Terminal Services Gateway and Terminal Services Web Access using Hyper-V (Part 3)
Part three of my weekend project involves a little more reconfiguration of my ISA 2006 Server to allow TS Web access the Terminal Services virtual machine running under Hyper-V beta. There are two rules I need to create on the ISA server to achieve this, using a very similar process to the rules I blogged about a couple of years when publishing Exchange through ISA. Essentially I’m going to configure one rule to bounce users to a Forms Based Authentication (FBA) subnet listener where user authentication is made, and another rule to forwards authenticated user traffic from the FBA subnet to the Terminal Server machine itself.
(Yes, I realize I’m probably using all the wrong terminology here, and some ISA guru is bound to correct me!)
This is what the rules like in the ISA 2006 management console.
I won’t go into all the details of how this is configured in detail – please refer back to previous blog posts and blogcasts where there is a lot of detailed information. Just replace “Exchange” with “TS” and you’re largely there. A few points to note though:
- On the “Paths” tab of the rule forwarding from the Internet to the FBA ensure there is a mapping of External Path “<same as internal>” to Internal Path “/ts/*”
- On the “Paths” tab of the rule forwarding from the FBA to the TS Gateway to ensure there is a mapping of External Path “<same as internal>” to Internal Path “/ts/*”
- On the Authentication Delegation tab of the rule forwarding from the FBA to the TS Gateway, select “Negotiate (Kerberos/NTLM)” with an SPN of “http/<internal dns name of the TS gateway>”
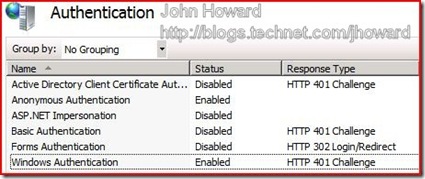
The above allows me to go to an external path of https://externaldomainname.com/ts to access Terminal Server Web. However, before that, you also need to allow Windows Authentication in IIS on the Terminal Services virtual machine. To do this, start Internet Information Services (IIS) Manager, click on the local machine and choose the authentication option. Right click on Windows Authentication, and enable it.
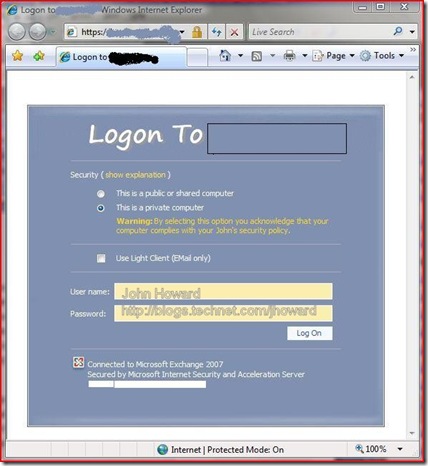
So with that all done, let’s give it a go. Start up your browser and point it to https://externaldomainname/ts. With a bit of customization I’ve made to the front end Forms Based Authentication screens you see below, you get a logon dialog. Here, I’m going to authenticate as myself.
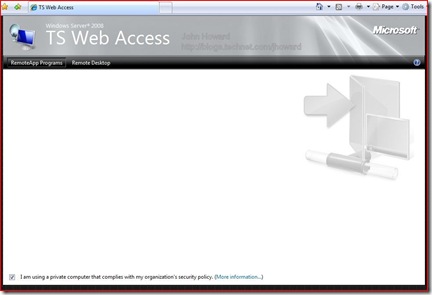
Currently, there are no remote applications, so the list is empty. In the next and last part, I’ll fix that and add the Hyper-V management programs to the list.
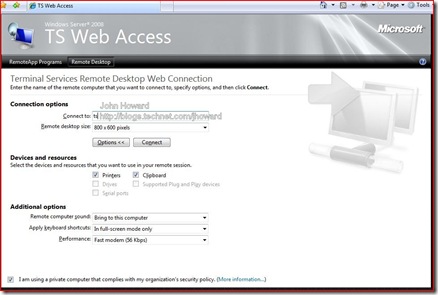
Note also that there is a remote desktop tab which allows another way of accessing remote desktops without having to configure the mstsc client directly.
Just for kicks, let’s logon to the TS Gateway machine using TS Web Access this time where you can see I still have IIS admin open after setting the authentication methods.
So we’re nearly there. The last thing to do is to add the Hyper-V management tools to TS Web Access to allow me to control my Virtual Machines remotely over the Internet. Part 4 soon!
Cheers,
John.