Creating a Web Access Policy for Your Organization
Forefront TMG introduces the Web Access Policy Wizard to help you create Web access rules and Web protection settings for your organization. You can launch the wizard from the completion page of the Getting Started wizard, or by navigating to the Web Access Policy node and selecting the Configure Web Access Policy option.
Note that in ISA Server 2004 and 2006, default access rules were created based on the policy selection in the Network Templates wizard. In Forefront TMG, the access rules are now created using the Web Access Policy Wizard, allowing you to configure rule properties and Web protection feature settings. All settings configured using the Web Access Policy wizard can be modified after completing the wizard, using the property pages.
Creating Default Web Access Policy Rules
When you run the Web Access Policy Wizard, a default rule allowing Web access from clients on the Internal network to the Internet is created for you. Based on your selections in the wizard, a default blocking rule may also be created and Web protection features, such as URL filtering, are enabled and applied.
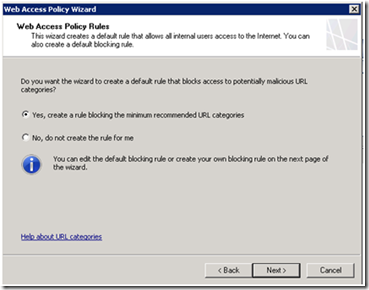
The Web Access Policy Rules page lets you select if you want URL categories deemed harmful to the productivity or security of your organization automatically included in the default Blocked Web Destinations rule, or if you prefer to create the rule yourself.
Regardless of which option you choose in this page, the Blocked Web Destinations page, used to create the blocking rule will display when you click Next. |
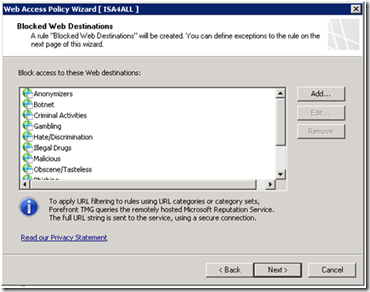
The rule will block access to all Web destinations listed in thispage. If you selected to have the rule created for you, a list of blocked URL categories is populated for you. If you selected no, the list is not populated. Use the options provided to add or modify the list. Note that if no destinations added to the list, the blocking rule will not be created. |
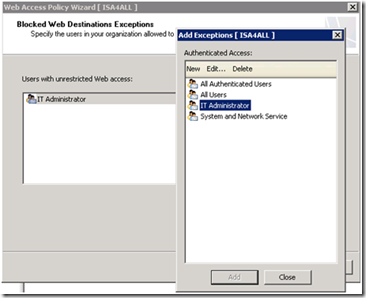
By default, the Blocked Web Destinations rule is applied to all users. The Blocked Web Destinations Exceptions page lets you specify users or groups for whom the rule should not be applied. |
Configuring Web Protection Features
After creating the default rules, you can configure Forefront TMG to inspect content requested from the Internet for malware such as viruses and spyware.
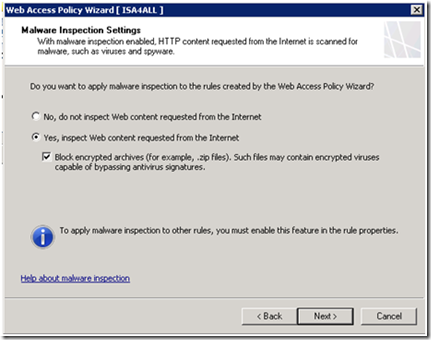
Configuring Malware Inspection Settings
The Malware Inspection Settings page lets you enable the Malware Inspection feature and apply the global settings for this feature.
You can view and modify global malware inspection settings, such as the content delivery method, in the Malware Inspection property pages after completing the wizard. You can also configure rule-specific settings for each access rule for which malware inspection is enabled. |
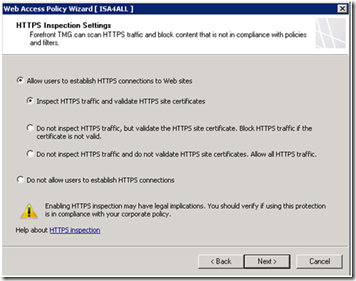
Configuring HTTPS Inspection Settings
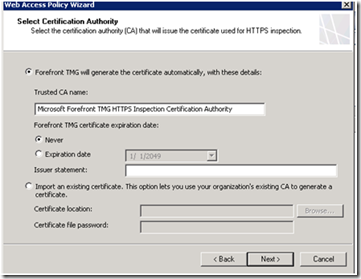
The HTTPS Inspection Settings page lets you specify if HTTPS connections are allowed and define how HTTPS inspection is applied to HTTPS traffic. If you select to allow HTTPS connections, the HTTPS protocol is added to the default allow rule.
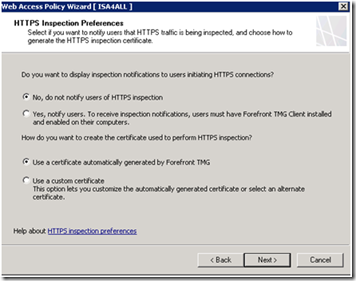
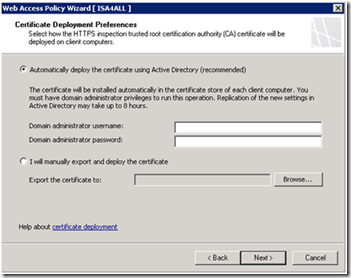
Depending on the certificate option you select, additional settings are provided.
After completing the wizard, you can use the HTTPS inspection property pages to define any sites exempt from HTTPS inspection and to specify if certification validation should be applied.
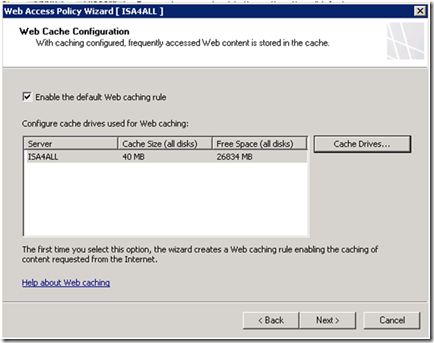
Enabling Web Caching
The final step in the wizard is to create and enable the default Web caching rule and define the default cache drive.
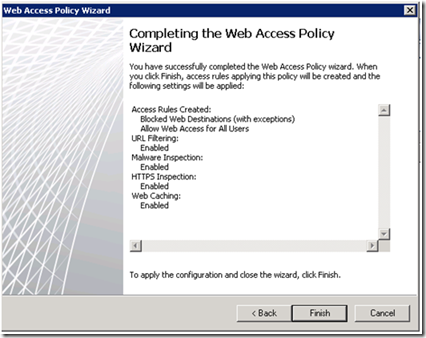
The completion page shows the settings that will be applied. Based on these settings, Web protection features are enabled and the default Web access policy rules are created.
Viewing the Policy Rules and Settings
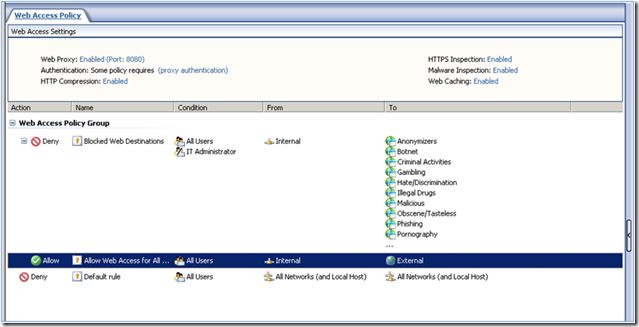
When you click Finish to complete the wizard, the Web access settings and rules are shown in the Web Access Policy results pane. You can view and modify the rule settings by opening the rule properties (either by double-clicking on a rule, or using the right-click menu). You can view and configure Web protection settings using the links in the Web Access Settings pane to open the corresponding property pages. Links to these property pages are also accessible from the Web Access Policy toolbar and the tasks pane.
The rules created in the Web Access Policy node are also listed in the Firewall Policy rules list. You can view and edit rule settings in either location.
Frequently Asked Questions
Q: How do I add other access rules to the Web Access Policy Group?
A: Selecting the group header, or a rule in the group, and then creating the new rule will put the rule into the group. You can also use the ungroup and move up or move down options available by right-clicking on a group header or rule to move rules around. Note that it is not necessary to add access rules created manually to this group. Rules are processed in order, regardless of groupings.
Q: How do I know if URL filtering is enabled? I don’t remember enabling it in the Web Access Policy wizard.
URL filtering is enabled automatically when URL categories are selected in the default blocking rule. The feature may also be enabled when running the Getting Started Wizard. You can view the URL filtering properties and settings by clicking the Configure URL Filtering option in the toolbar or tasks pane.
Q: What is the difference between the Web Access Policy group in the Firewall Policy node and the Web Access Policy group in the Web Access Policy node?
A: There is no difference. These are the same rules and can be edited in both places.
Q: What is the difference between the Create Access Rule option in the Web Access Policy node and the Create Access Rule option in the Firewall Policy node?
A: Both options launch the same Create Access Rule wizard. However, when launched from the Web Access Policy node, the HTTP and HTTPS protocols are preselected for you. You can add or remove protocols when running the wizard from either location.
Written by: Linda Lior
Edited by: Gabriel Koren, TMG Test Team