Implementing Secure Wireless Networking - Part 2
Continuing the configuration of a secure wireless network, this part deals with configuring the IAS server to recognise authentication requests from your wireless device. The first part of configuring IAS is configuring a RADIUS client. In this case, it is the wireless box. There's a simple wizard built into IAS to walk you through this.
Right-Click RADIUS Clients and select new client
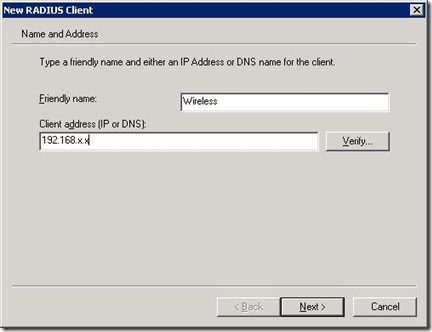
Give it a friendly name and the IP address of assigned to your wireless device (note I'm disguising my actual IP address range and internal domain names in this article).
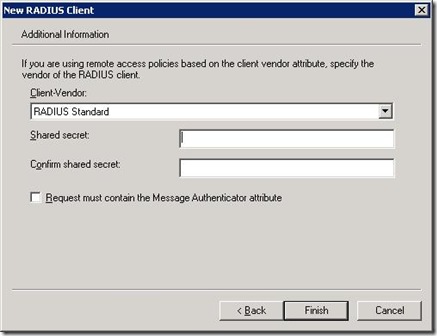
If your wireless vendor supports RADIUS standard, choose this. Otherwise, from the drop-down list, choose the appropriate setting. Also now re-type the shared secret password you configured on your wireless box. NOW you see why I recommended the use of notepad in the previous article :)
Finally, your screen should look similar to below
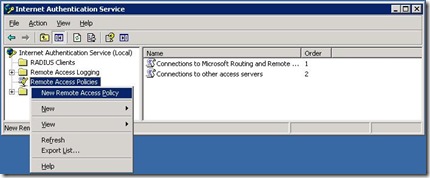
Next you need to configure a wireless access policy in IAS. If you select the Remote Access Policy node in the IAS MMC, you'll see a couple of default policies. In our case, we need to configure a new access policy for wireless. Fortunately, again everything can be configured through a wizard.
Right-click on Remote Access Policies and choose "New Remote Access Policy"
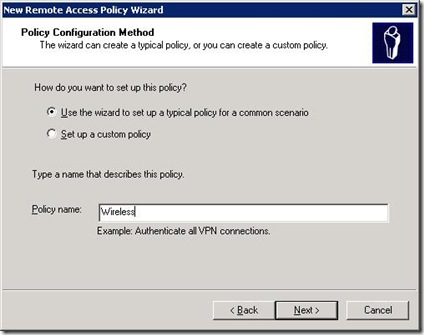
 After the intro page to the wizard, a typical policy is probably sufficient for most needs. Give it an appropriate name such as, logically I guess, Wireless
After the intro page to the wizard, a typical policy is probably sufficient for most needs. Give it an appropriate name such as, logically I guess, Wireless
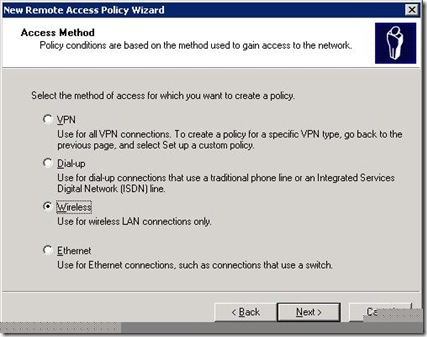
On the next page, choose Wireless
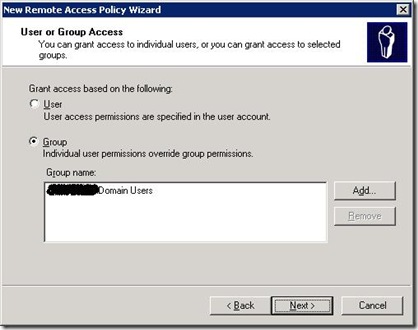
On the next page, select the appropriate groups from Active Directory you wish to allow wireless access to. You may wish to allow all users, or maybe just selected users (in my personal case I have a specific group for wireless access - the reason for this may become apparent later on when it comes to adding accounts from un-trusted domains. The screen shot just shows domain users though).
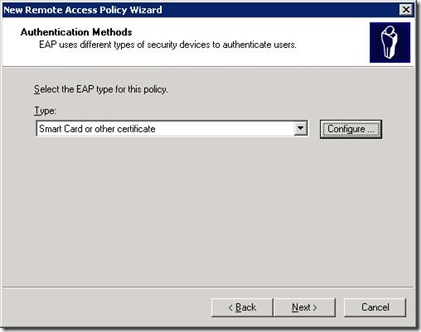
Now comes the important part. On the next screen, for the EAP type for this policy (assuming you do want this secure), use Smart Card or other certificate.
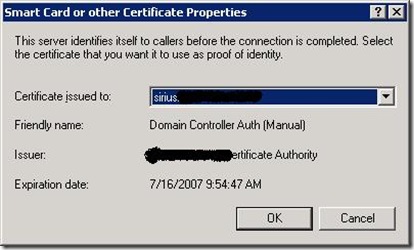
Click the configure box. At this point, you'll realise you need a certificate authority (but hopefully that will be obvious).
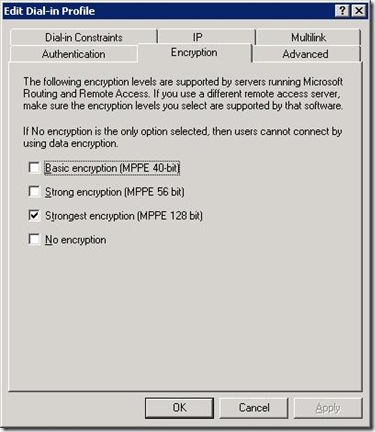
If you're astute, you'll notice in my case I have a certificate for Domain Controller Authentication being issued to the DC. That in itself was a little challenging, but the CA documentation is pretty readily available online :) That's pretty much the end of the wizard. Once the wizard is complete, it's worth revisiting the settings for the wireless policy and ensure that the only encryption setting checked is that for strongest encryption - by default, all encryption settings are allowed.
At this point, you're pretty much there for the basics. I guess it's group policy next. (It may be a few days to prepare the next blog post part - takes a while to prep the screenshots and walkthroughs).
Cheers,
John.