Creating Yammer Relying Party Trust in ADFS
Yammer supports any SAML 2.0 compliant Identity Provider (IdP). These include ADF 2.0 & 3.0, Windows Azure AD, Shibboleth, OneLogin, PingFed, Okta etc. The first step to implementing Single Sign-On (SSO) with Yammer is to open a yammer SSO service request. You will be asked to provide your IdP metadata and token signing certificate so you may want to speed up the data collection phase by providing the required files as soon as you open the service request. In the case of ADFS IdP, the metadata can be downloaded from - https://your-server-URL/FederationMetadata/2007-06/FederationMetadata.xml and you may use this instruction to extract the token signing certificate. You should zip the token signing certificate before sending it to the Yammer support rep. because .cer files are quarantined by Microsoft IT.
Once you’ve provided the required files, Yammer support will create the connection and respond back with the Yammer Service Provider (SP) metadata. At this point, the connection is inactive and there will be no impact on users' experience. Download the metadata file and start the process of creating the relying party trust and claims rule as described below.
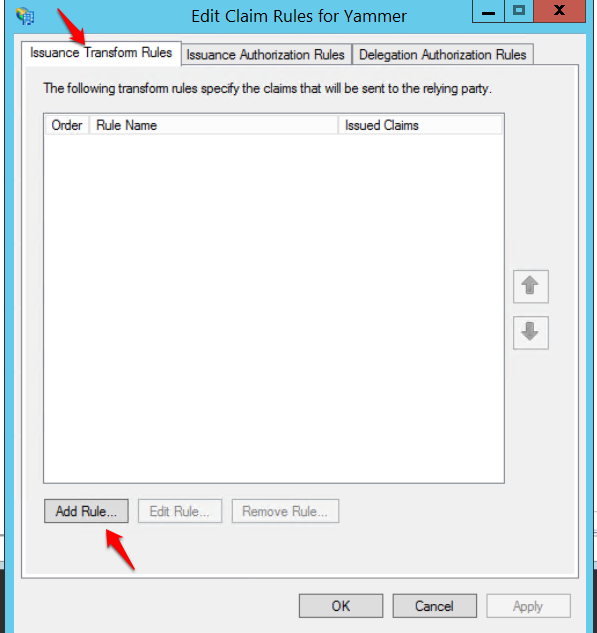
Add Relying Party Trust
- In ADFS Management Console, navigate to Trust Relationships ->Replying Party Trusts
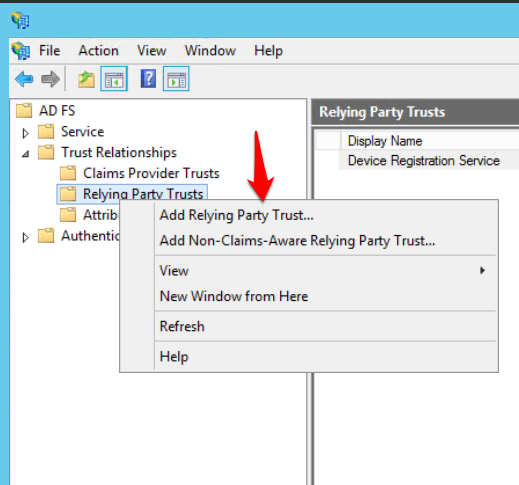
- Right Click Relying Party Trusts and click Add Relying Party Trust
- Click Start
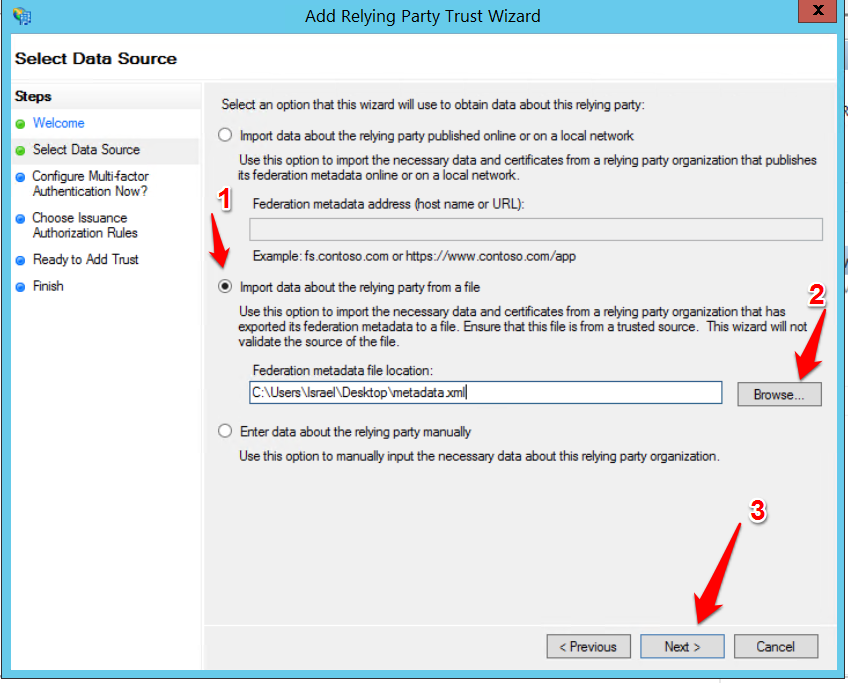
- Select "Import data about the relying party from a file", browse to the metadata file that was provided by Yammer Support and click Next.
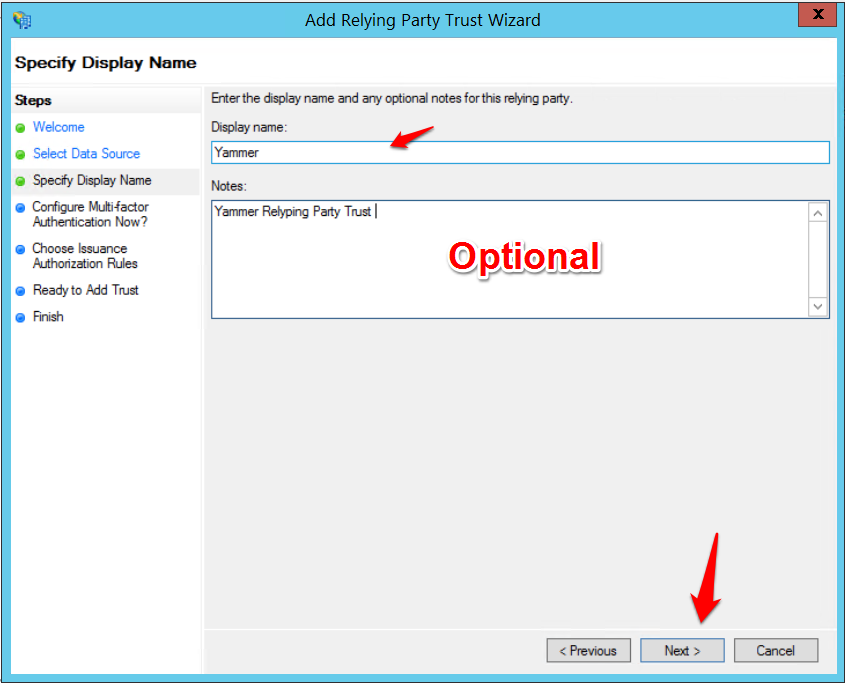
- Add a Display name (and Notes if necessary) and click Next
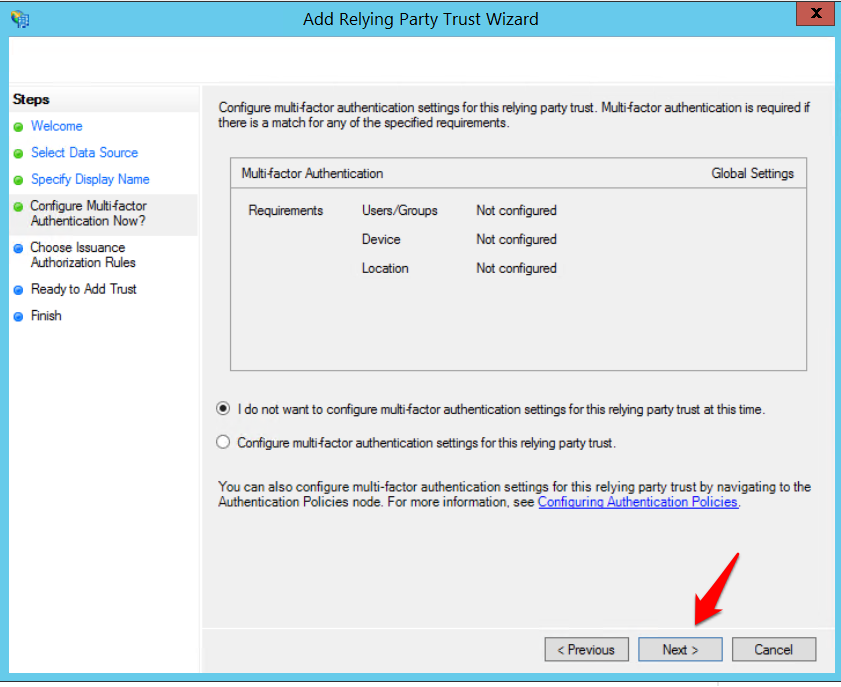
- Multi-factor authentication is not required, click Next
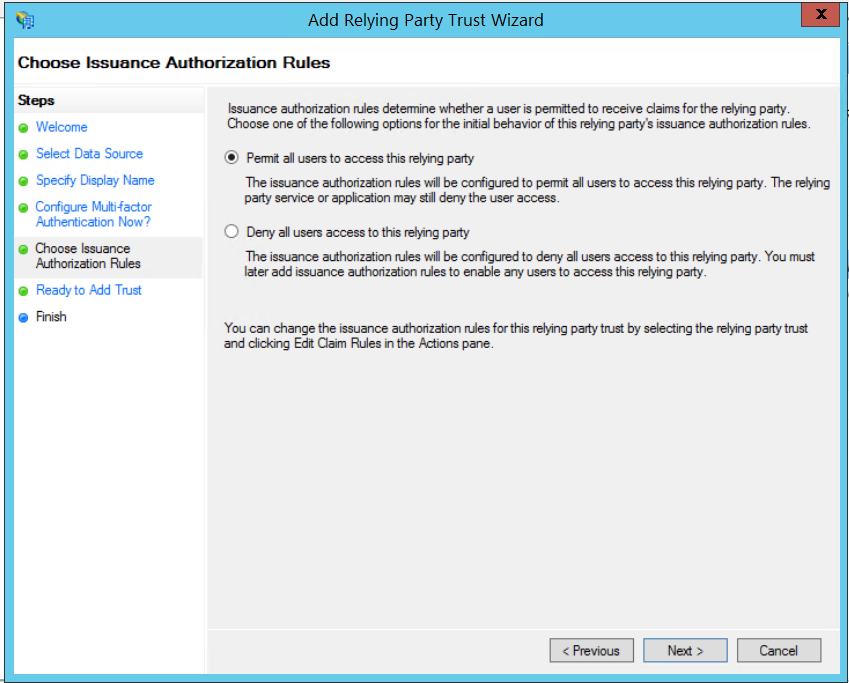
- Permit all users to access this relying party, Next.
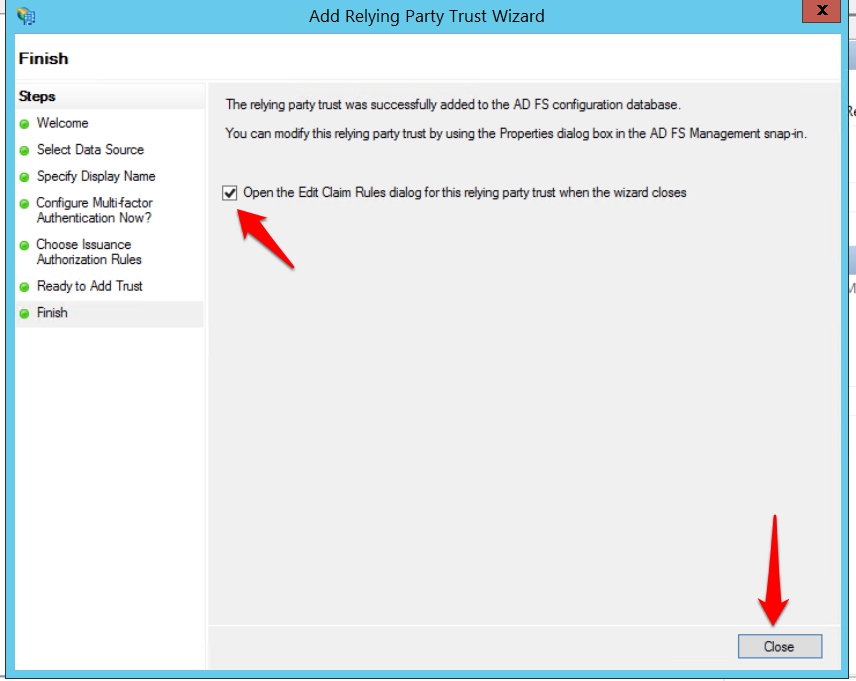
- Check the Edit Claim Rules box
Edit Claim Rules for Relying Party Trust
- In the Issuance Transform Rules tab, click Add Rule
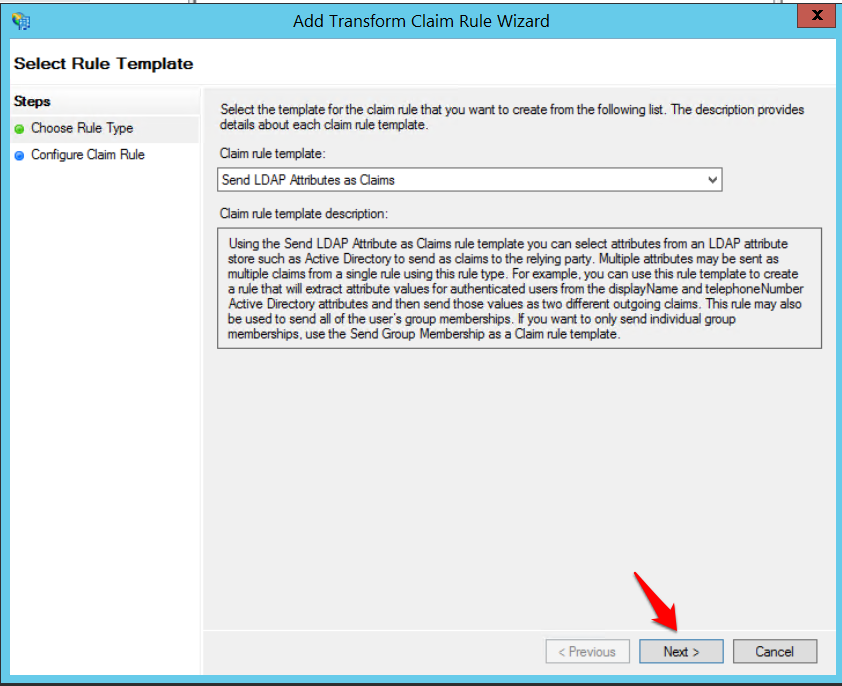
- In the Select Rule Template, leave "Send LDAP Attributes as Claims" selected
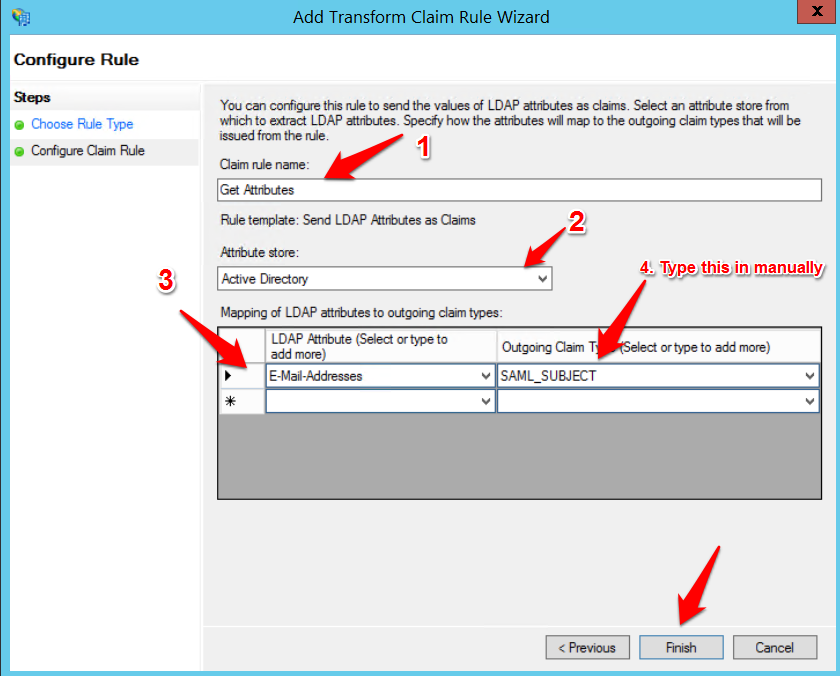
- In the Configure Claim Rule page, enter Get attributes in the Claim rule name box
- In the Attribute store list, select Active Directory
- In the Mapping of LDAP attributes create the following mappings: E-mail-Addresses - SAML_SUBJECT
- Click Finish
The outgoing claim type value (SAML_SUBJECT) is not listed in the drop down so it will need to be typed in and it is case-sensitive.
Testing your Single Sign-On Connection
The concept of UAT environment does not exist in Yammer so you'd need to test your SSO connection in your production network. Next steps are, decide on a suitable off-peak period to test SSO, give a heads up to your users by posting a yammer announcement. Plan your SSO test-case and then respond to Yammer support with the decided date and time. The test should last no more than 45mins if everything goes well .
At the end of the test, you may ask the Support representative to disable SSO connection to allow you to plan for a Go-Live date. Switching between SSO and non-SSO connection does not affect users' contents and/or credentials.
Lastly, if you want to restrict yammer access to a subset of users, which is the main reason most customers use Yammer SSO instead of Office 365 sign-in for Yammer, please refer to this blog.
[bing_translator]