More on File Shares and Autorun.inf with regards to malware
So in my last post I mentioned the fact that Conficker/Downad whatever can also have a component that will spread through file shares that allow everyone to write at the root level of the file share.
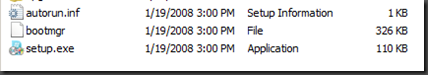
So a typical autorun.inf looks something like this..
[Autorun]
open=setup.exe
icon=setup.exe,0
Glancing at my dvd folder structure in this case I have
So basically with autoruns enabled if I double-click this drive explorer will process Autorun.inf and will run setup.exe in the same location as the autorun.inf. Now if you were running Vista with UAC this wouldn’t be a big deal however a lot/most enterprises probably are not. If you were running with your users as non-admins this would again not be an issue but again this is usually not the case.
So what do we do to mitigate this problem?
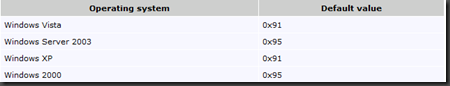
Well by default supposedly we should not process/execute autorun.inf from a network drive anyway on our XP/2K/Vista machine. Check out https://www.microsoft.com/technet/prodtechnol/windows2000serv/reskit/regentry/91525.mspx?mfr=true which goes into detail about the NoDriveTypeAutoRun registry key setting.
The 0x10 setting for “Disables Autoplay on fixed drives” is a default that is present on all our supported OS’s so why does the issue still occur? The reason it still occurs can be found in https://support.microsoft.com/kb/953252 “How to correct “disable Autorun registry key” enforcement in Windows”. If you read through the KB you will basically see that all of our currently supported OS’s had a bug with Explorer and autoruns. The bug though was fixed and released as security bulletin MS08-038 https://support.microsoft.com/kb/950582. Odds are though if you are one of those org’s that didn’t apply MS08-067 what’s a few more months (July vs October of 08). If you are having problems with malware that is spread via autoruns on network shares then you should probably make sure to get MS08-038 installed in your environment as quickly as possible.
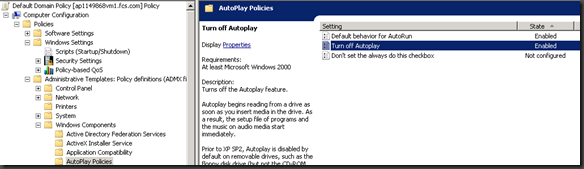
As part of Defense in Depth I would also recommend that you set in a Group Policy linked to your domain to disable Autorun functionality completely. The defaults should be fine once the MS08-038 is installed however in an enterprise setting you don’t want to rely on the “I hope my users didn’t change it” scenario. KB953252 also has information on where to set this, I’ve also included a picture from my test system (it’s 2008 so may look slightly different then 2003). Basically you want to set that “Turn Off Autoplay” as Enabled for “All drives”
That’s about all I have at the moment if you have any questions post them here. Thanks