New in Forefront TMG SP1: Redirect on Deny with dynamic parameters
Introduction
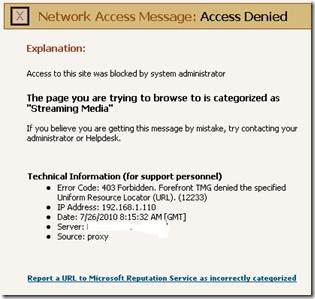
While acting as proxy, Forefront TMG can allow or deny Web traffic originating from the protected web clients. In case of denied traffic Forefront TMG sends to the client an error page to display in the browser. The page contains basic information about the reason the traffic was denied:
The major limitation of these pages (in Forefront TMG RTM) is that they must be self-contained single pages. That means, they cannot contain images and cannot load other pages since they're viewed in the context of the originally requested page (the one that was denied). By default the pages are localized to the Forefront TMG installation language and due to the limitation they cannot be customized to dynamically adjust to the viewing browser locale.
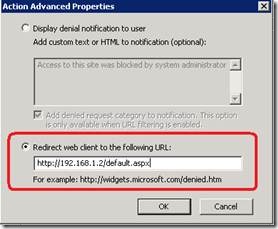
Instead of showing these error pages upon denied access, the Forefront TMG administrator may configure the denying rule so that the proxy would respond to the denied request with a redirect to another URL (typically residing within network protected by Forefront TMG):
After the redirect, the target page is free of the built-in error pages’ limitations because of the explicit redirect resulting in the correct browsing context. However, new limitations are introduced – after the redirect all the data related to the denial reason is lost.
The "Redirect on Deny with dynamic parameters" feature that was released with Forefront TMG SP1 allows the administrator to specify a token in the redirection URL, which is substituted with run-time data each time the redirect is enforced.
Feature Description
In Forefront TMG SP1 the administrator can use the following token in a redirection URL:
[DESTINATIONURL] – substituted with the originally denied URL.
[URLCATEGORYNAME] – substituted with denied URL Category name in the Forefront TMG installation language.
[URLCATEGORYID] – replaced with a number representing the denied URL Category Id, necessary if you want to display the URL category in a language different from the Forefront TMG installation language.
[OVERRIDEGUID] – replaced w/ an array GUID which is to be used for user override feature purposes.
For example, a web user tries to access www.contoso.com, which is categorized as "Entertainment". Forefront TMG policy is configured to redirect "General Business" requests to http://192.168.1.2/Default.aspx?OrigUrl=[DESTINATIONURL]&Category=[URLCATEGORYNAME]&CategoryId=[URLCATEGORYID]
After the proxy renders the token, the user will get redirected to:
http://192.168.1.2/Default.aspx?OrigUrl=www.contoso.com&Category=Entertainment&CategoryId=82
It's the administrators' responsibility to ensure that http://192.168.1.2/Default.aspx exists, is accessible and handles passed parameters correctly.
Here's a sample script that would handle this specific redirection syntax:
<%@ Page Language="VB" validateRequest=false %>
<HTML>
<BODY>
<span id="Url">Url = <%Response.Write(Server.HtmlEncode(Request.Params("OrigUrl")))%><br></span>
<span id="Category">Category = <%Response.Write(Server.HtmlEncode(Request.Params("Category")))%><br></span>
<span id="CategoryId">CategoryId = <%Response.Write(Server.HtmlEncode(Request.Params("CategoryId")))%><br></span>
</BODY>
</HTML
After server side rendering, the HTML source will look like this:
<HTML>
<BODY>
<span id="Url">Url =www.contoso.com<br></span>
<span id="Category">Category = Entertainment<br></span>
<span id="CategoryId">CategoryId = 82<br></span>
</BODY>
</HTML>
Note:
In the given example we used the InnerText property and the Server.HtmlEncode function to prevent cross-site scripting.
We recommend sticking to this example pattern when creating custom error pages designed for Forefront TMG redirections.
Additional aspects
HTTPS inspection
In order not to disclose the sensitive information that can be contained in the path and\or parameters of a denied HTTPS URL, we can't forward the whole URL to the redirection page. Due to privacy reasons (since redirect can be done on non-encrypted channel), only the hostname of the denied URL will be shown in this case:
If user tried to access https://contoso.com/some _secret_path,
In case of HTTPS inspection enabled he'll see in the sample:
Url: https://contoso.com...
In case of HTTPS inspection disabled he'll see
Url: contoso.com:443
Long URLs
As defined in IE RFC, the maximal URL length that can be processed is 2047 (browser limitation). So if the redirection URL grows larger than this number due to token substitutions, the original denied URL parameter will be cut to fit the size. In this case an appendix of <...> will be appended to indicate that the URL was cut.
Author: Dima Datsenko
Reviewers: Ori Yosefi, Nathan Bigman