Error While Configuring WAP–”The Underlying Connection Was Closed”–Part 2
Last week I ran into an issue that was similar in behavior to something that I covered in another previous post. I am inclined to think that we will see more calls similar to this so I thought I would take some time to show you what the cause was and how to resolve it.
Problem
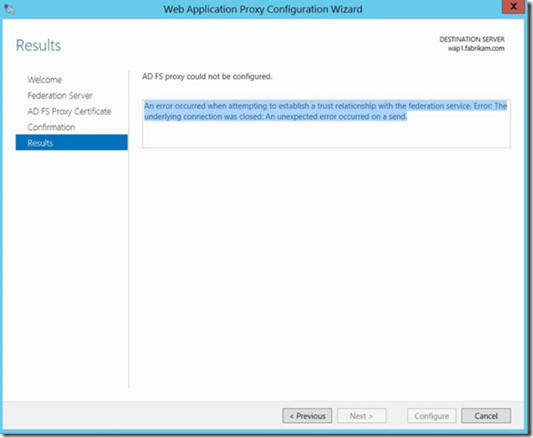
Running the configuration wizard on the WAP Server generates the following error:
“An error occurred when attempting to establish a trust relationship with the federation service. Error: The underlying connection was closed: An unexpected error occurred on a send.”
Figure 1 shows the error we see in the wizard.
Fig. 1
Data Gathering and Analysis
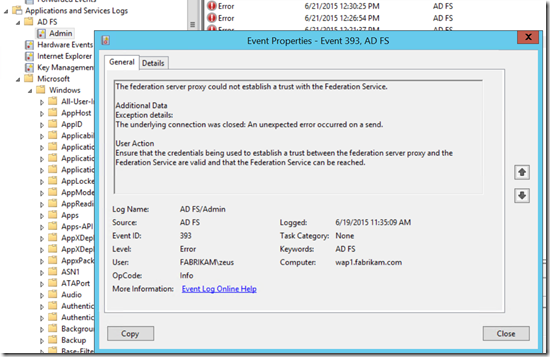
Checking the AD FS Admin event log on the WAP Server we see an Event ID 393 that corresponds to the time we received the error from the wizard (Figure 2).
Fig. 2
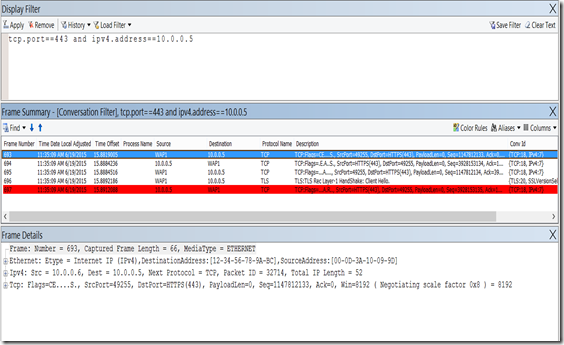
I also used Netmon 3.4 to capture a trace and see what was happening on the wire. Filtering the traffic for TCP traffic coming from the ADFS Server I can see the below behavior (Figure 3).
Fig. 3
As you can see there the TCP 3 way handshake sets up, there is a SSL/TLS Client Hello from the WAP Server and immediately the ADFS server resets the connection.
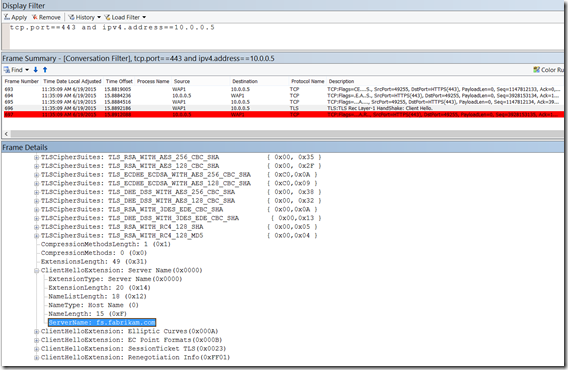
Since we have seen other issues that are caused by an incorrect SNI header that is the first place I checked. The SNI header value is fs.fabrikam.com (Figure 4).
Fig. 4
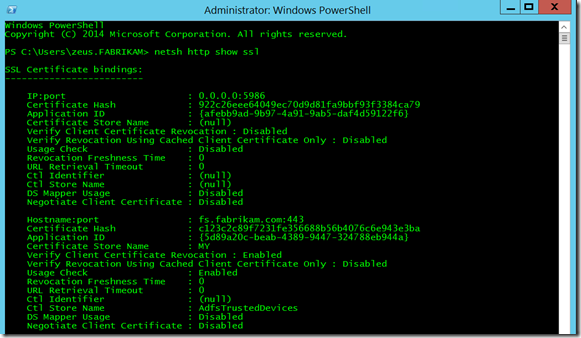
Back on the ADFS Server I run the command netsh http show ssl and verify that this is the correct value that is bound to port 443 (Figure 5).
Fig. 5
This issue was a little harder to diagnose than some of the previous ones we had seen. There was no corresponding event on the ADFS Server. We finally came to the conclusion that it was a protocol issue and found out that TLS 1.0 had been disabled on the WAP and ADFS Server. This has become a common practice because of some of the recent attacks such as Poodle.
Below is a summary of the values for the following key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
ADFS Server:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"Enabled"=dword:00000000
WAP Server:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"Enabled"=dword:00000000
As you can see TLS 1.0 Server and Client was disabled on both machines.
Resolution
In order to get this working again we had to enable TLS 1.0 on both the WAP and ADFS Server. In particular ADFS (Server) and WAP (Client) had to be enabled. We are likely to see this more often as companies become more aware of threats and attempt to lock down protocols on servers.
Update: We realized that some people may be hesitant to use TLS 1.0 so we did some additional testing. It turns out that this is an issue with .NET Framework 4 not using TLS 1.1 or 1.2. By adding a simple registry key to the WAP Server you can get this functioning with TLS 1.0 disabled and TLS 1.1 or 1.2 enabled.
Location: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319
DWORD Value: SchUseStrongCrypto
Value: 1
Reboot the WAP Server after adding the key and you should be good to go.
Note: If the information contained here was useful please let me know in the comments below. Also, if there are any corrections needed or you would like to see future content on a particular subject please let me know that as well. Thanks!
Special thanks to Ian Parramore for this research and troubleshooting!