Understanding HTTP logging in Microsoft Forefront TMG
Consider a firewall policy which contains two Web access rules:
1. My Public Restrictive access rule- Allow traffic from internal network to a restricted set of URLs on the external network.
2. My Private Permissive access rule- Allow traffic from a limited subnet to all destinations on the external network.
As a simple example, at home you allow all computers to access a restricted set of URLs which are safe for children, and allow your personal computer to access everything on the Internet.
With this scenario, logging may be non intuitive for secureNAT clients.
Consider your personal computer accessing a destination which is not in the restricted url set. The traffic will be matched by the “My Private Permissive access rule” rule.
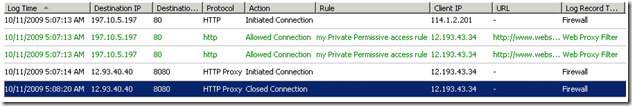
If your computer is configured as a Web proxy client, the logging is as expected:
The traffic is allowed by the “My Private permissive access rule”. Traffic to port 8080 is logged too.
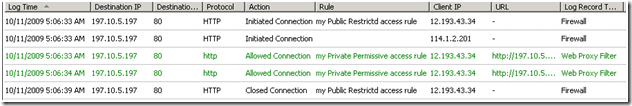
On the other hand, if your computer is configured as a secureNAT client, the logging is as follows:
Unexpectedly, the traffic is allowed by both “My Public Restrictive access rule” and “My Private Permissive access rule”. How come?
The Web proxy is an application filter on top of the firewall engine. It implements its own rule engine which evaluates all web related rules to determine if traffic is allowed or denied.
Traffic from Web Proxy clients enter directly into the Web proxy code, because the Web proxy has listeners on ports 80, 443, and 8080. So only the rule engine of the Web proxy is involved in the evaluation of the policy. Therefore, logging is done by the Web proxy and points to the correct rule.
The story is different for secureNAT clients. Such traffic is first handled by the firewall engine, which runs its rule engine to evaluate the traffic. For Web related traffic, the firewall engine performs only partial evaluation. This is done for optimization, to reduce the resources consumed by the firewall engine. If the firewall engine determines that the traffic may be handled by the Web proxy then it is delivered to the Web proxy and the firewall engine logs the rule where it makes that decision. Then the Web proxy will do a complete evaluation and log the correct rule.
In the above example, the firewall engine makes the decision to delegate full evaluation to the Web proxy when it examines the “My Public Restrictive access rule” rule. This is the wrong rule, but it is enough for the decision in the firewall engine. Later on, the Web proxy will make the final decision and log the final result and the correct policy rule.
More on client types here.
Doron Juster
Senior Development Engineer