Third-party Active Directory Migration Tools and KB 3070083
Hello, Chad Munkelt here with my very first post for the Ask PFE Platforms blog.
I wanted to discuss a new hotfix that Microsoft released recently:
This hotfix was created to address an issue with third-party Active Directory migration tools that receive a duplicate Service Principle Name (SPN) error when trying to migrate users or computers within the same forest.
In Windows Server 2012 R2, we introduced SPN uniqueness checks/blocks which ensure applications or administrators aren't able to create objects in Active Directory with the same SPN as another object.
Typically, preventing duplicate SPNs is a great idea. Duplicate SPNs can cause issues, including Kerberos authentication problems or application failures. However, there are some situations/tools that require the ability to bypass the duplicate SPN check in order to function properly.
A prime example would be a third-party Active Directory migration tool or even the built in command NETDOM. When these tools are used, the SPN uniqueness check prevents the application from fully moving or migrating computers and users, and will often error out.
In order for these applications to work properly, the hotfix alters AD behavior via the dSHeuristics setting in Active Directory and allows the SPN uniqueness check to be bypassed.
This may be useful to individuals who are running all Windows Server 2012 R2 domain controllers, and need to do an intra-forest migration using third party Active Directory migration tools.
- Note - Microsoft's Active Directory Migration Tool (ADMT) isn't impacted by this this issue
!! CAUTIONARY NOTES !!
- This is a temporary change to get through a very specific scenario. Once complete, it is STRONGLY recommended to revert the change to ensure the AD retains its built-in protection mechanisms. Take a screenshot of the current/pre-changed value so you can revert the change when you no longer need this setting enabled.
- Changing the dSHeuristics settings in this manner is for a very specific scenario and is not recommended unless you are experiencing the same issues.
- Changing this setting should not be necessary if you are using Microsoft ADMT.
- Test all changes in a non-production environment or test lab first.
- This hotfix requires a restart of the target domain controller after it is installed.
- Ensure you have gone through all of your change control processes prior to implementing the change in the production environment.
- Changing or modifying the Configuration Container is a forest wide change. It is replicated out to all domain controllers, change with caution.
- Before you ever change or modify the Configuration Container ensure you have a current, valid Active Directory backup and you've verified you can restore.
- This does not disable the all SPN uniqueness checks across the board – this only affects manually setting of a duplicate SPN in ADSI Edit or using NETDOM.
Details
We didn't scare you away? Carry on, wayward son…
You can configure the dSHeuristics to either bypass UPN, SPN, or both UPN and SPN checking. The supported values tied to this function and this specific aspect of dSHeuristics are listed below. You can find out more about the various dSHeuristics settings from here:
The following are the supported dSHeuristics values for this situation:
- dSHeuristic 21st char = 1: AD DS allows adding duplicate user principal names (UPNs)
- dSHeuristic 21st char = 2: AD DS allows adding duplicate service principal names (SPNs)
- dSHeuristic 21st char = 3: AD DS allows adding duplicate SPNs and UPNs
- dSHeuristic = Any other value: AD DS enforces uniqueness check for both SPNs and UPNs
Examples (assuming you have the default dSHeuristic values to begin with – which you may/may not have):
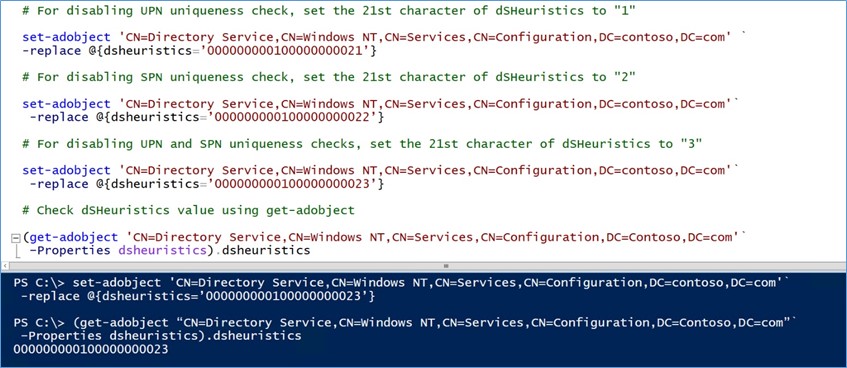
- For disabling UPN uniqueness check, set the 21st character of dSHeuristics to "1" (000000000100000000021)
- For disabling SPN uniqueness check, set the 21st character of dSHeuristics to "2" (000000000100000000022)
- For disabling UPN and SPN uniqueness checks, set the 21st character of dSHeuristics to "3" (000000000100000000023)
Download and Install the Hotfix
In order to make the changes necessary, you need to download the hotfix from KB3070083 and ensure you have met the KB prerequisites. It is recommended that you install the hotfix on all domain controllers that will be used during the Active Directory migration and recall, the install WILL require a reboot.
Configure dSHeuristics to Disable SPN Uniqueness Check
You can modify the attribute through ADSI Edit, LDP.exe, and "Get-ADObject/Set-ADObject" AD PowerShell cmdlets. Please note that in all of the examples I am using the domain Contoso.com, ensure you replace that with your domain.
Using PowerShell to modify the dSHeuristics.
One of the easiest ways to modify the dSHeuristics attribute is through PowerShell. The commands for using PowerShell are as follows:
Note: This value may not be the exact same value you have, this is replacing the default value my lab has, and changing the 21st character. Ensure you do a Get-ADObject first and accurately record the value, taking care below to only change the 21st character.
- To check dSHeuristics value using get-adobject
- (get-adobject "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=Contoso,DC=com" –Properties dsheuristics).dsheuristics
- For disabling UPN uniqueness check, set the 21st character of dSHeuristics to "1".
- Set-adobject 'CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=Contoso,DC=com' –replace @{dsheuristics='000000000100000000021'}
- For disabling SPN uniqueness check, set the 21st character of dSHeuristics to "2".
- Set-adobject 'CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=Contoso,DC=com' –replace @{dsheuristics='000000000100000000022'}
- For disabling UPN and SPN uniqueness checks, set the 21st character of dSHeuristics to "3".
- Set-adobject 'CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=Contoso,DC=com' –replace @{dsheuristics='000000000100000000023'}
- For setting dSHeuristics back to the default value of <not set>
- Set-adobject 'CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=Contoso,DC=com' –clear dsheuristics
- Note: If you had a value set for dSHeuristics set prior to making this change that will also be removed with the clear command.
Below is an example using the PowerShell ISE to set and view the dSHeuristics value. We used line continuation (back tick `) for readability purposes.
For those that are not comfortable with using PowerShell or want to use another method, you can use ADSI Edit or LDP.exe.
Below are two sets of instructions – quick, for those familiar with ADSI Edit and LDP and a longer set for those not as familiar with ADSI Edit or LDP.
Quick Steps - Using ADSI Edit
- In the left pane of ADSIEdit, right-click ADSI Edit and select Connect to from the menu.
- Select Configuration from the Select a well-known Naming Context menu and click OK.
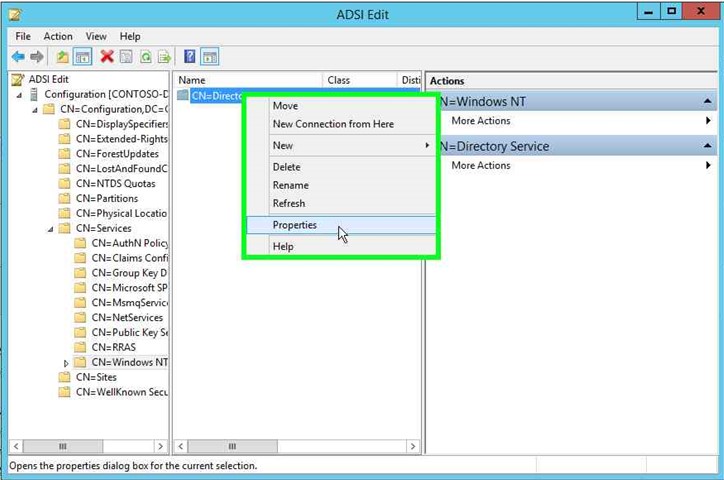
- In the left pane, expand Configuration, CN=Services, CN=Windows NT. In the right pane, right-click CN=Directory Service, and select Properties from the menu.
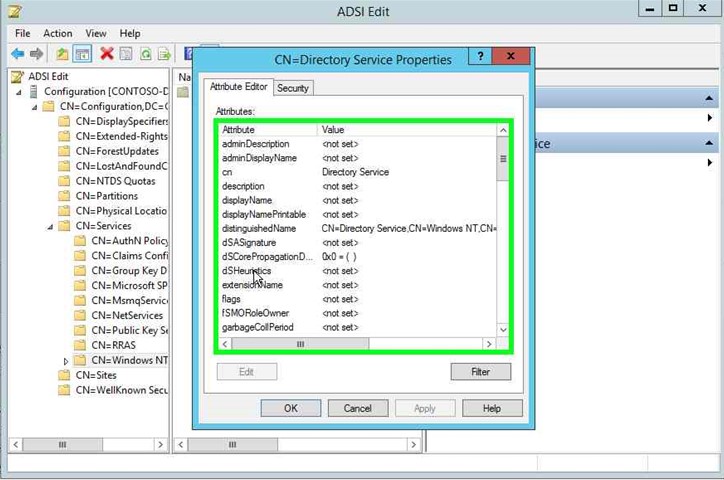
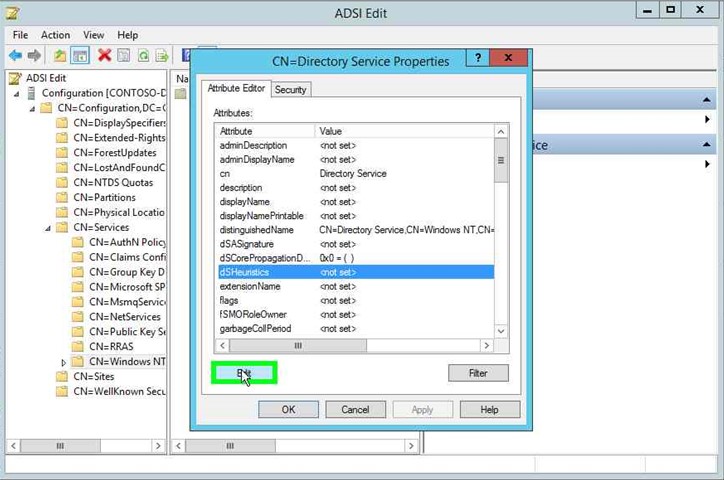
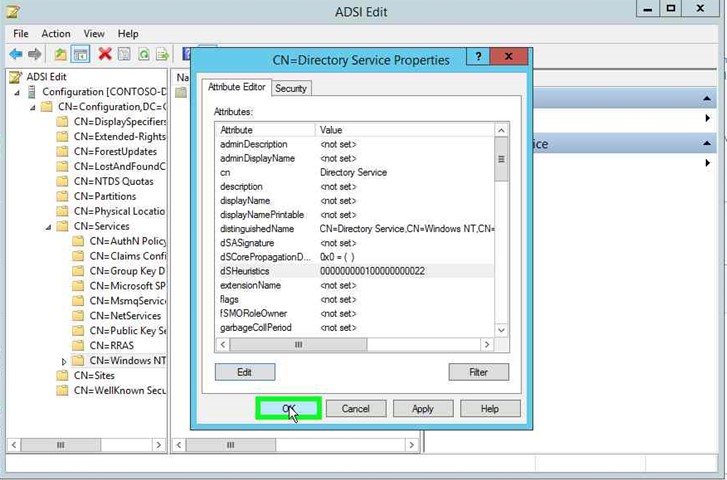
- In the CN=Directory Service Properties dialog box, select dSHeuristics on the Attribute Editor tab and click Edit.
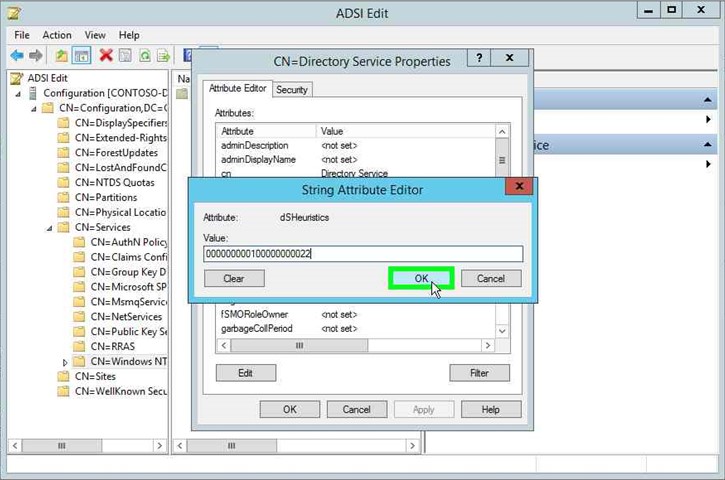
- In the String Attribute Editor dialog box, type 000000000100000000022 to disable NETBIOS based SPN uniqueness check, and click OK.
- Click OK in the CN=Directory Service Properties dialog box and close ADSI Edit.
Quick Steps - Using LDP
- Open LDP.exe
- Click on Connection and select Connect
- Enter the name or IP address of a domain controller
- Click on connection and select Bind…
- Chose a Bind Type and click OK.
- Click on View and select Tree.
- Select CN=Configuration,DC=CONTOSO,DC=COM for Base DN, click OK.
- Drill down to CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=Contoso,DC=Com and right click and select Modify.
- Enter the below information: Please note that you must know your current value and only change the 21st character in the values field.
- Attribute: dSHeuristics
- Values: 00000000010000000022
- Operation: Replace
- Click on Enter and then Run.
Longer Steps – Using ADSI Edit (captured here with the awesome Problem Steps Recorder) Step 1: Open Server Manager Step 2: Click on "Tools" |
|
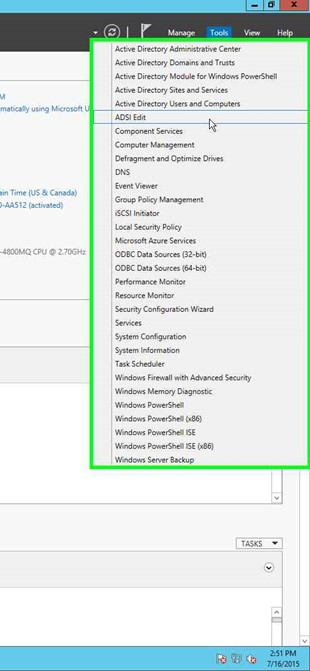
Step 3: Click on "ADSI Edit". |
|
Step 4: Click on "ADSI Edit (tree item)" in "ADSI Edit". |
|
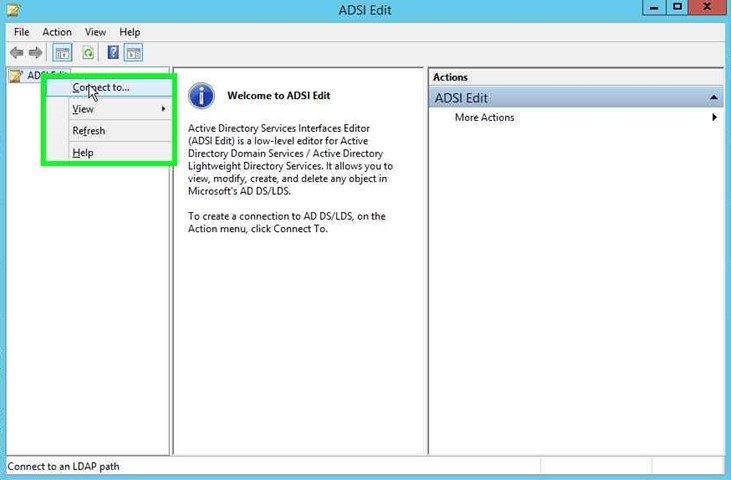
Step 5: Click on "Connect to... ". |
|
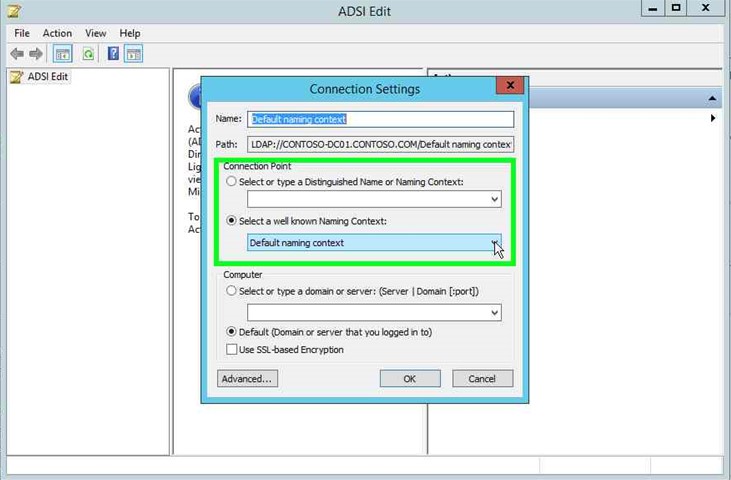
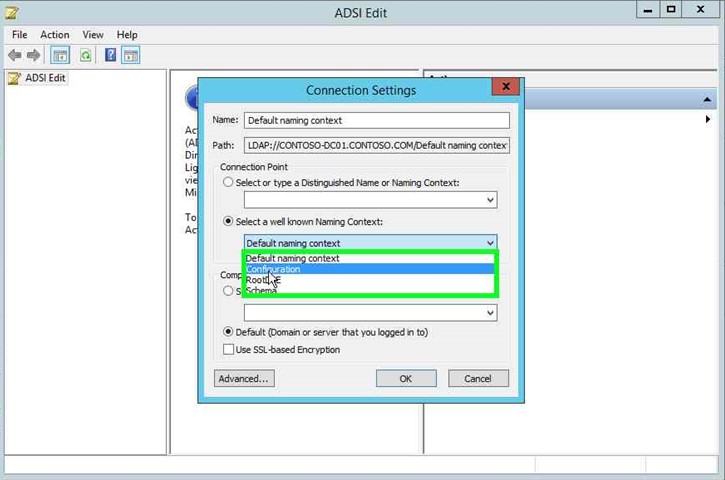
Step 6: Under "Select a well know Naming Context" click on the drop down in "Connection Settings". |
|
Step 7: Click on "Configuration (list item)". |
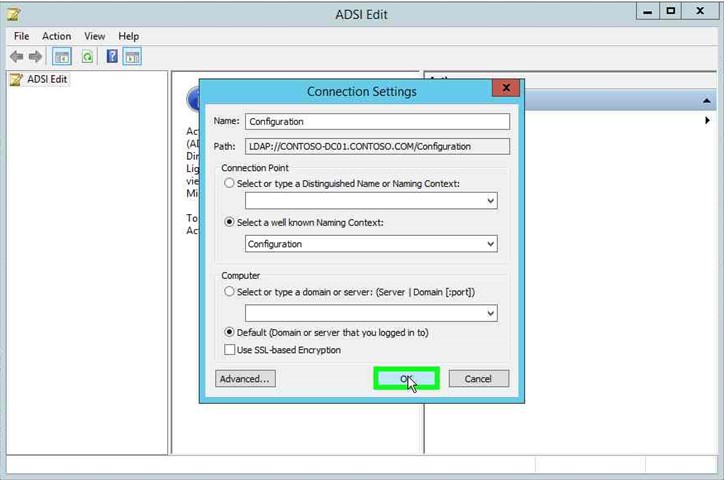
|
Step 8: Click on "OK (button)" in "Connection Settings". |
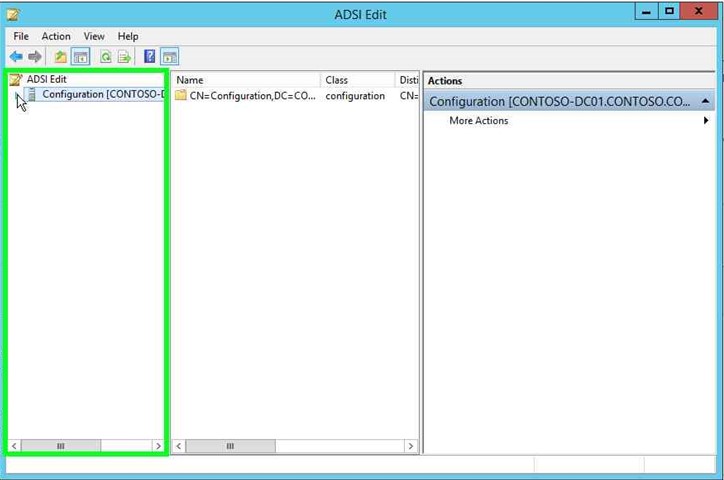
|
Step 9: Click on "Configuration [CONTOSO-DC01.CONTOSO.COM] (tree item)" in "ADSI Edit". |
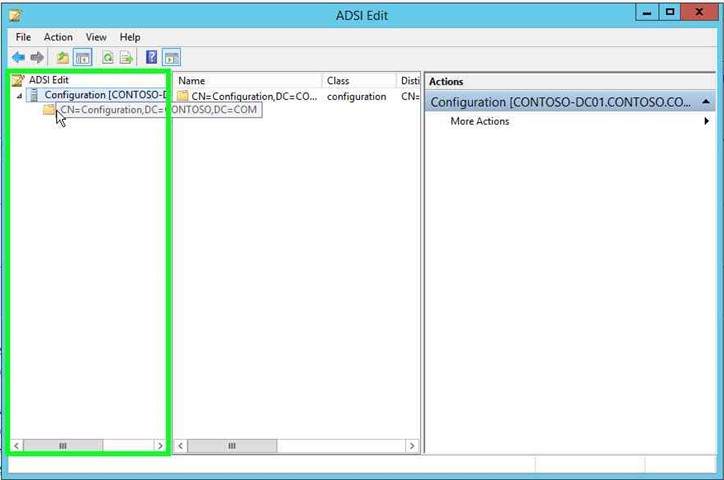
|
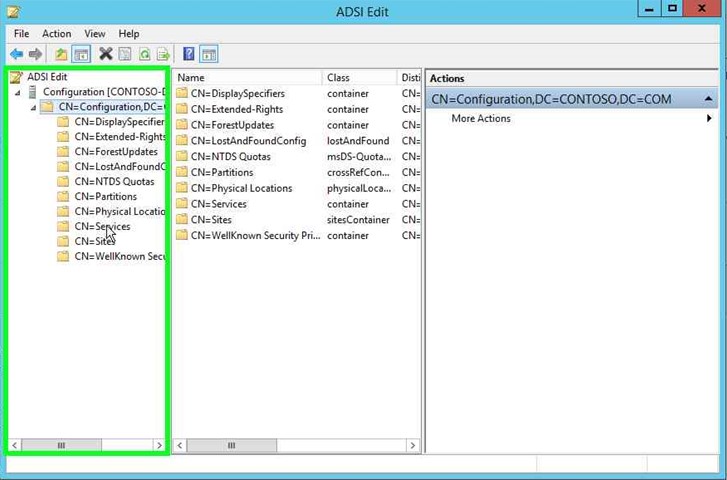
Step 10: Double click on "CN=Configuration,DC=CONTOSO,DC=COM (tree item)" in "ADSI Edit". Choosing your domain, obviously. |
|
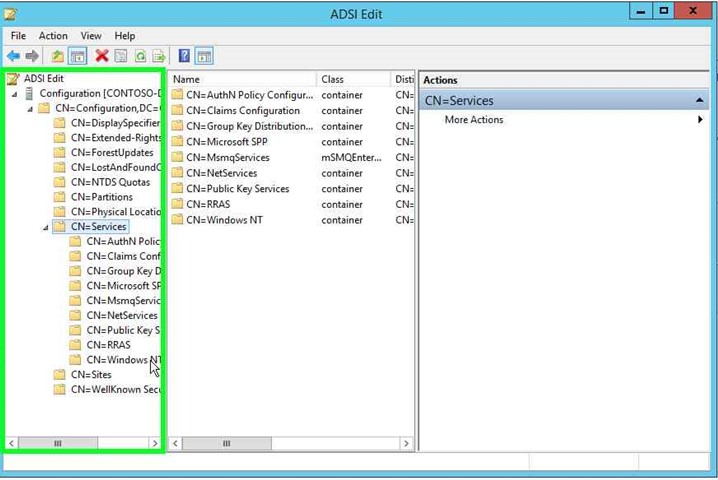
Step 11: Double click on "CN=Services (tree item)" in "ADSI Edit". |
|
Step 12: Click on "CN=Windows NT (tree item)" in "ADSI Edit". |
|
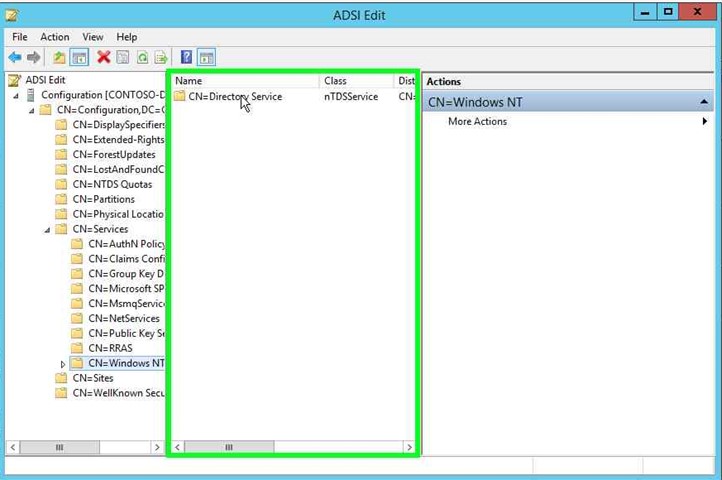
Step 13: Right click on "CN=Directory Service (edit)" in "ADSI Edit". |
|
Step 14: Click on "Properties (menu item)". |
|
Step 15: Click on "dSHeuristics" in "CN=Directory Service Properties". |
|
Step 16: Click on "Edit (button)" in "CN=Directory Service Properties" and take a screenshot of the current value so you can revert the change when you no longer need this setting enabled. |
|
Step 17: Input dSHeuristics value.
|
Step 18: Click on "OK" in "String Attribute Editor". |
|
Step 19: Click on "OK" in "CN=Directory Service Properties". |
|
Step 20: Allow the setting to replicate out to all domain controllers prior to testing the setting.
Longer Steps - Using LDP
Step 1: Right click PowerShell and select "Administrator: Windows PowerShell ". |
|
Step 2: Enter ldp.exe in the PowerShell window. |
|
Step 3: Click on Connection. |
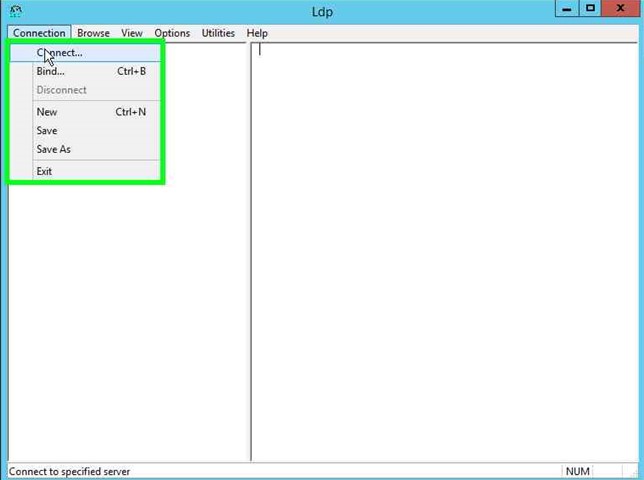
Step 4: Click on "Connect... (menu item)" |
|
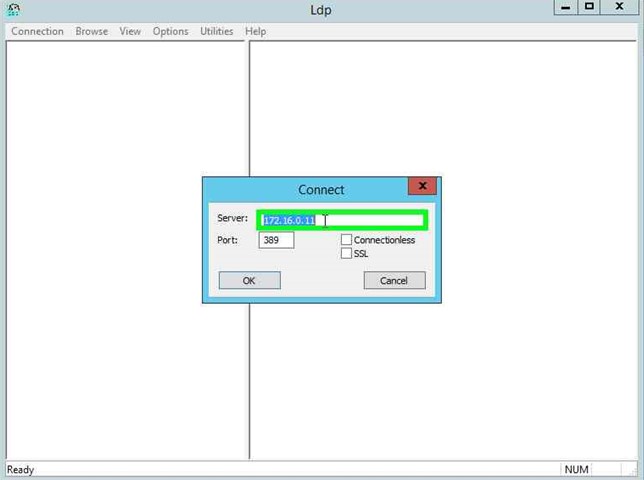
Step 5: Click on "Server: (edit)" in "Connect". |
|
|
Step 6: Input the name or IP Address of your domain Controller in "Server: (edit)" in "Connect". Click on "OK (button)" in "Connect". |
|
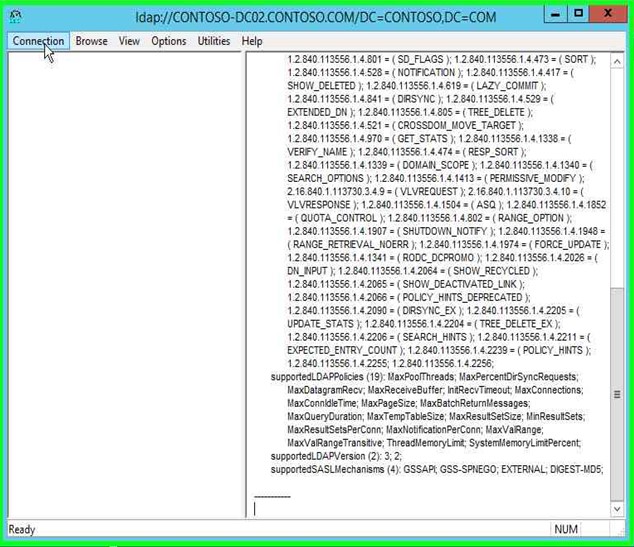
Step 7: Click on "Connection (menu item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". Please note that this will be your domain name and not Contoso. |
|
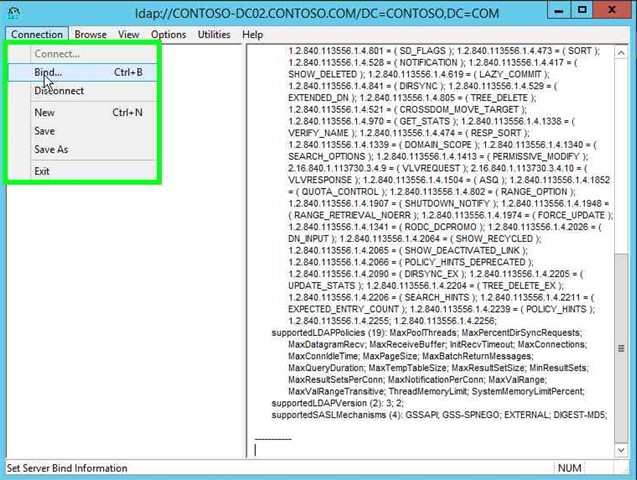
Step 8: Click on "Bind... (menu item)". |
|
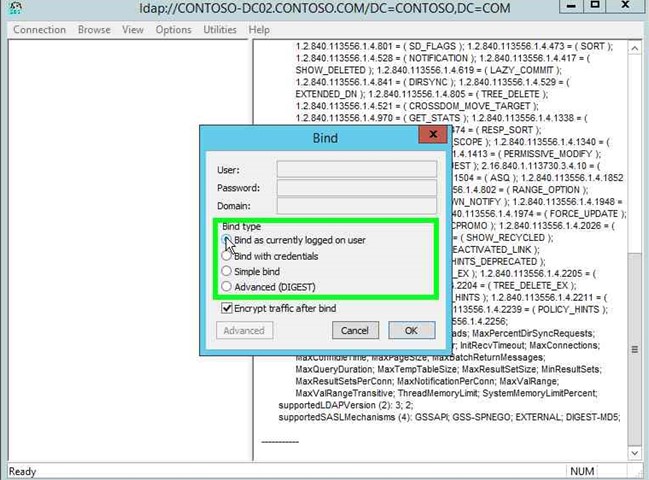
Step 9: Click on "Bind as currently logged on user (radio button)" in "Bind". At this point ensure you use credentials that have permissions to modify the Configuration Container. If you are not logged in with the applicable rights, choose "Bind with credentials". |
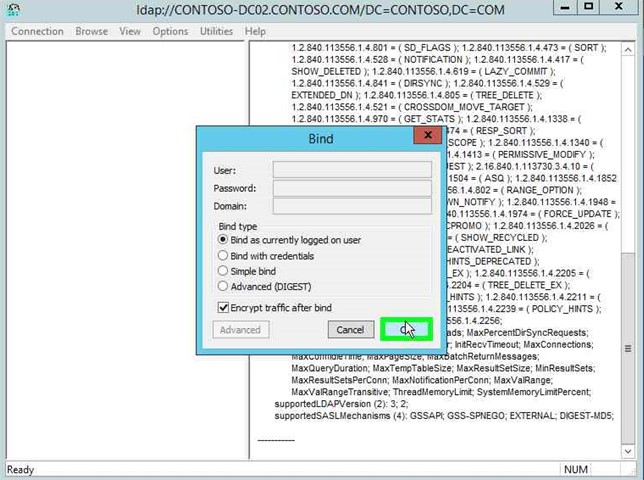
|
Step 10: Click on "OK (button)" in "Bind". |
|
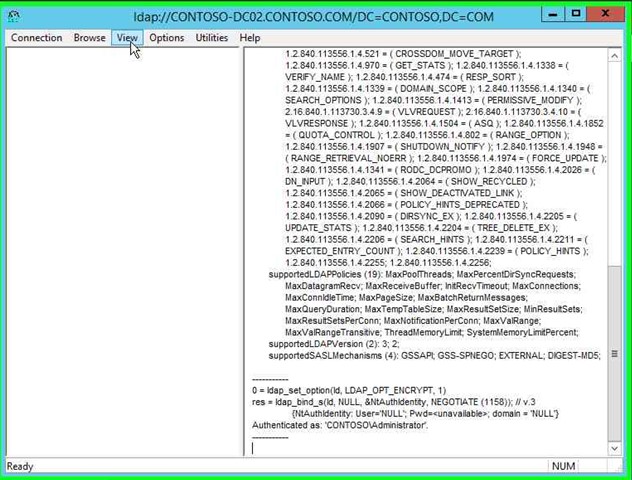
Step 11: Click on "View (menu item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". |
|
|
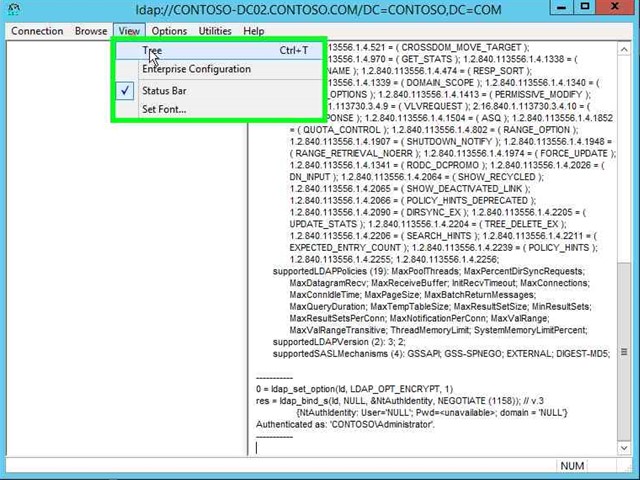
Step 12: Click on "Tree (menu item)". |
Step 13: Click on "Open (button)" in "Tree View". |
|
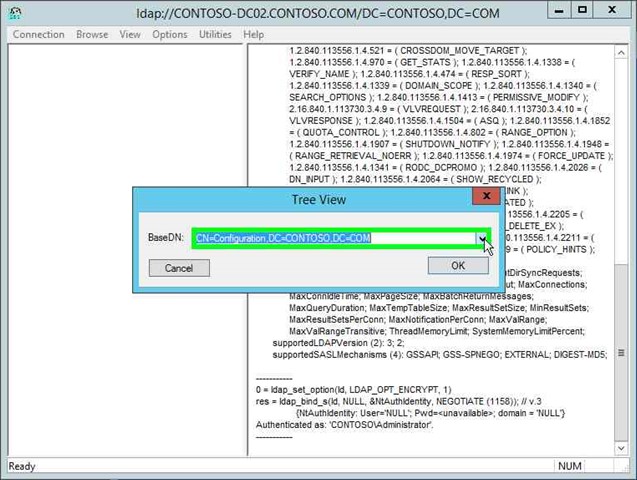
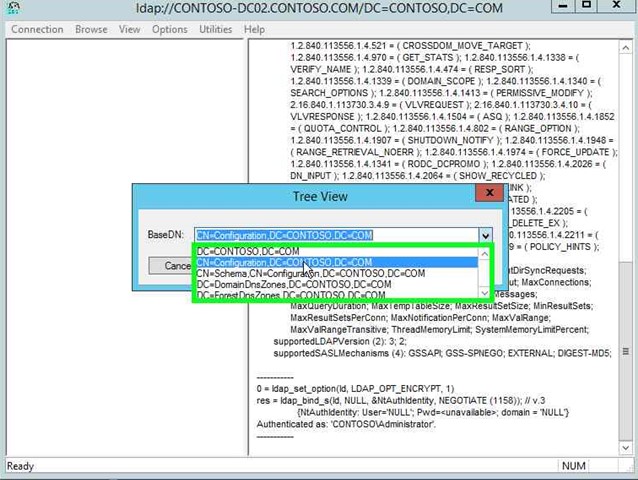
Step 14: Click on "CN=Configuration,DC=CONTOSO,DC=COM (list item)". Please note this is your domain, not Contoso. |
|
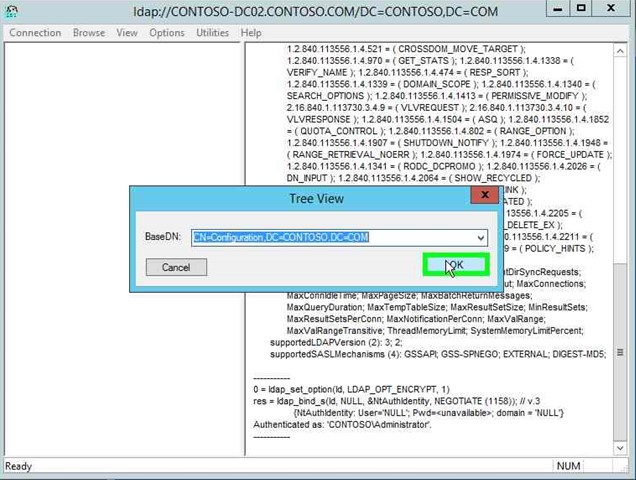
Step 15: Click on "OK (button)" in "Tree View". |
|
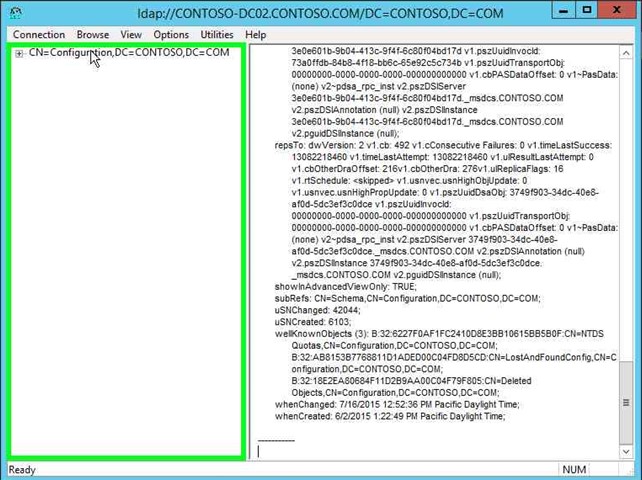
Step 16: Click on "CN=Configuration,DC=CONTOSO,DC=COM (tree item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". |
|
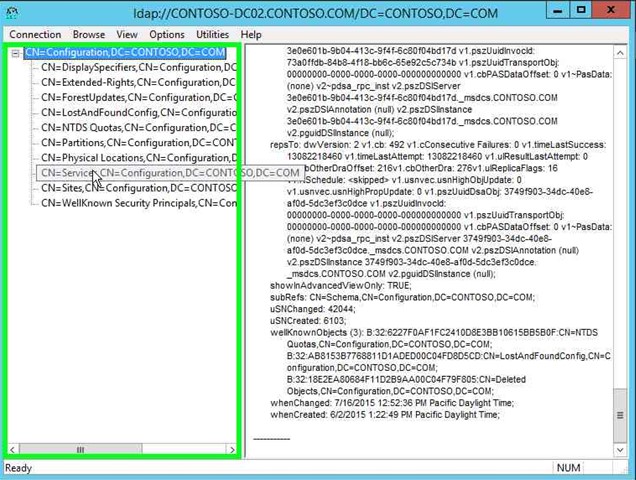
Step 17: Double click on "CN=Services,CN=Configuration,DC=CONTOSO,DC=COM (tree item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". |
|
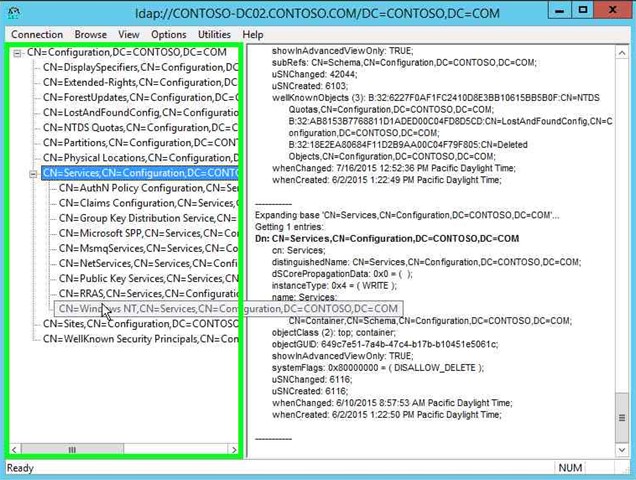
Step 18: Double click on "CN=Windows NT,CN=Services,CN=Configuration,DC=CONTOSO,DC=COM (tree item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". |
|
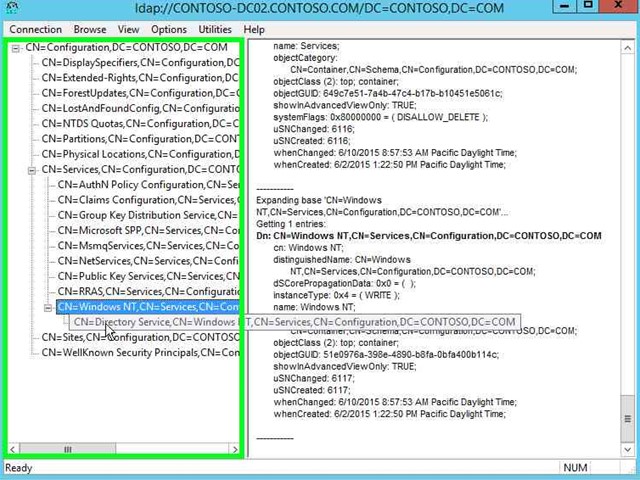
Step 19: Click on "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=CONTOSO,DC=COM (tree item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". |
|
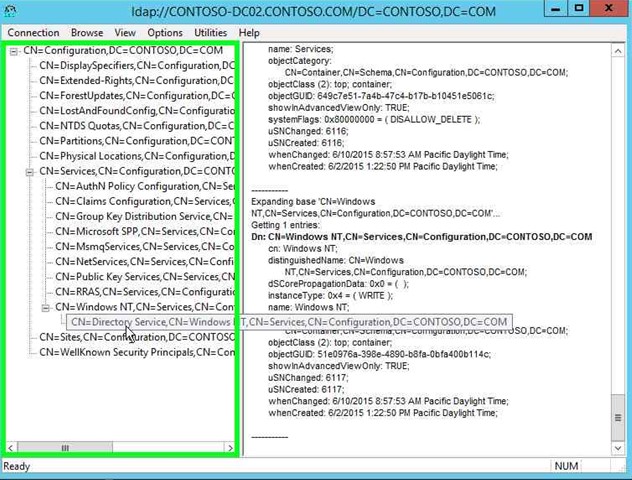
Step 20: Right click on "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=CONTOSO,DC=COM (tree item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". |
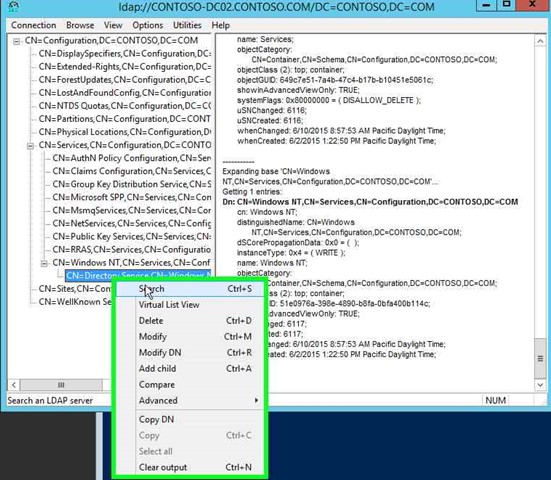
|
Step 21: Click on "Search (menu item)". |
|
|
Step 22: Click on "Open (button)" in "Search". |
|
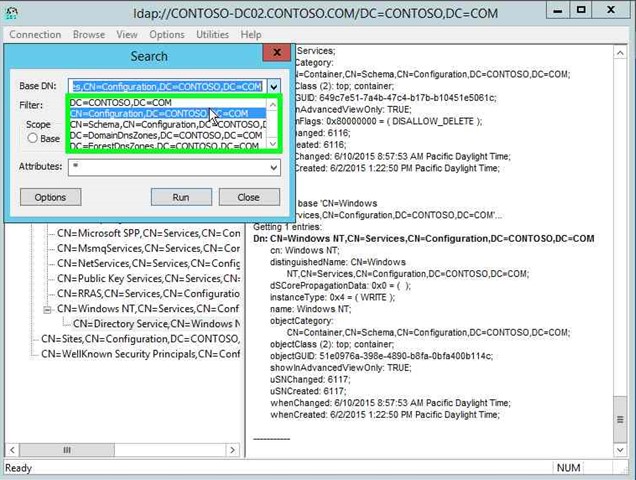
Step 23: Click on "CN=Configuration,DC=CONTOSO,DC=COM (list item)". |
|
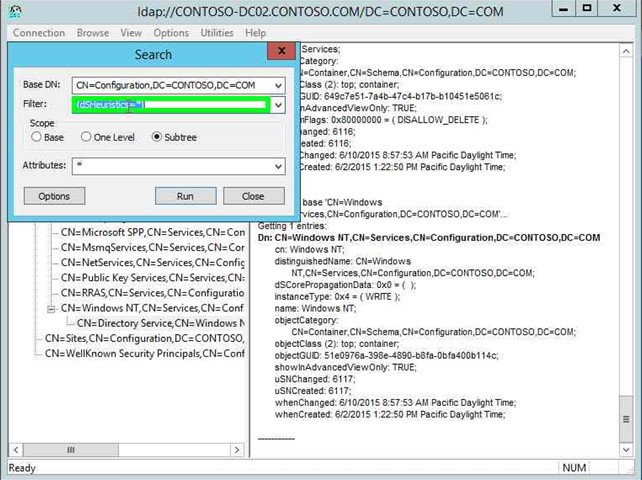
Step 24: Left click on "Filter: (edit)" in "Search". |
|
Step 25: Click on "Filter: (edit)" in "Search". |
|
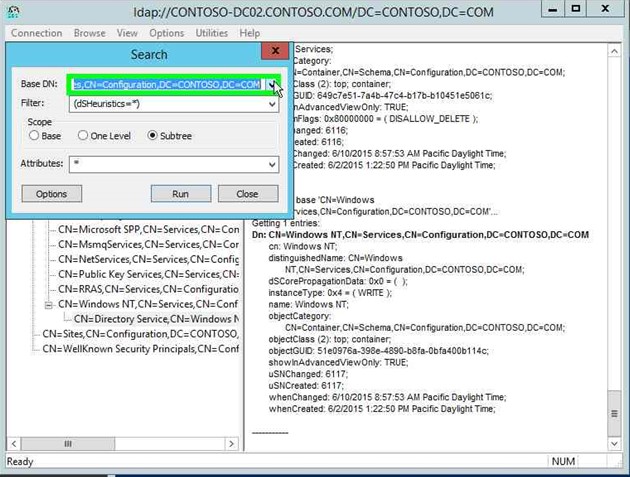
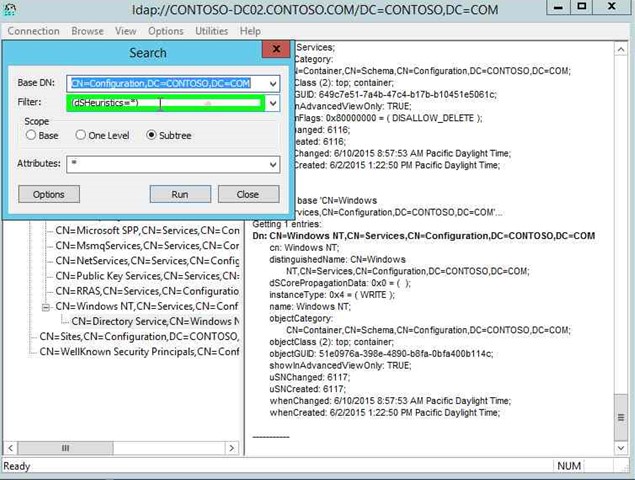
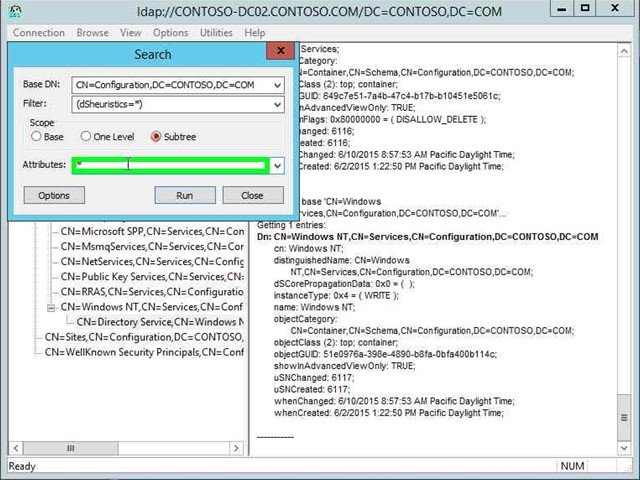
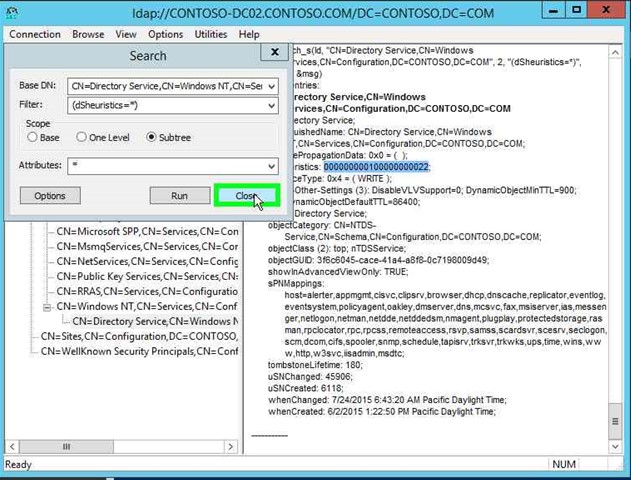
Step 26: Input (dSHeuristics=*).in "Filter: (edit)" in "Search". |
|
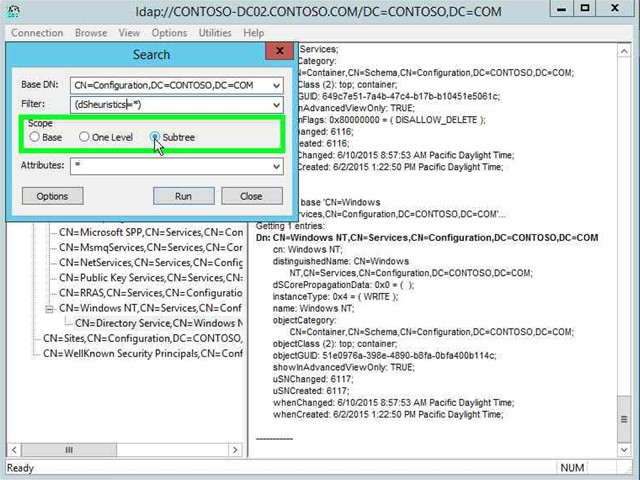
Step 27: Click on "Subtree (radio button)" in "Search". |
|
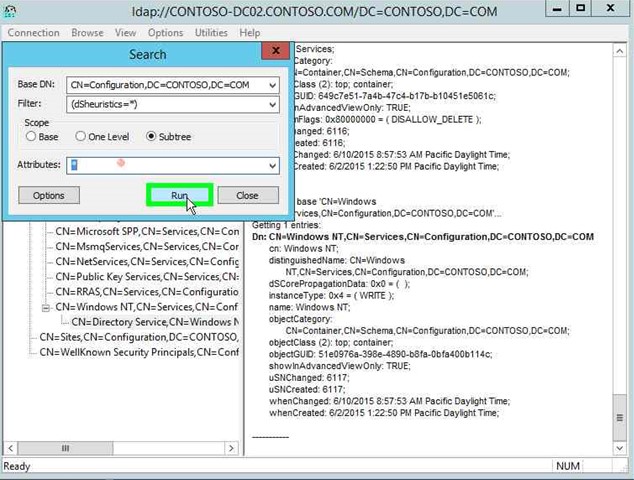
Step 28: Click on "Attributes: (edit)" in "Search" and enter a "*" without quotes. |
|
Step 29: Click on "Run (button)" in "Search". |
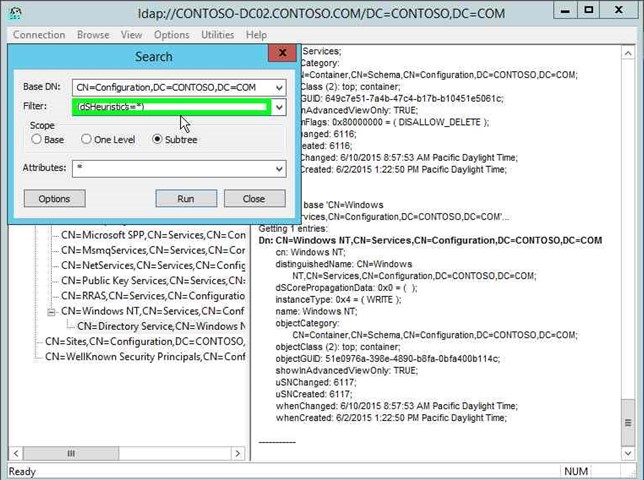
|
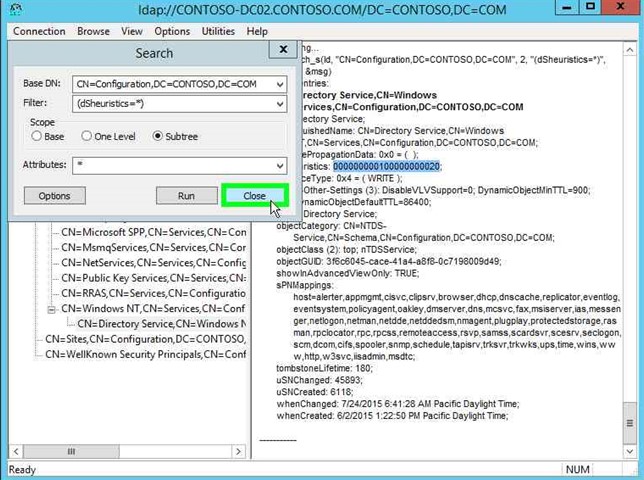
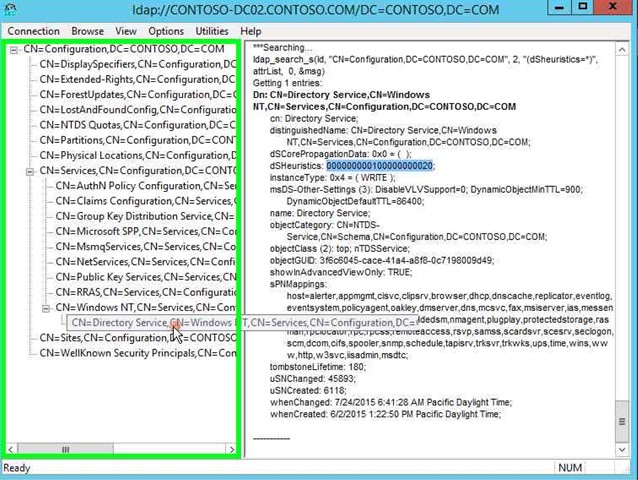
Step 30: You can see the current value in the right hand side. Record the pre-change value is, so you can change it back when you are done. Click on "Close (button)" in "Search". |
|
Step 31: Click on "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=CONTOSO,DC=COM (tree item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". |
|
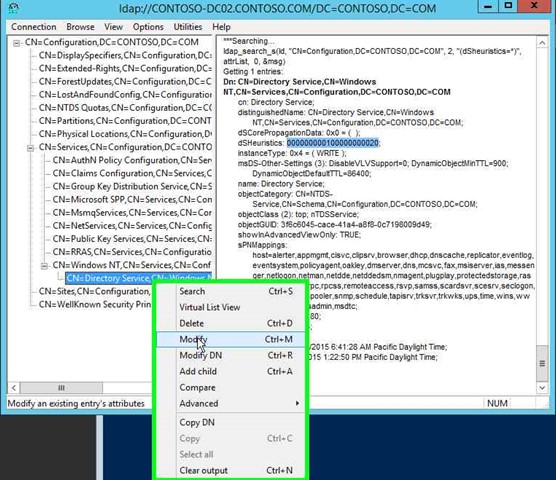
Step 32: Right click on "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=CONTOSO,DC=COM (tree item)" in "ldap://CONTOSO-DC02.CONTOSO.COM/DC=CONTOSO,DC=COM". |
|
Step 33: Click on "Modify (menu item)". |
|
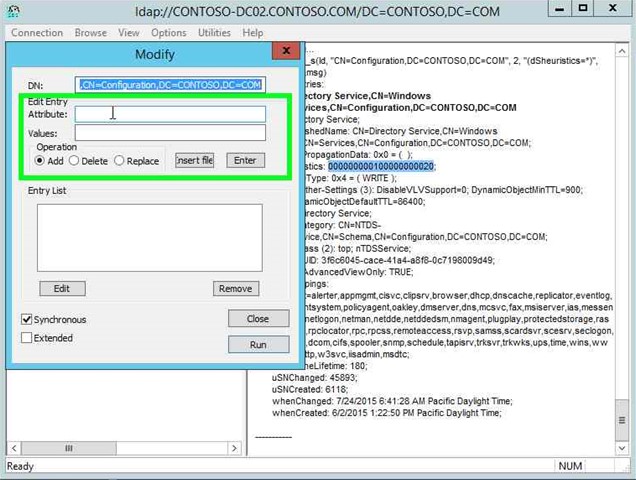
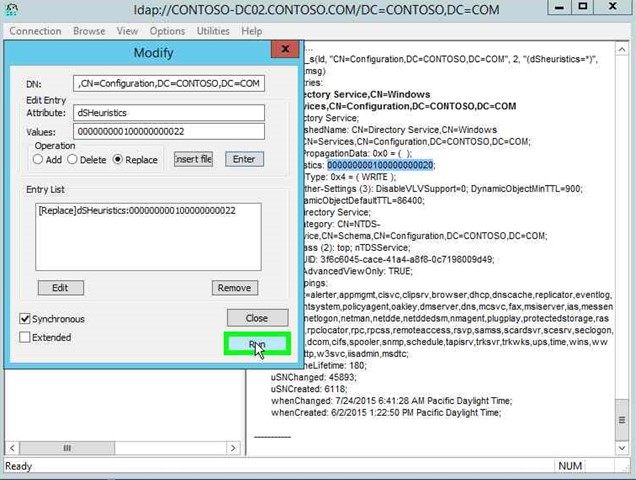
Step 34: Click on "Attribute: (edit)" in "Modify". |
|
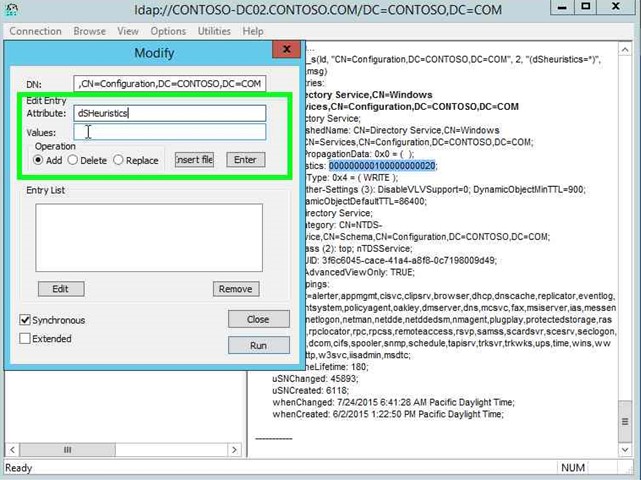
Step 35: Input dSHeuristics on "Attribute: (edit)" in "Modify". |
|
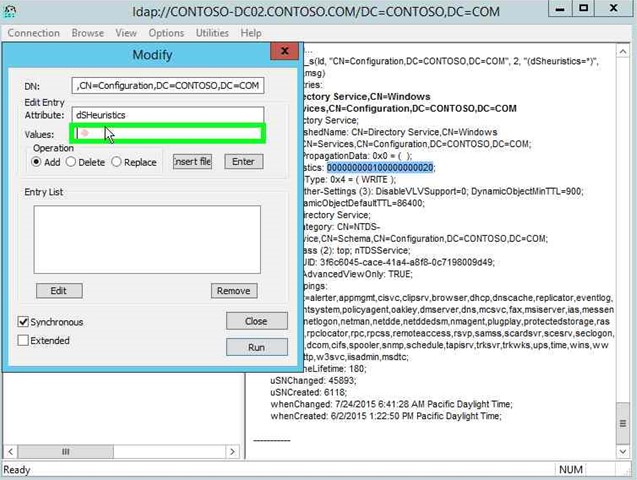
Step 36: Click on "Values: (edit)" in "Modify". |
|
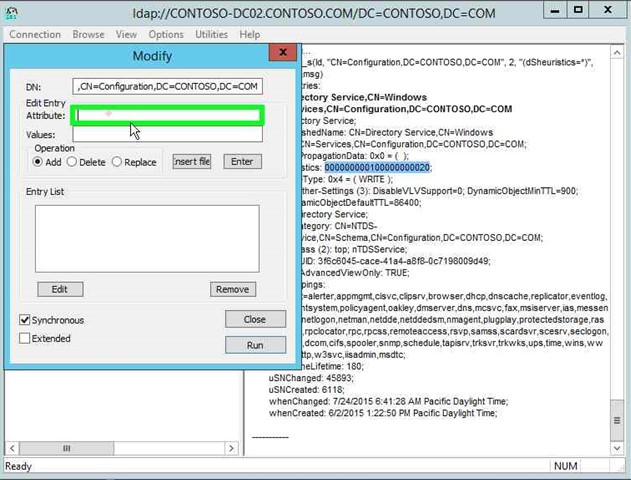
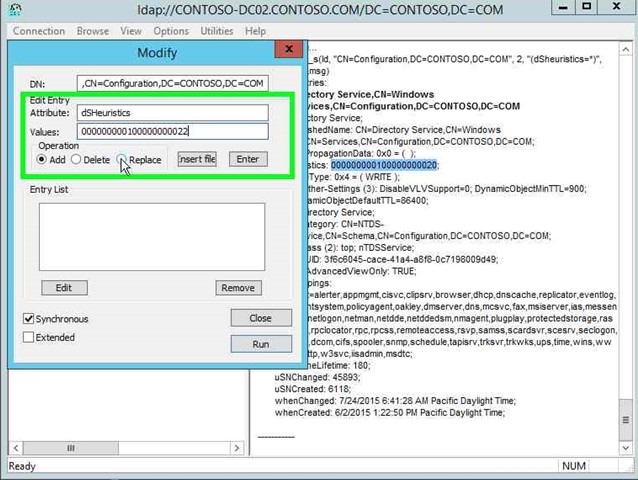
Step 37: Input the new dSHeuristics Value "Values: (edit)" in "Modify".
|
|
Step 38: Click on "Replace (radio button)" in "Modify". |
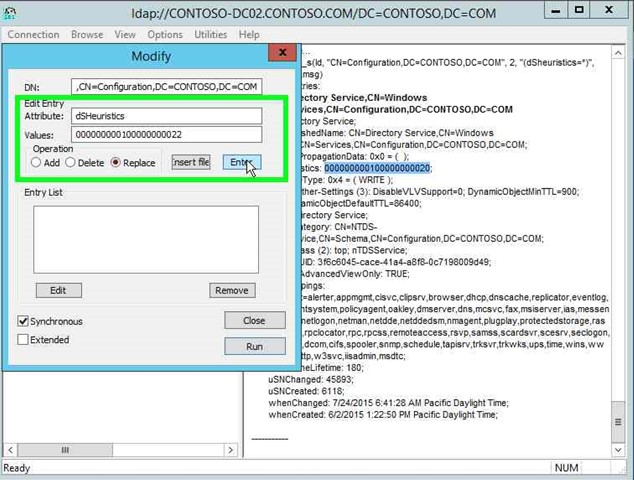
|
Step 39: Click on "Enter (button)" in "Modify". |
|
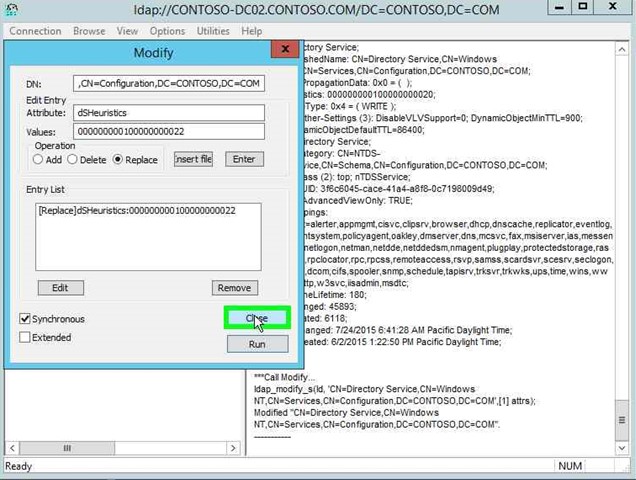
Step 40: Click on "Run (button)" in "Modify". |
|
Step 41: Click on "Close (button)" in "Modify". |
|
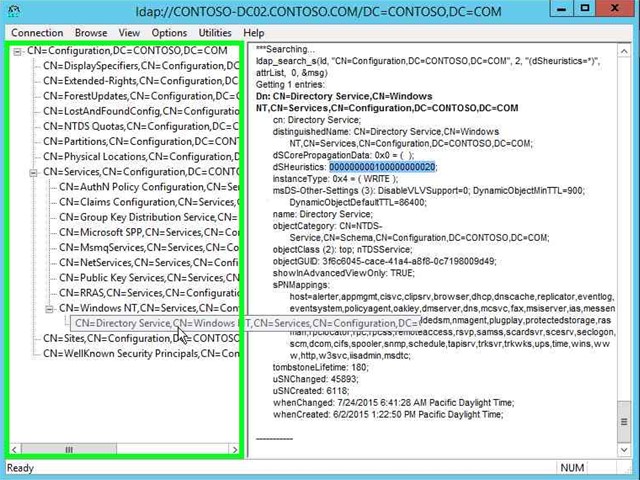
Step 42: To ensure the value has changed you can re-run the search you performed earlier to verify the value changed. |
|
Allow the changes to replicate across AD and you should be able to now use your third party AD migration tools without getting the duplicate SPN error!
Thanks to Mike Kline and Mike Hildebrand for the help and review. Cheers!
Chad