TMG Network Inspection System (NIS) – “Attention Required” Feature
Network Inspection System (NIS), the vulnerability signature component of TMG’s Intrusion Prevention System (IPS), offers automatic and manual flagging of specific NIS signatures in TMG UI for future reference. Similar to important or unread emails flagging in outlook, NIS flags specific signatures for the administrator attention.
Manual Flagging for Attention
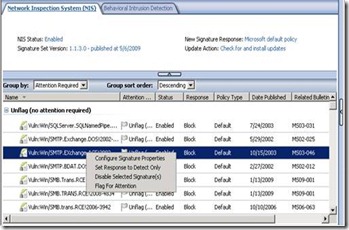
You can flag any signature or group of signatures manually for future reference. All you need to do is to make your selection, right click and choose Flag for Attention.
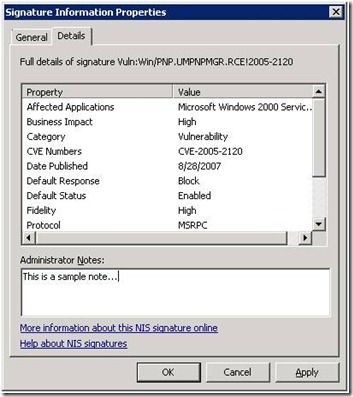
The signature properties dialog can also be used to enter free text with your comments regarding the reason to flag a specific signature for attention.
You can un-flag selected flagged signatures at any time in a similar way.
Automatic Flagging for Attention
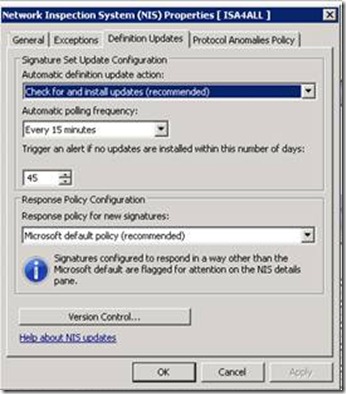
NIS will automatically flag signatures for your attention in the case that the Response Policy for new Signatures is not set to Microsoft Defaults. NIS allows for granular control over new signature setting to comply with different administrators needs.
The following options are offered for Response Policy for new Signatures:
-
- Microsoft default policy (recommended) — select this configuration to accept the default response to the signature.
- Detect only response — select this configuration to record a log entry only when traffic matching this signature is detected.
- No response (disable signature) — select this configuration to take no action and to not record a log entry if traffic matching this signature is detected.
In the case that the Response Policy for new Signatures is not set to Microsoft default (but set to Detect Only or No Response Policy), NIS will flag for attention all new signatures in newly downloaded signature snapshots, to assist in their manual administration and alerts about potential security risks.
Why does NIS automatically flag for attention new signatures with overridden policy?
Microsoft Malware Protection Center (MMPC) sets the recommended signatures policy based on multiple factors including but not limited to the vulnerability, severity and potential business impact. MMPC may change the recommended policy automatically through signature snapshot update, if conditions change.
If you choose to override a Microsoft default response policy through the Response Policy for new signatures, or manually, for instance, by setting a “Block” mode signature to "Detect Only”, NIS will not change the response automatically if the signature response is updated by MMPC; but will flag it for attention.
Once you override a signature default policy you must manually set it back to Microsoft Default to allow for dynamic response policy setting by MMPC.
Best Practices when NIS is not configured with Microsoft Default Configuration
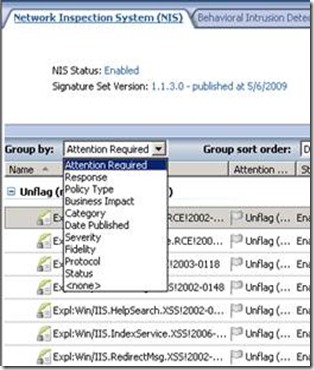
1. Periodically group signatures by “Attention required” and review their policy, preferably setting it to Microsoft Default.
2. In the case that the Response Policy for new Signatures is not set to Microsoft default , periodically group signatures by “Publish Date”. For instance, if you chose to set the response policy of new signatures to “Detect Only“ for a test period, be sure to set them to Microsoft Defaults once finished testing.
3. Periodically group signature by “Policy Type” to review overridden signatures and reconsider setting them back to Microsoft Defaults.
At this point, we would like to emphasize that NIS is designed to minimize administration overhead. Once you operate NIS in recommended default configuration, you will minimize the need for the “Attention Required” feature; it is provided for your choice and convenience.
Author
Moshe Golan, Senior Program Manager – Forefront, GAPA
Reviewers
Avi Ben-Menahem, Principal Group Manager – Forefront, GAPA
Evgeny Ryzhyk, GAPA Senior Development Engineer – Forefront, GAPA
Nathan Bigman, Content Publishing Manager - Forefront