Using RBA To Separate Servers And Workstations In Configuration Manager 2012
Overview:
A question I see come up a lot is how can I Delegate permissions for my Server Team to only see/manage servers and my Desktop Team to only see/manage desktops in Configuration Manager?
In Configuration Manager 2007, the best option was to have two completely different Configuration Managers sites(One site for servers and one for desktops).
In this Post/Guide, I'm going to walk through the process of using Role-Based Administration in Configuration Manager 2012 to achieve this in a Single Primary Site.
My Environment:
- CMServerAdmin = Domain account that will be to demonstrate a Server administrator.
- CMDesktopAdmin = Domain account that will be to demonstrate a desktop/workstation administrator.
- AD Global Security Group named CM Server Admins CMServerAdmin is part of this group
- AD Global Security Group named CM Desktop Admins CMDesktopAdmin is part of this group
- Standalone Primary Site = PRI
How It Works:
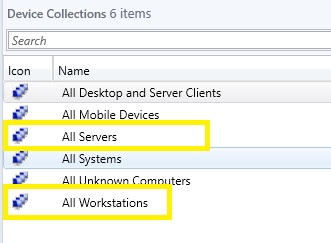
The first step you will need to do is create two collections one for Servers and one for Desktops/Workstations. If you wanted to delegate permissions to computers by location(e.g. United States & Canada) you would simply create a collection of machines based on location (This can be used for more than just separating Server & Desktops).
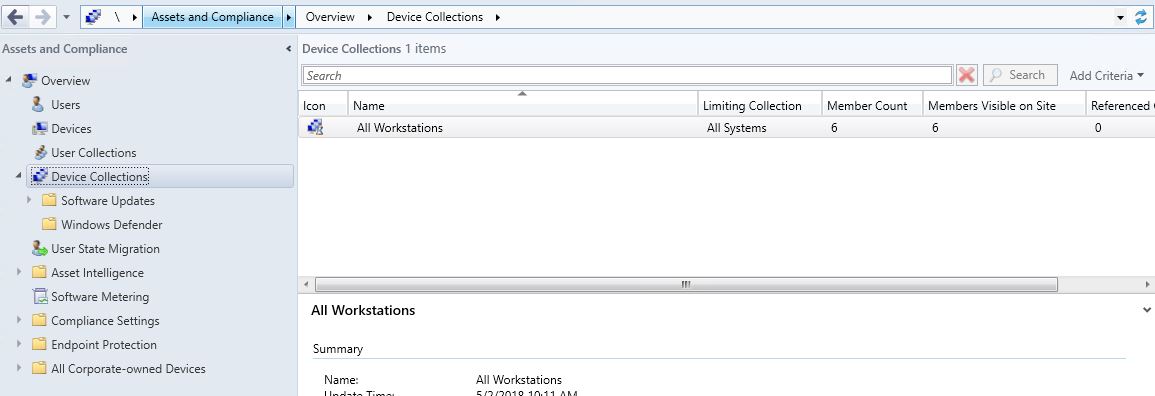
I'm going to start by creating my Desktop Collection. If you wanted to delegate permissions based on something other than Servers/Workstations name your collection accordingly.I'm going to name this collection All Workstations.
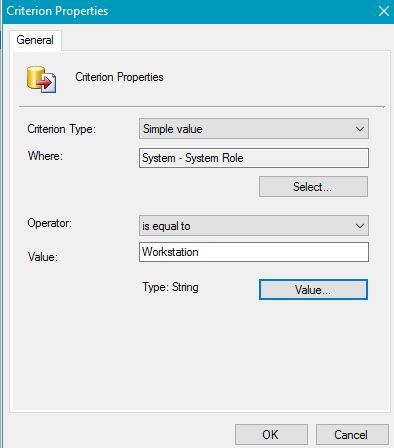
You will need to create a Query to find all Desktops/Workstations. I used a WQL Collection Query to find where (System Role = "Workstation") . See an example below:
Since this collection is going to be used as our limiting collection for all other Workstation/Server collections, it would make sense to use "Incremental Updates" for this collection. 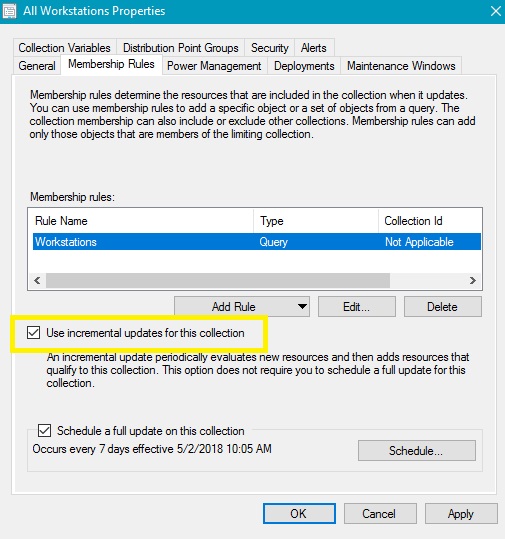
You will want to repeat this process to create a collection for Servers. Obviously, we will want to change the Collection Name and the Query. In the Query, use where (System Role = "Server") .
You should see your All Workstations and All Servers collection now. 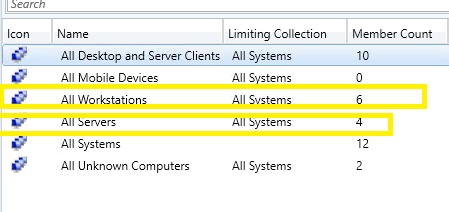
Next we will add two new "Administrative Users" to our site: 
I will start by adding my CM Desktop Admins group. You will need to add a Security Role for your group (I used Full Administrator but any will work) . You will also need to change the Collection this group can manage. Since this in the Desktop Admin group, I assigned *ONLY* the All Workstation Collection. 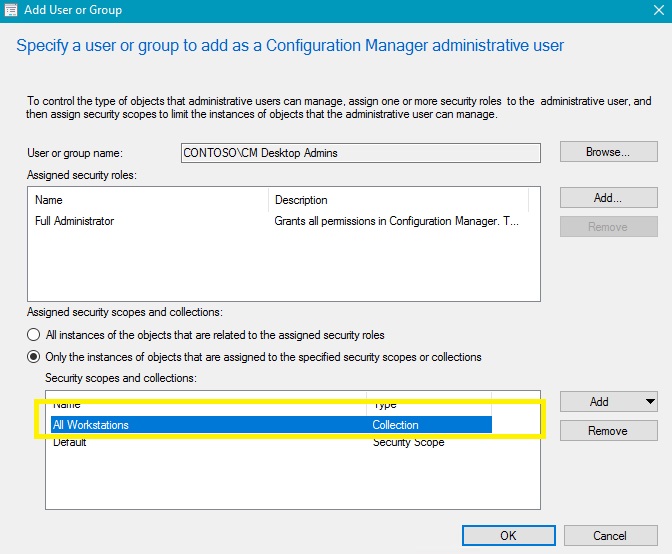
Repeat this process for the CM Servers Admins group make sure you change the collection they can manage to your "All Servers" collection.
Here's a Screenshot of both of my New Administrative Groups: 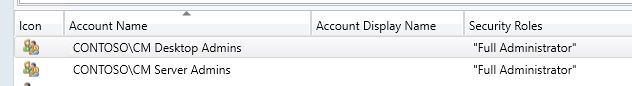
Now that we have our groups setup so they can only see the collection assigned to them. We should be able to check out the console for each of these users.
The Screenshot below is how the devices node will look when CMDesktopAdmin (Or any user part of CM Desktop Admins Group) is logged in. You can see that the only devices this user can see is devices in the "All Desktops" collection.
Here is how things will look logged in as CMServerAdmin: 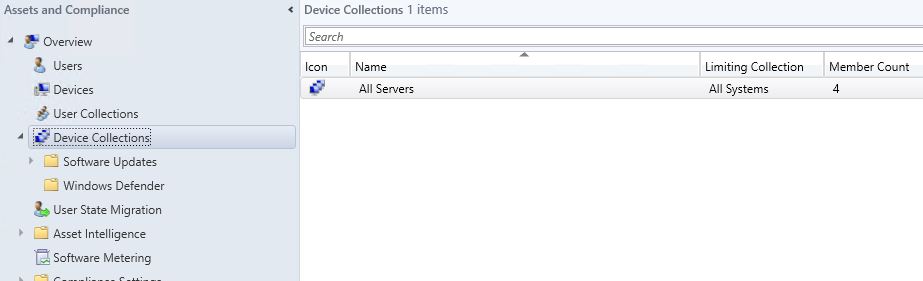
Wrapping Up:
This post showed you how you can use the new Role-Based Administrative model in Configuration Manager 2012 to allow certain Users/Groups to only be able to manage certain resources.
Limiting certain users/groups to certain collections with RBA can help with the following (To name a few):
- Ensure that CM administrative users can only see Resources they need to
- Ensure that CM administrative users can only create collections that are limited to the collection they are able to manage
- Ensure that CM administrative users can only create deployments to Resources they are approved to manage
Hope this helps!
Disclaimer: The information on this site is provided "AS IS" with no warranties, confers no rights, and is not supported by the authors or Microsoft Corporation. Use of any included script samples are subject to the terms specified in the Terms of Use