Honey....have you seen my keys?
Well, it happens sooner or later. Someone (probably you) ends up setting your keys somewhere and then spend the next 20 minutes destroying your house looking for them. I actually had a friend who left in his keys inside the refrigerator once. Sad.
When we're talking about recovery keys for your most important, keep-it-secure-always, data....losing the key to unlock the encryption mechanism (yes, I know it's more complicated than this....spare me the finer points of cryptographic arguments please)...is not a good thing. I also know that this is one of the key reasons you guys are wary of deploying the new BitLocker technology in Windows Vista. Well guess what....you're life is about to get better.
As you may (or may not) realize, BitLocker can be set to escrow the recovery keys into your Active Directory. That's a very good thing. We've made it even easier with the release of the new whitepaper entitled "Configuring Active Directory to Back up Windows BitLocker Drive Encryption and Trusted Platform Module Recovery Information". It even includes the VB scripts and LDF files to make all this goodness possible.
No AD? What the heck?
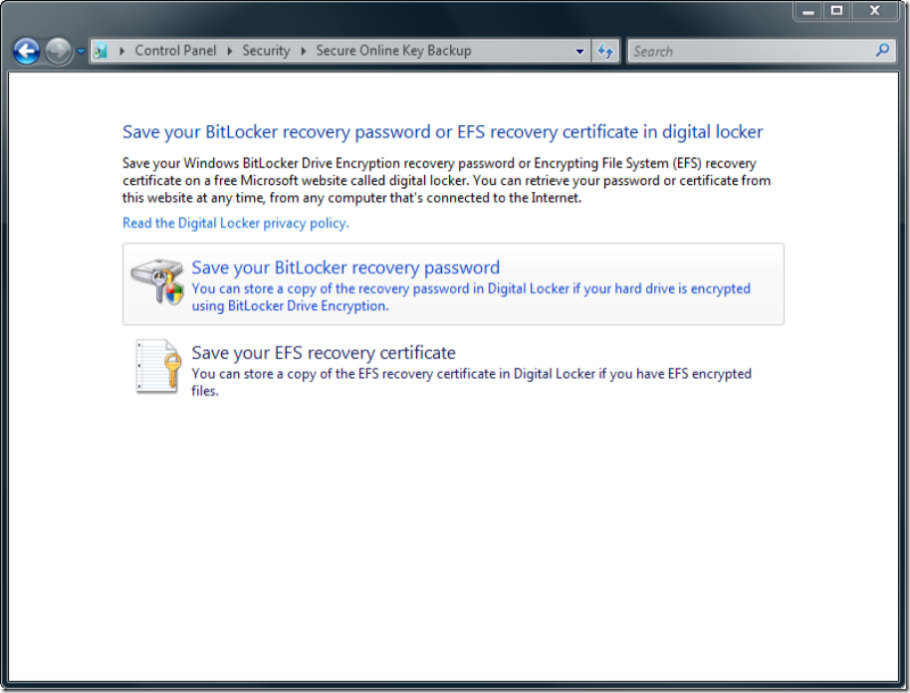
....not an issue....for those without the foresight to install AD in your own house (I know some of you actually do have AD installed at home.....Who needs date night, we got "Honey...I need to extend the schema again!")....you can now retain your BitLocker recovery password and your EFS recovery certificates in your very own Digital Locker at Windows Marketplace. (Still no excuse for not having AD installed at home.....a nice bottle of wine and ADSI Edit.....good times.) The Vista Ultimate team is even going to include an Ultimate Extra called the Windows BitLocker Drive Preparation Tool, that will help you get everything configured properly.