’t have non-customer sample data to give a good example of the output but you should basically end up with a file that consists of lines with paths for example
c:\windows\junk.exe
c:\temp\gotinfected.exe
c:\users\kfalde\av2009.exe
etc…
EDIT 1/5/2010
Apparently my .csv I was working with was done differently then the output from a .csv exported from the GUI. Mine had carriage return symbols \r\n which I was triggering on as opposed to the output .csv from the GUI which puts the Path Found: on it’s own line like the following:
Path Found: file:C:\malwarefound\here\malware.exe
Unfortunately this makes it more complicated to gather files that were only infected by a specific threatid as this is now on a different line so I’ll look into a way to do this better but for now the following logparser line will work to gather the paths from a .csv output from the eventviewer GUI:
logparser -i:textline -o:csv "SELECT SUBSTR(Text, ADD(INDEX_OF(Text, 'file:'), 5), NULL) into pathsfinal.csv from sysevent.csv where text like '%Found:%'"
Also the following should work quite well directly against the event log however it may be slow when you run it over the network against a target computer that you are trying to gather data from:
logparser -i:EVT -o:csv "select eventid, timewritten, EXTRACT_TOKEN(Strings, 15, '|') into paths.csv from \\REMOTEIPADDRESSHERE\System where Eventid=3004 or EventID=1006
Replace the REMOTEIPADDRESSHERE with the IP of the system you are gathering data for. If you are just running this against the local system you are on use the following:
logparser -i:EVT -o:csv "select eventid, timewritten, EXTRACT_TOKEN(Strings, 15, '|') from System where Eventid=3004 or EventID=1006
Hopefully this is useful for someone :) I know it was a learning useful experience for me. And oh yeah Merry Christmas!! 3 days.. why am I at work???