Using WMI Event rules
This is just a quick example of using a WMI Event rule in OpsMgr.
There are some kinds of events that are not easily captured by Perfmon or the Windows Event log. For many things, we can use WMI and WMI Events.
For some solid background, I suggest reading Brian Wren's article on using these in MOM 2005:
https://technet.microsoft.com/en-us/magazine/cc160917.aspx
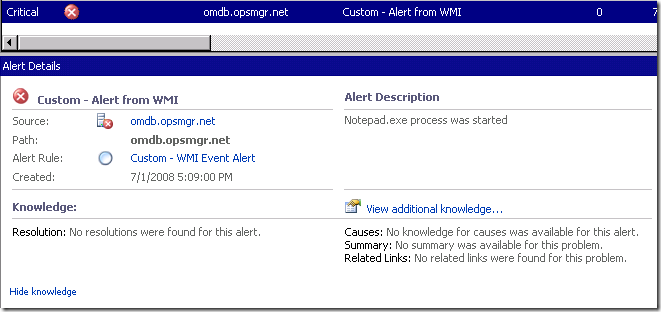
An example I will be using.... is a process starting on an agent machine. A process start typically doesn't have a Windows event logged for it.... like a service might. However, there will be a record of this in WMI.
Create an Alert generating WMI Event rule. Choose a good target class for your rule (I use Windows Server for testing). Set the rule Category to Alert.
For the namespace - choose root\cimv2
For the query.... we will be using the following example query:
SELECT * FROM __InstanceCreationEvent WITHIN 30 WHERE TargetInstance ISA 'win32_process' AND TargetInstance.Name = 'notepad.exe'
For examples of a lot of options and understanding the query components - see the link above.
Basically, I am telling WMI to watch for the creation of a process called notepad.exe, and to check every 30 seconds. Checking too often creates overhead. Checking too infrequently and I might miss the event if notepad.exe gets closed quickly.
Set the rule interval for how often you need OpsMgr to look for these events.... I chose 30 seconds as well for testing.
Once applied, on any server that I open a copy of Notepad.exe on.... I will get an alert for each instance of Notepad running. You can use these to look for processes, services, existence of files, etc.