TMG Client introduces automatic detection using Active Directory
1. Introduction
The new TMG Client that is available on TMG 2010 is now capable of performing automatic discovery using a record that resides on Active Directory. TMG Client still able to use the traditional methods (DHCP / DNS) for automatic discovery, the difference now is that if both options are enabled on UI (see Figure 1) the auto detection will take effect using the following flow:
1. TMG Client will first try to retrieve information from Active Directory using LDAP query.
2. If TMG Client is unable to retrieve that information due to an error with the connection, it won’t failover to DHCP / DNS automatic detection methods for security reasons. This reduces the risk that an attacker might try to force fallback to a less secure method by affecting Active Directory marker availability. Active Directory discovery is considered more secure than DHCP/DNS methods.
3. In case that the connection succeeded to Active Directory but no information was found the TMG Client will failover to DHCP and then to DNS.
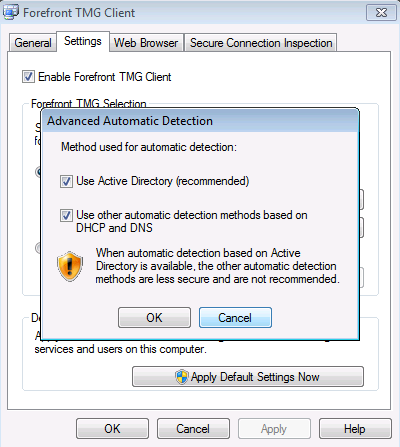
Figure 1 – TMG Client
In order to configure Active Directory to support that you should use the TMG Auto-Discovery Configuration Tool (TmgAdConfig.exe). This tool configures an Active Directory with a marker key that points to your Forefront TMG server. This key is going to be used by the TMG Client to locate the Forefront TMG server and connect to it.
Note: Active Directory-based auto detection works only for computers that are members of a domain. Use of AD Marker in workgroups is not supported.
2. Using TMGADConfig Tool
You can download the TMG AD Config Tool from Microsoft Download Center (look for the AdConfigPack.EXE). After download and install on TMG you can execute the following command line in order to register the AD marker key:
tmgadconfig add -default -type winsock -url http://ftmgfw.contoso.com:8080/wspad.dat
Forefront TMG Auto-Discovery Configuration Tool
New Winsock default marker successfully registered.
Note: to see more switches for this command used TMGAdConfig /?
The highlighted part is the one that will change according to the TMG’s FQDN and also the port used by TMG. When you run this command line TMG will send an LDAP request to the Domain Controller asking for the registration of this marker key. Here it is a sample of the LDAP traffic caused by this execution of this command line:
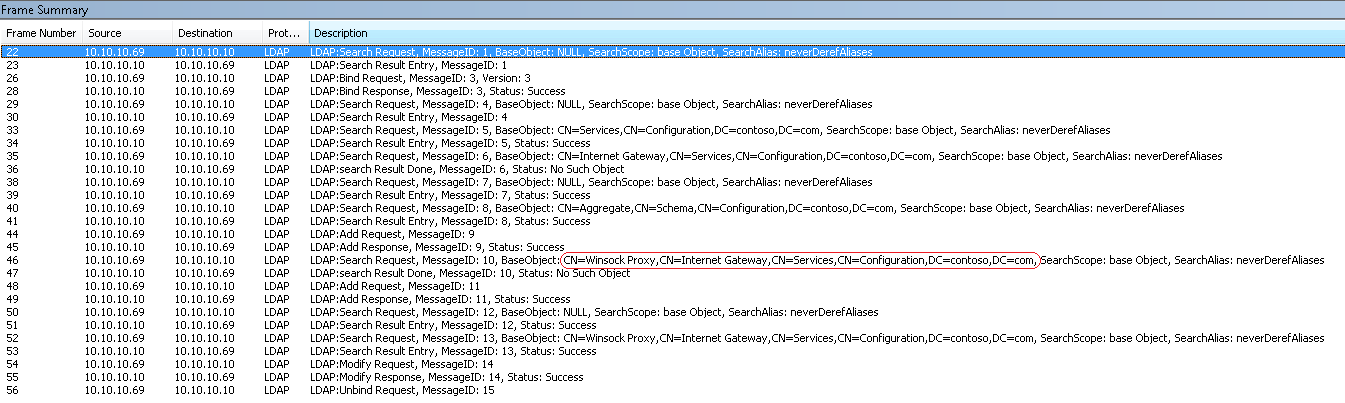
Figure 2 – Typical LDAP Traffic (click here to enlarge this picture).
Note: on this example TMG is 10.10.10.69 and the DC is 10.10.10.10
The LDAP search that is marked in the above traffic sample is exactly the location where this marker will be registered. If you use LDP.EXE you can browse through the location shown below:
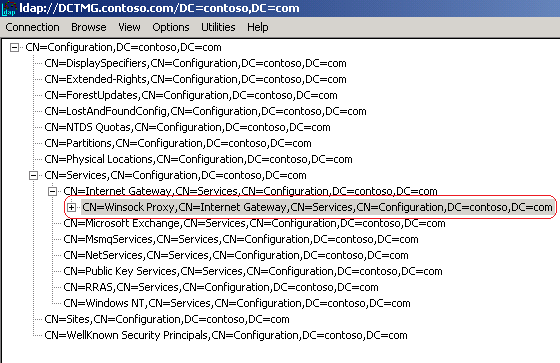
Figure 3 – LDP Tool result.
When accessing this location, the right panel should show the value that has the TMG AD Marker that was registered as shown below:
Expanding base 'CN=Winsock Proxy,CN=Internet Gateway,CN=Services,CN=Configuration,DC=contoso,DC=com'...
Getting 1 entries:
Dn: CN=Winsock Proxy,CN=Internet Gateway,CN=Services,CN=Configuration,DC=contoso,DC=com
cn: Winsock Proxy;
distinguishedName: CN=Winsock Proxy,CN=Internet Gateway,CN=Services,CN=Configuration,DC=contoso,DC=com;
dSCorePropagationData: 0x0 = ( );
instanceType: 0x4 = ( WRITE );
keywords (2): Winsock Proxy; ISAServer;
name: Winsock Proxy;
objectCategory: CN=Service-Connection-Point,CN=Schema,CN=Configuration,DC=contoso,DC=com;
objectClass (4): top; leaf; connectionPoint; serviceConnectionPoint;
objectGUID: a87cf902-1b5a-4532-a9cb-bef8dd663fed;
serviceBindingInformation: http://ftmgfw.contoso.com:8080/wspad.dat;
serviceClassName: Winsock Proxy Service;
showInAdvancedViewOnly: TRUE;
uSNChanged: 496989;
uSNCreated: 496988;
whenChanged: 10/22/2009 9:08:54 AM Pacific Daylight Time;
whenCreated: 10/22/2009 9:08:53 AM Pacific Daylight Time;
3. Testing Client Configuration
To test the configuration on the client side you can use the FWCTool that comes with TMG Client, which is installed by default in %programfiles%\Forefront TMG Client folder. Follow the steps below to perform this test:
1. On the client workstation, open command.
2. Navigate to the location where TMG Client is installed.
3. Run the command fwctool TestAutoDetect
Here it is an output sample of this command when perform all tests successfully:
FwcTool version 7.0.7733.100
Forefront TMG Client support tool
Copyright (c) Microsoft Corporation. All rights reserved.
Action: Test the auto detection mechanism
Type: Default
Detection details:
Timeout is set to 60 seconds
Locating WSPAD URL on the Active Directory server
WSPAD object was found in the global Active Directory container
WSPAD URL found on the Active Directory server:
http://ftmgfw.contoso.com:8080/wspad.dat
Initializing Web server connection
Resolving IP addresses for ftmgfw.contoso.com
Resolved 1 address(es):
10.10.10.69
Connecting to address #1: 10.10.10.69:8080
Waiting for address #1 to connect
Address #1 successfully connected
Requesting wspad.dat file
Web server is connected and ready to send WSPAD file
Downloading WSPAD file
WSPAD file was downloaded successfully
Detected Forefront TMG: FTMGFW:1745
Result: The command completed successfully.
The highlighted text above is your confirmation that the AD registration was correctly found by the TMG Client.
Author
Yuri Diogenes
Sr Security Support Escalation Engineer
Microsoft CSS Forefront Edge Team
Technical Reviewers
Bala Natarajan
Sr Security Support Escalation Engineer
Microsoft CSS Forefront TMG Beta Team
Eric Detoc
Escalation Engineer
Microsoft CSS Forefront TMG Beta Team