Network Load Balancing (NLB) configuration settings in Forefront TMG: to clear or not to clear?
Introduction
Network Load Balancing integration is one of the features that existed in the previous version of Forefront Threat Management Gateway (TMG), Internet Security and Acceleration (ISA) Server 2006. The concept of this functionality is described in Network Load Balancing Integration Concepts for Microsoft Internet Security and Acceleration (ISA) Server 2006. The main idea is that instead of defining NLB settings on each cluster node, cluster settings can be configured on the Forefront TMG Enterprise Manager Server (EMS) or on the array manager, and the EMS or array manager distributes the settings to all array members. After that, the system enters an NLB integrated state, where Forefront TMG detects and overrides any external changes made to the NLB configuration on all array members. For example if Forefront TMG is in an NLB integrated state and someone changes a virtual IP on any array member, the Firewall Service will change it back to the IP that is defined in the array configuration.
However, in ISA Server, after the NLB integration is disabled, the NLB cluster remains configured with the ISA Server settings with corresponding virtual IPs and NLB protocol bindings. This may interfere with future NLB clusters defined not via ISA Server.
NLB Clear
In order to allow the Forefront TMG administrator to have more control over the NLB state, the "NLB Clear" functionality was introduced in Forefront TMG.
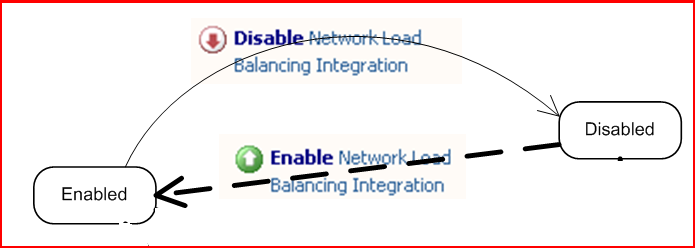
NLB Integration state machine in ISA Server:
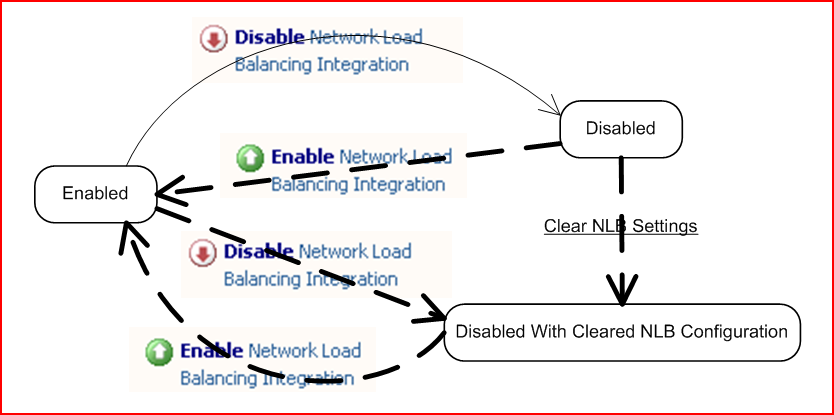
NLB Integration state machine in Forefront TMG:
In Forefront TMG, when the administrator disables NLB integration, the following dialog allows them to select what will be the next state:
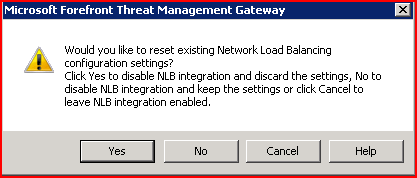
The default option is to discard NLB configuration settings, which includes removing virtual IPs from appropriate NICs, unbinding them from the NLB protocol, and removing all NLB-related settings from the registry. Note that you cannot perform a selective clear of NLB configuration.
When disabling NLB integration via the API, the settings are not cleared by default; this is done for backward compatibility with scripts written for ISA Server. To have the settings removed, you should set the NLBIntegrationClearUponDisable member of the interface IFPCNLBConfiguration2 to TRUE, prior to setting NLBIntegrationEnabled to FALSE.
Alert for NLB configuration removal
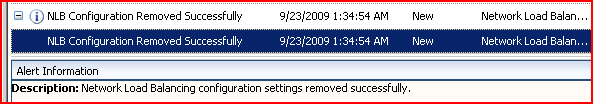
Each time an NLB Clear is successfully performed, the alert above appears in the Alerts pane of the Monitoring node. There is a corresponding alert for a failure to clear the settings. By the way, such an alert is purely informative since the failure doesn't block any other Forefront TMG functionality, but may indicate some NLB-related issues.
Each time that NLB integration is enabled, NLB Clear is automatically called by the Firewall Service and the alert appears.
Individual NLB configuration removal
If the administrator chooses not to remove NLB configuration settings when disabling the integration, it can be done at a later stage. However, since Forefront TMG won't control NLB configuration any longer, the settings will have to be removed for each array member individually. This can be done in two ways: by using a troubleshooting task or by running the NLBClear.exe utility located in the installation directory.
Troubleshooting task:
This task can be run regardless of whether NLB Integration is enabled or disabled.
· If NLB Integration is enabled, the task clears the settings, which are immediately overridden by Forefront TMG according to the stored configuration. This can be used to refresh NLB settings that got corrupted.
· If NLB Integration is disabled, the task just clears all NLB settings.
The task cannot run from a remote management console and operates only on the local array member.
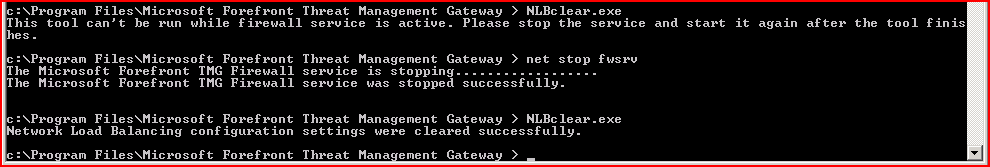
NLBClear.exe
This utility clears NLB settings on the local array member. Note that the Firewall Service has to be stopped before the utility is run.
Dima Datsenko, Software Development Engineer, Forefront Threat Management Gateway
Reviewers: Jonathan Barner and Rachel Adam