Why R2? Step-by-Step: Solve BYOD Challenges with Workplace Join in Windows Server 2012 R2 and Windows 8.1
These days, users are growing more and more accustomed to expecting that they can accomplish productive work from anywhere, at any time, and on any device. As a result, IT Pros and organizations are increasingly faced with the challenge of balancing convenience with security to provide users with the necessary remote access to corporate applications and services that was previously available only from corporate-managed Active Directory Domain-Joined PC’s. As one method of addressing this growing need, Windows Server 2012 R2 and Windows 8.1 provide a new BYOD management feature that lots of IT Pros have been excited about: Workplace Join. In addition, Workplace Join is also supported for Apple iOS mobile devices.
This month, we’re joined by Guido van Brakel, Principal Consultant and Subject Matter Expert at Enduria. As a frequent contributor to the IT Pro Community at-large, Guido is always eager to share new information. In this article, Guido will walk us through an overview of Workplace Join and how to configure this new feature in our labs so that we can begin evaluating it …
Keith
- - - - - - - - - -
What is Workplace Join?
With Workplace Join, users can remotely register a non-Domain Joined device in Active Directory (AD) to gain secure “single sign-on” access to permitted corporate network resources from a BYOD, or Bring Your Own Device, PC. The Workplace Join process creates a new device object in AD and also installs a certificate on the device. Once Workplace Join is completed for a device, IT Pros can leverage the user’s device authentication as part of a set of conditional access policies to permit access to only authorized network applications and services. These conditional access policies can be used to provide appropriate access to users when accessing resources from a Workplace Joined device versus a fully Domain Joined device. In addition, users can opt-in to Windows Intune device management, so that IT Pros can provide users with managed access to applications, including internal LOB apps and links to public app stores, and updates on these devices.
Workplace join is enabled by a new AD Federation Service (ADFS) role service in Windows Server 2012 R2 called the Device Registration Service. In order to perform Workplace Join from a BYOD device, that BYOD device can be running any edition of Windows 8.1.
Let Get Started!
To support Workplace Join, you’ll need to first build a base lab environment with ADFS and the new Device Registration Service installed. Use the steps below to build your lab, which are an updated version of the original steps posted here.
Download the Windows Server 2012 R2 evaluation kit. You’ll need these bits to build your lab environment.
Install and configure an AD Domain Controller in a new isolated AD Forest for contoso.com.
Note: For more information and step by step instructions, see this article.- Install the AD DS role service and promote your computer to be a domain controller.
- AD Domain Controller Name: dc1.contoso.com
- AD Forest name: contoso.com
- Install the AD DS role service and promote your computer to be a domain controller.
Install and configure a new member server named ADFS1 and join this server to the contoso.com domain.
- Server name: adfs1.contoso.comCreate Test User and Group Accounts in AD to test Workplace Join and resource access.
Note: For information on how to create user/group accounts in AD, see this article.- Create a new test User Account for “Robert Hatley”
- Username: RobertH
- Password: P@ssw0rd
- Create a new test Group Account for Finance
- Group name: Finance
- Add user RobertH as a member of the Finance group
- Create a new test User Account for “Robert Hatley”
Create a Group Managed Service Account (GSMA) in AD. This GMSA will be used in the configuration of ADFS.
Open a PowerShell command prompt window and run the following command-lines:
Add-KdsRootKey –EffectiveTime (Get-Date).AddHours(-10)New-ADServiceAccount FsGmsa -DNSHostName adfs1.contoso.com -ServicePrincipalNames http/adfs1.contoso.com
Obtain a server SSL certificate from either a public certificate authority (CA) or from your organization's PKI subordinate CA that is trusted by a public certificate authority.
The server SSL certificate must have the following certificate attributes to be used with Workplace Join:
- Subject Name (CN): adfs1.contoso.com
- Subject Alternative Name (DNS): adfs1.contoso.com
- Subject Alternative Name (DNS): enterpriseregistration.contoso.comThe Certificate Revocation List (CRL) location must be accessible to remote client devices for this certificate and all certificates in its certification path to be usable with Workplace Join. This CRL location typically will be remotely accessible when using SSL certifications that are directly signed by a public CA, but the CRL location may not currently be accessible in your organization if using SSL certificates that are signed by a subordinate CA internal to your organization.
Note: For isolated lab testing when your SSL certificate does not have a CRL location available, you can uncheck the Internet Explorer option on the client workstation for Advanced | Security | Check for server certificate revocation and then restart your client workstation. This option is not recommended for production use or in environments where the client workstation has Internet access due to potential security issues.
At the server console of adfs1.contoso.com, install the certificate obtained in Step 6 above in the Local Machine certificate store.
Install the ADFS role on adfs1.contoso.com.
Open Server Manager. To do this, click Server Manager on the Start screen, or Server Manager in the taskbar on the desktop.
In theQuick Start tab of the Welcome tile on the Dashboard page, click Add roles and features. Alternatively, you can click Add Roles and Features on the Manage menu.
On the Before you begin page, click Next.
On the Select installation type page, click Role-based or feature-based installation, and click Next.
On the Select destination server page, click Select a server from the server pool, verify that adfs1.contoso.com is highlighted, and then click Next.
On the Select server roles page, click Active Directory Federation Services, and then click Next.
On the Select features page, click Next.
On the Active Directory Federation Service (AD FS) page, click Next.
After you verify the information on the Confirm installation selections page, select the Restart the destination server automatically if required check box, and then click Install.
On the Installation progress page, verify that everything installed correctly, and then click Close.
Configure the ADFS role on adfs1.contoso.com.
On the Server Manager Dashboard page, click the Notifications flag, and then click Configure the federation service on the server.
The Active Directory Federation Service Configuration Wizard is launched.
On the Welcome page, select Create the first federation server in a federation server farm and click Next.
On the Connect to AD DS page, specify an account with domain administrator permissions for the contoso.com AD domain that this computer is joined to and then click Next.
On the Specify Service Properties page, do the following and then click Next:
Select the SSL certificate that you have obtained earlier. This is the required service authentication certificate. Browse to the location of your SSL certificate.
Provide a name for your federation service, type adfs1.contoso.com. This is the same value you provided when enrolling your SSL certificate.
Provide a display name for your federation service, type Contoso Corporation.
On the Specify Service Account page, select Use an existing domain user account or group Managed Service Account and then specify the GMSA account (fsgmsa) that you previously created in Step 5 above.
On the Specify Configuration Database page, select Create a database on this server using Windows Internal Database and then click Next.
On the Review Options page, verify your configuration selections and click Next.
On the Pre-requisite Checks page, verify that all pre-requisite checks were successfully completed, and then click Configure.
On the Results page, review the results and whether the configuration has completed successfully, and then click Next steps required for completing your federation service deployment.
Configure the Device Registration Service on adfs1.contoso.com.
Open a PowerShell command window and run the following command-line:
Initialize-ADDeviceRegistration
When prompted for a service account, type contoso\fsgmsa$
In the open PowerShell command window, run the following command-line:
Enable-AdfsDeviceRegistration
In the AD FS Management console, navigate to Authentication Policies.
Select Edit Global Primary Authentication.
Select the checkbox next to Enable Device Authentication and then click OK.
Register the Device Registration Service endpoint in the contoso.com DNS namespace.
- At the server console of dc1.contoso.com, launch Server Manager, and open the DNS Management tool from the Tools menu.
- In the console tree, expand DC1, expand Forward Lookup Zones, right-click contoso.com, and then click New Host (A or AAAA) .
- In the Name field, type the name you will use for your AD FS farm, for this walkthrough, type adfs1.
- In the IP address field, enter the IP address of the adfs1.contoso.com server. Click the Add Host button.
- Right-click contoso.com, and then click New Alias (CNAME) .
- In the New Resource Record dialog box, type enterpriseregistration in the Alias name box.
- In the Fully Qualified Domain Name (FQDN) of the target host field, type adfs1.contoso.com and click OK.
- At the server console of dc1.contoso.com, launch Server Manager, and open the DNS Management tool from the Tools menu.
Completed! Let’s Test Workplace Join!
You’ve completed the process for configuring the servers in your lab environment. Now, let’s switch over to a Windows 8.1 device in your lab to test the Workplace Join process.
Note: To successfully complete these steps in an isolated lab environment, connect your Windows 8.1 device to the same network as adfs1.contoso.com and ensure that your Windows 8.1 device is using dc1.contoso.com for local DNS name resolution. This Windows 8.1 device should not be Domain Joined to Active Directory.
Let’s get Joined!
Complete the Workplace Join process from your Windows 8.1 device using the following steps:
- Sign on to your Windows 8.1 device with your Microsoft account.
- On the Start screen, open the Charms bar and select the Settings charm.
- Select Change PC Settings in the Settings charm sidebar.
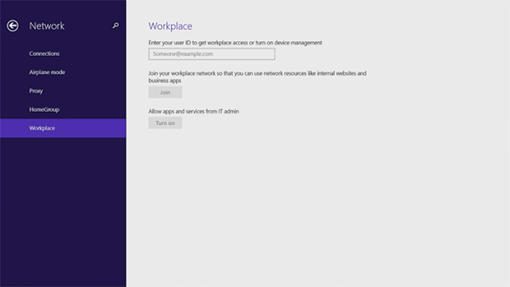
- On the PC Settings page, select Network and then click Workplace.
- When prompted to Enter your User ID to get workplace access or turn on device management, type RobertH@contoso.com and then click Join.
- When prompted for credentials, enter the test domain user account credentials for roberth@contoso.com. Click OK.
You should now see the message: This device has joined your workplace network.
Additional Resources in which you may have interest …
- Hands-on Lab: Implementing Workplace Join
- Step-by-Step: Workplace Join with an Apple iOS Device
- Step-by-Step: Connect to Applications and Services using Web Application Proxy
- Guided Hands-on Lab: BYOD Management with Windows Intune and System Center
- Get Ready for Windows 8.1 in One Page!
- Backup and Recovery of Windows 8 & Windows 8.1
- Windows 8.1 – DisplayLink Video Drivers?
About Guido …
Guido van Brakel is an experienced Principal Consultant and Subject Matter Expert at Enduria. Guido is certified on several Microsoft technologies, including Windows Server, SharePoint and Office 365. Recently, Guido assisted in the development of training courseware for Microsoft SharePoint Server 2013. As a frequent contributor to the IT Pro community, you will find Guido online on his blog at https://www.enduria.eu/. Be sure to check out Guido’s blog for other great articles on Windows Server 2012 R2 and Windows 8.1!